
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Part 1 - API Security Best Practices - Restrict ac...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
divyamary
Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-07-2017
8:17 PM
SAP Cloud Platform, API Management offers many out of the box API Security best practices which can be customized based on your enterprise requirements. These API Security Best Practices includes security policies for Authentication and Authorization, Traffic Management and many more.
Access control policy consists of allowing or denying access of the API to specific client IP or IP ranges. In this blog, we describe how to restrict or limit the access to APIs to only specific client IP ranges.





With this we have activated an API Proxy which connects to the SAP Gateway OData API https://sapes4.sapdevcenter.com/sap/opu/odata/IWBEP/GWSAMPLE_BASIC/ and is accessible to any one on the public domain.
In this section, we would apply the Access control security policy from SAP Cloud Platform, API Management to restrict access of the API to select Client IP ranges.


In the above sample, the default rule is to restrict access to the API and using the MatchRule filter, specific IP ranges are allowed access. Therefore this snippet is a way to achieve IP white listing where in API access is provided to specific client IP ranges.
The mask value enables you to define the IP ranges of the Client IP which have access to the API. In the above sample, in case you would like to allow access to a specific Client IP then mask value should be set to 32 and for allowing access of the API to a client IP address of the range X.X.*.* the mask value should be set to 16.
Another flavor of the restricted access of the API based on client IP address is to have the default rule of allowing accessing to all the Client IP addresses and denying API access to the malicious IP Addresses which is also commonly known as IP black listing. The access control policy sample provided below can be used to achieve this scenario.

A combination of the match rule of Allow/Deny can be used in the Access Control policy. For more such samples refer the help documentation

With this we have restricted the API access to only white listed client IP addresses.


Access control policy consists of allowing or denying access of the API to specific client IP or IP ranges. In this blog, we describe how to restrict or limit the access to APIs to only specific client IP ranges.
More best practices covered in API Security Best Practices blog series.Prerequisites
Create an API Proxy
- Logon to your SAP Cloud Platform, API Management account (say https://account.hanatrial.ondemand.com/cockpit).
- Navigate to the Services tab, search for API Management service tile and click to open SAP API Management service.

- Click on the link Access API Portal to open API Portal.

- Navigate to the Define from the hamburger icon, then select the tab APIs and Click on the Create button

- Create a new API Proxy for any endpoint say GW Sample services (https://sapes4.sapdevcenter.com/sap/opu/odata/IWBEP/GWSAMPLE_BASIC/) from the SAP Gateway ES4 system. Provide the API Proxy details like Proxy name, title, description and base path and click on the Create button

- Click on the Save and Deploy button to activate the API Proxy.

With this we have activated an API Proxy which connects to the SAP Gateway OData API https://sapes4.sapdevcenter.com/sap/opu/odata/IWBEP/GWSAMPLE_BASIC/ and is accessible to any one on the public domain.
Restrict access to the API via Access control
In this section, we would apply the Access control security policy from SAP Cloud Platform, API Management to restrict access of the API to select Client IP ranges.
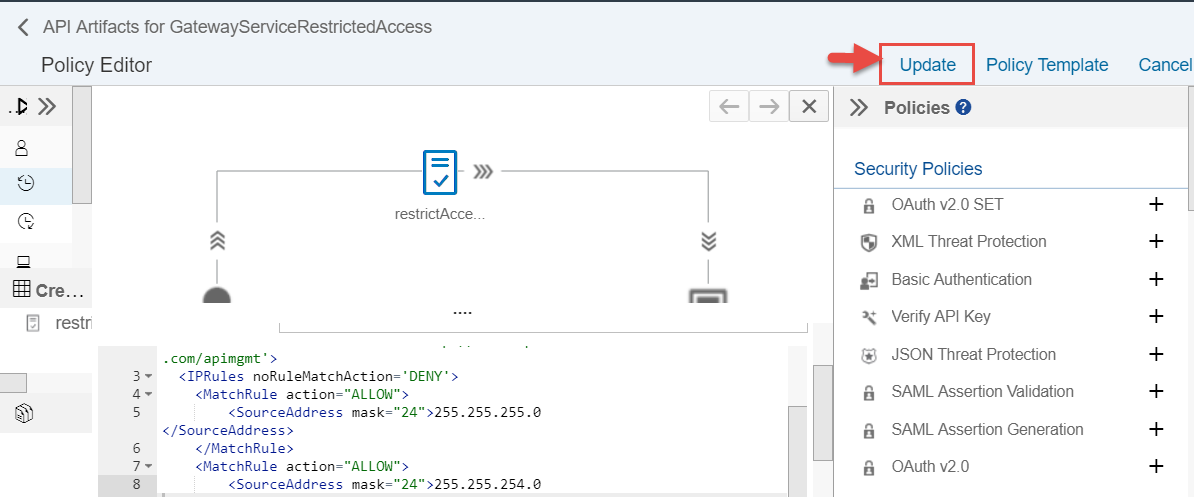
- Click on the Policies button of the newly created API Proxy

- Click on the Edit button from the Policy designer, select PreFlow from the ProxyEndPoint and then click on the + button next to the Access Control Policy available under the Traffic Management Policies segment.

- In the Create Policy dialog, provide the name of the policy say restrictAccess.

- In policy snippet window provide the sample policy provided below. Instead of the IP address of 10.20.30.40 provide a Client IP address to which you would like to provide access of the API.
<AccessControl async='true' continueOnError='false' enabled='true' xmlns='http://www.sap.com/apimgmt'>
<IPRules noRuleMatchAction='DENY'>
<MatchRule action="ALLOW">
<SourceAddress mask="24">10.20.30.40</SourceAddress>
</MatchRule>
<MatchRule action="ALLOW">
<SourceAddress mask="24">20.30.40.50</SourceAddress>
</MatchRule>
</IPRules>
</AccessControl>
In the above sample, the default rule is to restrict access to the API and using the MatchRule filter, specific IP ranges are allowed access. Therefore this snippet is a way to achieve IP white listing where in API access is provided to specific client IP ranges.
The mask value enables you to define the IP ranges of the Client IP which have access to the API. In the above sample, in case you would like to allow access to a specific Client IP then mask value should be set to 32 and for allowing access of the API to a client IP address of the range X.X.*.* the mask value should be set to 16.
Another flavor of the restricted access of the API based on client IP address is to have the default rule of allowing accessing to all the Client IP addresses and denying API access to the malicious IP Addresses which is also commonly known as IP black listing. The access control policy sample provided below can be used to achieve this scenario.
<AccessControl async='true' continueOnError='false' enabled='true' xmlns='http://www.sap.com/apimgmt'>
<IPRules noRuleMatchAction='ALLOW'>
<MatchRule action="DENY">
<SourceAddress mask="24">10.20.30.40</SourceAddress>
</MatchRule>
<MatchRule action="DENY">
<SourceAddress mask="24">20.30.40.50</SourceAddress>
</MatchRule>
</IPRules>
</AccessControl>

A combination of the match rule of Allow/Deny can be used in the Access Control policy. For more such samples refer the help documentation
- Click on the Update button to save the Policy changes

- Click on the Save button to save the changes to API Proxy

With this we have restricted the API access to only white listed client IP addresses.
Finally testing the flow
- Click on the API Proxy URL to open up the API Proxy in a new browser window and this should result in an Access denied error.


Further Reads
- Part 2 – Rate limit API calls with Retry time
- API Security Best Practices
- For more blogs on SAP Cloud Platform API Management visit us at SAP Community
- SAP Managed Tags:
- API Management
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
345 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
427 -
Workload Fluctuations
1
Related Content
- Connection restrictions and their relation to user groups in SAP HANA Cloud, SAP HANA Database in Technology Blogs by SAP
- SAP Datasphere - Space, Data Integration, and Data Modeling Best Practices in Technology Blogs by SAP
- Taking Data Federation to the Next Level: Accessing Remote ABAP CDS View Entities in SAP HANA Cloud in Technology Blogs by SAP
- How to Connect a S/4HANA Cloud Private Edition System to SAP Start in Technology Blogs by SAP
- Partner Innovation - eMudhra's Co-Innovation Journey with SAP in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 41 | |
| 25 | |
| 17 | |
| 14 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |