
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Cloud Platform Security: Safeguarding Your Bus...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Former Member
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-04-2017
11:13 PM

At SAP, we take security seriously. Whether an organization needs to run applications securely through SAP data centers or needs to ensure that applications are securely developed for internal or external use, SAP customers can always be assured that the latest and greatest security measures are upheld. For this post let’s focus specifically on the comprehensive SAP Cloud Platform integrated security services that customers rely upon to securely run and develop applications.
Run Secure
Let’s start with the physical security involved with applications running on the SAP Cloud Platform. Data within these cloud applications no longer resides on-premises within your organization but is stored and run through SAP data centers around the world. SAP data centers are subject to high levels of industry security standards with ISO 27001 certified and SOC1 and SOC2 compliance.

Data backup is physically separated but co-located within the same region as the primary SAP Data Center whenever possible. Your organization’s data is always kept securely separate from other customer data and administrative access to the data is highly restricted. Any data at rest or in transit is securely encrypted to the highest possible standards.
SAP’s Cloud Platform Technical and Organization Measures (TOM) imparts a high level of security and covers all bases with its security patch and malware management, multi-tenancy, access restrictions, business continuity management, disaster recovery, subcontractor compliance, 24 x 7 security monitoring, network security, encryption, policies and standards, strong authentication and access management tool, video and sensor surveillance, intruder alarm systems and so much more.

Develop Secure
SAP offers different security mechanisms for ensuring that only approved users have access to SAP Cloud Platform applications.

Managing Identities
With the SAP Cloud Platform Identity Authentication service, you can provide your employees, customers, and partners with simple and secure cloud-based access to the business processes, applications, and data they need, including two-factor authentication and custom password policy. For authentication and single sign-on, you can choose SAP Cloud Platform Identity Authentication or use your own corporate IdP with identity federation. SAP Cloud Platform also supports social IdPs such as Facebook, Google or LinkedIn for authentication. The social IdP integration will make consumer on-boarding to your cloud applications easily achievable.
User Role Access using SAP Cloud Platform Identity Provisioning
What about the different user roles and departments accessing the SAP Cloud Platform?
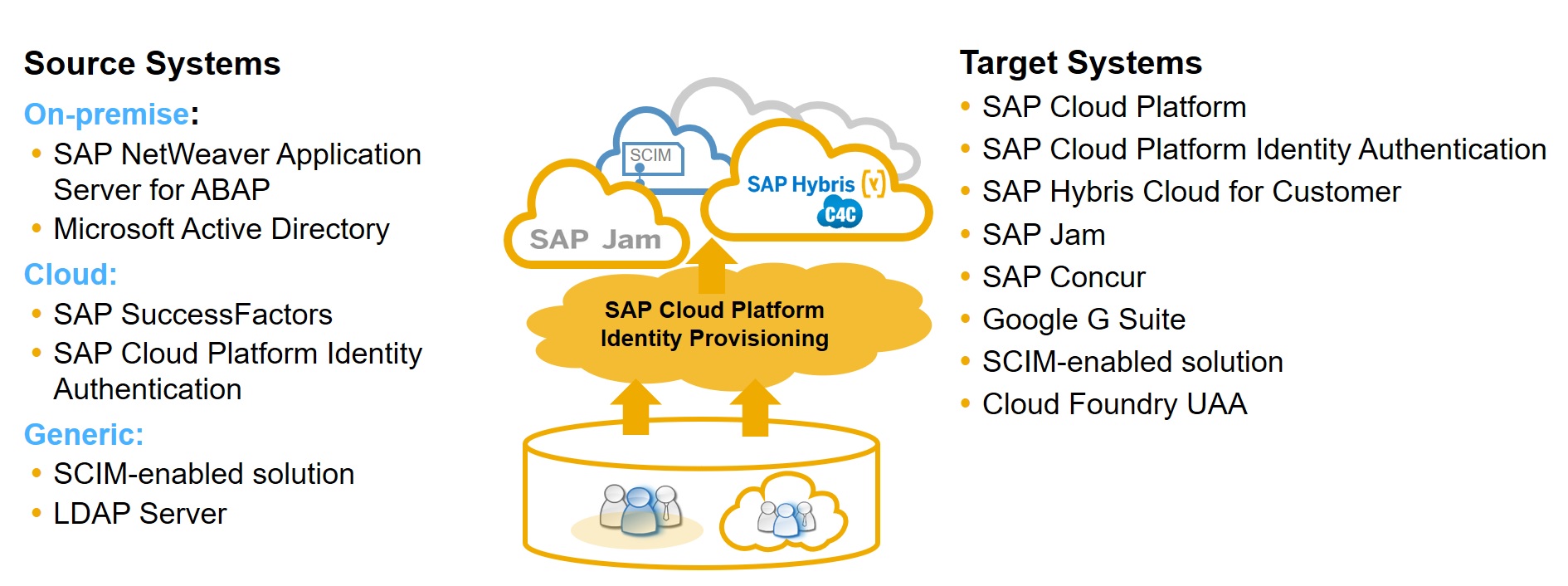
SAP Cloud Platform Identity Provisioning offers a comprehensive, low cost approach to identity lifecycle management in the cloud. Beyond provisioning on-premise or third party cloud users to SAP Cloud applications, customers can also provision the relevant user authorizations to the respective SAP cloud applications during the provisioning process. The is done by defining the access policies before the provisioning process. It maps between your source user groups to your user roles in the cloud.
Furthermore, SAP Cloud Platform supports dynamic role assignment. When the user roles in on-premises or cloud systems change, the SAML user attributes will change immediately. When the user logs into the platform, the new role credentials will be automatically assigned. This ensures, based on a user’s role, that areas of the cloud application and data only relevant to them can be accessed. As a point of note, you can also program user role assignments using platform authorization APIs for a secure and private authorization process.
Authentication and Single Sign-on with OAuth and SAML
OAuth is a security prevention measure that replaces an individual’s username and password with a token – so your access is always protected. OAuth provides clients with a "secure delegated access" to server resources on behalf of a resource owner. SAP Cloud Platform supports the OAuth 2.0 protocol as a reliable way to protect application APIs and resources. How the OAuth flow is staged includes a Security Assertion Markup Language (SAML) 2.0-compliant IdP that authenticates the user and produces an authorization code. The client connects with SAP Cloud Platform OAuth service, where the access token is generated. From there, authentication is evaluated, validated and in-line with service scope.

Beyond the above security services, SAP Cloud Platform also provides a Cloud Identity Access Governance service to help you manage identities and optimize compliance across your enterprise. For example, to achieve SOX compliance for your company.
The Importance of Security
The security architecture of SAP Cloud Platform aims to establish security measures that are among the highest in the industry. At SAP, your data, platform and application security is our top priority regardless of where you are located in the world. Our aim is to consistently safeguard your business.
To read more, please visit SAP Cloud Platform.
- SAP Managed Tags:
- SAP Cloud Identity Services,
- Identity Provisioning,
- Security
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
297 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
343 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
420 -
Workload Fluctuations
1
Related Content
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- What’s new in Mobile development kit client 24.4 in Technology Blogs by SAP
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
- Developing & Deploying the UI5 App to Cloud Foundry and Accessing from App-router End-to-End Steps in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 37 | |
| 25 | |
| 17 | |
| 13 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 |