
- SAP Community
- Groups
- Industry Groups
- SAP for Public Sector
- Blogs
- Interoperability in our Border(less) Society
SAP for Public Sector Blogs
Read and write blog posts showcasing creative initiatives, technology advancements, and success stories in public sector transformation powered by SAP.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member80
Participant
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-15-2017
2:21 PM
The definition of Interopability is –
‘the ability of computer systems or software to exchange and make use of information”
Interoperability in Public Safety and Security has been at the top of the agenda for many years and covers a huge span of requirements at all levels within the security community. There is fundamentally one major challenge preventing us from getting the right information at the right time to deliver the required end result and that is:-
Information Technology and all the supporting paraphernalia was not produced by one manufacturer or one set of standards in one global language. It is broad, huge and very complicated and our Public Security Agencies whether Intelligence, Police or Borders have evolved along with the technology to what we have today and that is a very complex landscape of heterogenous capability that is being challenged by the emergence of a rapid and sophisticated rise in technology.
We must look at the rise of the industry disrupters such as Uber, Tesla and AirBNB as examples. They have disregarded the old-school approach to deliver capability and services on technology utilising Machine Learning, Big Data, Blockchain, Artificial Intelligence, Real Time Intelligence and Situational Awareness that only a few years (or is it months !!) ago we could have hardly imagined.

To move the needle forward quickly Public Security Agencies will need to optimise their existing assets. Provide immediate and extended value on those assets and innovate as a series of parallel rapid sprints.
On the dark side there is a tirade of threats from serious organised crime and terrorism, these people have also disregarded the past and embraced all aspects of the current and future but without the burden of legacy, budget constraint and procurement processes
Commissioner for the Security Union Julian King said: "The recent tragic attacks in Europe have highlighted the importance of effective information sharing between Member State authorities. The approach we are outlining today sets out a targeted and intelligent way of using the existing data to best effect. What we propose would be a step-change in the way we manage data for security, helping national authorities better addressing transnational threats and detecting terrorists who act across borders."
It means today we are under an unprecedented and disruptive threat that our governments must deal with as a matter of urgency. We exist to thrive and prosper whilst taking care of ourselves and our family and fellow citizens in a securely governed, fair and tolerant society.
Border Management is at the epicentre
The challenge is identifying the threats whilst maintaining the rights and privileges of those legitimately traveling or moving goods and services across the physical borders in what is becoming an increasingly borderless world. Physical borders will always exist and will be managed by people but only with the collaboration of technology will we get the interopability required at all levels and across all organisations to fight the threat
Commissioner for Migration, Home Affairs and Citizenship Dimitris Avramopoulos said: "The value of our security information is maximised when our systems talk to each other. The complex and fragmented systems we have today make us vulnerable. Actionable information is not always available for the law enforcement officials that need it. Today, we present a clear vision on how to act to correct this. To connect the dots and to eliminate blind spots to step up the security of our citizens across the EU."
The aim of public security agencies today is to establish a strategic crisis-prevention, response, and recovery system that can collect, process, and analyze the information necessary for executive decision making. It defines a centralised command with distributed operational networks capable of providing decision guidance to the appropriate agents. It integrates data from open sources and social media with classified reporting systems for a full contextual picture of threats to public security.
The objective is to start with a set of common attributes and phases that can be described by data and held in open-source and public security stakeholder information systems. Next is to identify the information needs of each stake-holder and initiate legal discussions – per region and country – on how to combine information streams lawfully. The fruit of this labor is to provide frontline border officers, police and intelligence officers with exactly the information they require to apply their resources in real time effectively. The source is just-in-time information streaming in from fused intelligence, which generates structured reports from signals triggered in unstructured data. In other words the source is providing what is seen as a Common Identity Repository which must in most cases provide a real time capability whilst respecting the requirements of the data-protection safeguards in place. In the case of the EU requirements this must provide: -
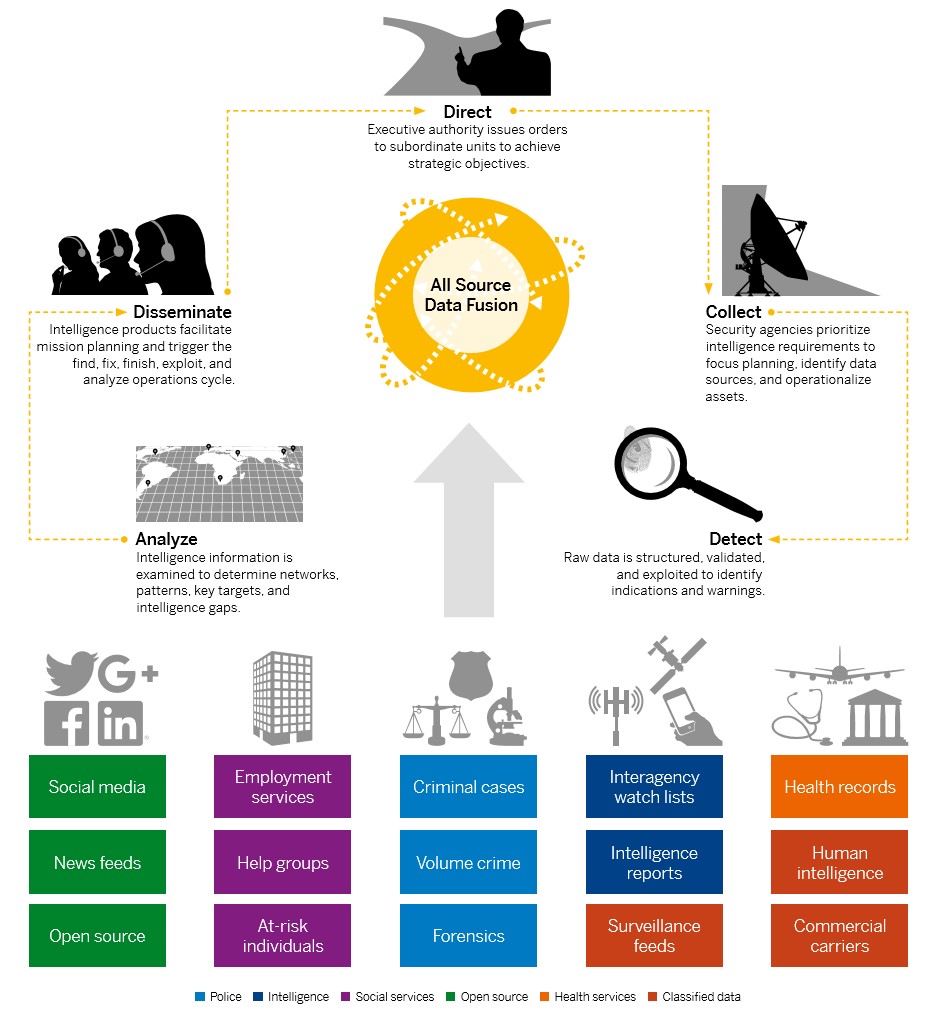
An intelligence picture starts to emerge from the interoperable data, particularly with the element of time, which correlates events for additional fidelity and understanding of behavior patterns. The threat model can start to be refined based on investigations of false positives, machine learning, and new rules integrated into the event processing and preparation tools. In terms of the traditional “direct, collect, analyze, and disseminate intelligence” cycle, we now have a detection step that assists analysts who advise decision makers on how to respond and apply resources
The key elements of such a structure would be:-
Interoperability must mean that there is a smooth path to communicate and collaborate across all channels to all parties in real time whilst utilizing every aspect of the legacy environment using modern technology to turn it into a future focused adaptable platform to fight what will be a constant threat.
We need to not only keep up with the bad people but close the space in where they operate by providing the right information at the right time for it to be correctly analysed and enacted upon in real time.
For more information and points of view on the impact of digital transformation on the wider Public Sector visit our website.
‘the ability of computer systems or software to exchange and make use of information”
Interoperability in Public Safety and Security has been at the top of the agenda for many years and covers a huge span of requirements at all levels within the security community. There is fundamentally one major challenge preventing us from getting the right information at the right time to deliver the required end result and that is:-
COLLABORATION
Information Technology and all the supporting paraphernalia was not produced by one manufacturer or one set of standards in one global language. It is broad, huge and very complicated and our Public Security Agencies whether Intelligence, Police or Borders have evolved along with the technology to what we have today and that is a very complex landscape of heterogenous capability that is being challenged by the emergence of a rapid and sophisticated rise in technology.
We must look at the rise of the industry disrupters such as Uber, Tesla and AirBNB as examples. They have disregarded the old-school approach to deliver capability and services on technology utilising Machine Learning, Big Data, Blockchain, Artificial Intelligence, Real Time Intelligence and Situational Awareness that only a few years (or is it months !!) ago we could have hardly imagined.

To move the needle forward quickly Public Security Agencies will need to optimise their existing assets. Provide immediate and extended value on those assets and innovate as a series of parallel rapid sprints.
On the dark side there is a tirade of threats from serious organised crime and terrorism, these people have also disregarded the past and embraced all aspects of the current and future but without the burden of legacy, budget constraint and procurement processes
Commissioner for the Security Union Julian King said: "The recent tragic attacks in Europe have highlighted the importance of effective information sharing between Member State authorities. The approach we are outlining today sets out a targeted and intelligent way of using the existing data to best effect. What we propose would be a step-change in the way we manage data for security, helping national authorities better addressing transnational threats and detecting terrorists who act across borders."
It means today we are under an unprecedented and disruptive threat that our governments must deal with as a matter of urgency. We exist to thrive and prosper whilst taking care of ourselves and our family and fellow citizens in a securely governed, fair and tolerant society.
Border Management is at the epicentre
The challenge is identifying the threats whilst maintaining the rights and privileges of those legitimately traveling or moving goods and services across the physical borders in what is becoming an increasingly borderless world. Physical borders will always exist and will be managed by people but only with the collaboration of technology will we get the interopability required at all levels and across all organisations to fight the threat
- The EU has 1000 external Customs Border Posts
- Over 5000 Organised crime groups in the EU
- Tax Evasion and Avoidance cross borders costs the EU 1000 Billion a year through illicit goods
- Drug trafficking is worth USD 320-344 billion worldwide
- The Belgian bomb attack cost over 1 Billion in lost revenue (but what cost a life!)
- Da’esh had financial assets worth more than two trillion USD and an estimated annual income of USD 2.9 billion
- 66% of people who travelled to Syria to fight with Da’esh from Germany were known to police
No one authority worldwide has a unified or single view of the movement of illicit trade or Criminal/Terror related activity and the lines between these who pose this threat are well and truly blurred.
At no time before has the need for a more collaborative and adaptable approach required.
Commissioner for Migration, Home Affairs and Citizenship Dimitris Avramopoulos said: "The value of our security information is maximised when our systems talk to each other. The complex and fragmented systems we have today make us vulnerable. Actionable information is not always available for the law enforcement officials that need it. Today, we present a clear vision on how to act to correct this. To connect the dots and to eliminate blind spots to step up the security of our citizens across the EU."
The aim of public security agencies today is to establish a strategic crisis-prevention, response, and recovery system that can collect, process, and analyze the information necessary for executive decision making. It defines a centralised command with distributed operational networks capable of providing decision guidance to the appropriate agents. It integrates data from open sources and social media with classified reporting systems for a full contextual picture of threats to public security.
The objective is to start with a set of common attributes and phases that can be described by data and held in open-source and public security stakeholder information systems. Next is to identify the information needs of each stake-holder and initiate legal discussions – per region and country – on how to combine information streams lawfully. The fruit of this labor is to provide frontline border officers, police and intelligence officers with exactly the information they require to apply their resources in real time effectively. The source is just-in-time information streaming in from fused intelligence, which generates structured reports from signals triggered in unstructured data. In other words the source is providing what is seen as a Common Identity Repository which must in most cases provide a real time capability whilst respecting the requirements of the data-protection safeguards in place. In the case of the EU requirements this must provide: -
- Aggregated view of identify from multiple systems
- Security of the ownership of data from the original systems
- Access rights
- Anonymous existence of data on a hit/no-hit basis
An intelligence picture starts to emerge from the interoperable data, particularly with the element of time, which correlates events for additional fidelity and understanding of behavior patterns. The threat model can start to be refined based on investigations of false positives, machine learning, and new rules integrated into the event processing and preparation tools. In terms of the traditional “direct, collect, analyze, and disseminate intelligence” cycle, we now have a detection step that assists analysts who advise decision makers on how to respond and apply resources

The Intelligence Interoperability Model
The key elements of such a structure would be:-
- A single version of the truth – in other words a repository of data using a common data model such as NIEMS or in the EU – UMF (Unified Message Format) for the exchange of data between member state systems
- A single search capability across all information systems – Existing - In respect to the EU this would-be SIS (Schengen Information System), Eurodac, PRUM and VIS (Visa Information System) and new – ETIAS, ECRIS-TCN, EES and PNR
- Adaptable and future focused for facilitating all new technology innovation
- Data Privacy by Design respecting the rights of the Citizen and traveler
- Advanced and shared Biometric Service
- Data Access – Multiple stakeholders, cross government and cross border – Governance, Risk and Compliance
- Data Quality – Multiple and legacy data needs to be rationalised to get to a common identity
Interoperability must mean that there is a smooth path to communicate and collaborate across all channels to all parties in real time whilst utilizing every aspect of the legacy environment using modern technology to turn it into a future focused adaptable platform to fight what will be a constant threat.
We need to not only keep up with the bad people but close the space in where they operate by providing the right information at the right time for it to be correctly analysed and enacted upon in real time.
Interoperability is at the heart of the border management mission
For more information and points of view on the impact of digital transformation on the wider Public Sector visit our website.
- SAP Managed Tags:
- Public Sector
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.