
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Trusted X509 Authentication Support in SAP Busines...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
vishal_mour
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-06-2017
5:11 PM
This is the second part of the blog series on how to achieve X509
authentication for REST SDK. In the first blog I have provided the steps for
certificate and keystore generation. In this post I will provide the steps needed to configure WACS (which hosts RESTful web-services ) and how to
resolve the errors reported by browsers
Step 1: Logon to CMC, and navigate to Servers -> WACS. Maintain the keystore details generated earlier under the properties as shown below:

Restart WACS.
Step 2: Navigate to CMC-> Authentication -> Enterprise

Unable the Trusted Authentication checkbox, maintain validity period.
Update the setting and download the Shared Secret

Copy the downloaded conf file in the path:
<Install Dir>/SAP BusinessObjects/SAP BusinessObjects Enterprise XI 4.0/java/pjs/container/bin/
And restart WACS
Step 3: Need to make sure the user account through which I want to X509 based trusted authentication exists in the BusinessObejcts Platform.
Example for my use case, the X509 certificate is in name of TestUser1

Step 4: Try to access the below url in your browser to achieve Trusted Authentication based on X509 certificate using REST SDK:
https://<hostname>:<ip>/biprws/logon/v1/logon/trustedx509
with the above configuration, url looks like: .
https://targetmachine/biprws/v1/logon/trustedx509
In case everything is fine, it should generate the logon token directly or it will ask to select the user certificate see below. In case of error refer next steps
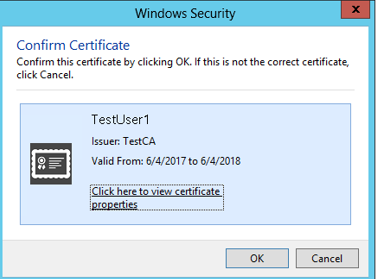
And it will login with that user account. In my case: TestUser1

Step 5: In case browser displays the following error:
The security certificate presented by this website was not issued by a trusted certificate authority.
Perform this step mentioned below or moved to next step

This error indicates that browser does not trust the signing authority of the server certificate. To bypass this error, upload the server CA certificate to browsers Trusted Certificate Authority list.
Go to Internet Explorer ->Settings -> Internet options
Navigate to content tab and select Certificates.

Navigate to Trusted Root Certificate Authority Tab and select Import

Click on Browse and select the CA certificate created earlier:

Select Next, Next, Finish. And when it gives a confirmation window to install certificate. Select yes.
Note: You should not install certificates from unknown sources to your Trusted Root Certificate List, it may lead to security issues.
Try to access the below url in your browser: https://<hostname>:<ip>/biprws/logon/v1/logon/long
with the above configuration, url looks like:
https://targetmachine/biprws/v1/logon/long
If everything is fine it should display something like below and then go back to step 4. In case there are errors go to next step.

Step 6: In case browser displays the following error:


This error indicates that the required client/ user certificate in not present in your certificate store.
Go to Internet Explorer ->Settings -> Internet options
Navigate to content tab and select Certificates.

Navigate to Personal tab and click on import
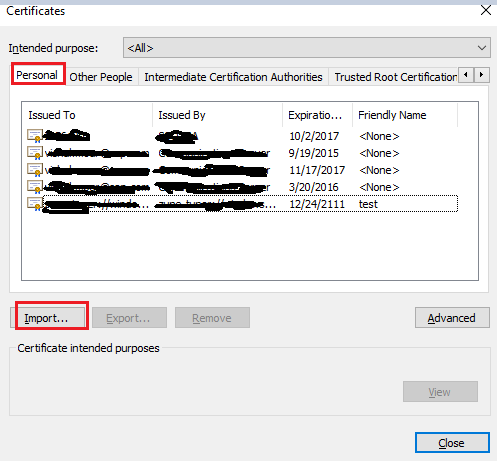
Click on browse and select the client/ user certificate created earlier

Click on Next and provide the Private Key Password of the certificate
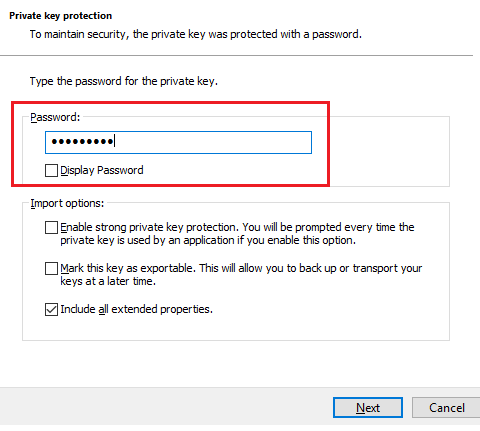
Do next, next and finish. This will successfully import the user certificate in your certificate store.

Try to access the below url in your browser: https://<hostname>:<ip>/biprws/logon/v1/logon/long
with the above configuration, url looks like:
https://targetmachine/biprws/v1/logon/long
If everything is fine it should display something like below and then go back to step 4

authentication for REST SDK. In the first blog I have provided the steps for
certificate and keystore generation. In this post I will provide the steps needed to configure WACS (which hosts RESTful web-services ) and how to
resolve the errors reported by browsers
Note: We have tested 2 Factor Authentication login for BIL with the same approach. As long as the 2nd Factor returns a Valid X509 certificate of a user, and the certificate is available in Windows Certificate Store, user can same the same certificate for login
Step 1: Logon to CMC, and navigate to Servers -> WACS. Maintain the keystore details generated earlier under the properties as shown below:

Restart WACS.
Step 2: Navigate to CMC-> Authentication -> Enterprise

Unable the Trusted Authentication checkbox, maintain validity period.
Update the setting and download the Shared Secret

Copy the downloaded conf file in the path:
<Install Dir>/SAP BusinessObjects/SAP BusinessObjects Enterprise XI 4.0/java/pjs/container/bin/
And restart WACS
Step 3: Need to make sure the user account through which I want to X509 based trusted authentication exists in the BusinessObejcts Platform.
Example for my use case, the X509 certificate is in name of TestUser1

Step 4: Try to access the below url in your browser to achieve Trusted Authentication based on X509 certificate using REST SDK:
https://<hostname>:<ip>/biprws/logon/v1/logon/trustedx509
with the above configuration, url looks like: .
https://targetmachine/biprws/v1/logon/trustedx509
In case everything is fine, it should generate the logon token directly or it will ask to select the user certificate see below. In case of error refer next steps

And it will login with that user account. In my case: TestUser1

Step 5: In case browser displays the following error:
The security certificate presented by this website was not issued by a trusted certificate authority.
Perform this step mentioned below or moved to next step

This error indicates that browser does not trust the signing authority of the server certificate. To bypass this error, upload the server CA certificate to browsers Trusted Certificate Authority list.
Go to Internet Explorer ->Settings -> Internet options
Navigate to content tab and select Certificates.

Navigate to Trusted Root Certificate Authority Tab and select Import

Click on Browse and select the CA certificate created earlier:

Select Next, Next, Finish. And when it gives a confirmation window to install certificate. Select yes.
Note: You should not install certificates from unknown sources to your Trusted Root Certificate List, it may lead to security issues.
Try to access the below url in your browser: https://<hostname>:<ip>/biprws/logon/v1/logon/long
with the above configuration, url looks like:
https://targetmachine/biprws/v1/logon/long
If everything is fine it should display something like below and then go back to step 4. In case there are errors go to next step.

Step 6: In case browser displays the following error:


This error indicates that the required client/ user certificate in not present in your certificate store.
Go to Internet Explorer ->Settings -> Internet options
Navigate to content tab and select Certificates.

Navigate to Personal tab and click on import

Click on browse and select the client/ user certificate created earlier

Click on Next and provide the Private Key Password of the certificate

Do next, next and finish. This will successfully import the user certificate in your certificate store.

Try to access the below url in your browser: https://<hostname>:<ip>/biprws/logon/v1/logon/long
with the above configuration, url looks like:
https://targetmachine/biprws/v1/logon/long
If everything is fine it should display something like below and then go back to step 4

- SAP Managed Tags:
- SAP BusinessObjects Business Intelligence platform
10 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
416 -
Workload Fluctuations
1
Related Content
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
- Configure Custom SAP IAS tenant with SAP BTP Kyma runtime environment in Technology Blogs by SAP
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Crystal Reports text clipping issue. PDF created by Business Obj on Red Hat Enterprise Linux (RHEL) in Technology Q&A
Top kudoed authors
| User | Count |
|---|---|
| 31 | |
| 24 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |