
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Using Roles to Keep Data Secure in SAP IT Operatio...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-21-2017
11:22 PM
Nowadays, IT security is at the forefront of everyone’s minds. With sensational stories about hackers and ransomware dominating news cycles, it's no wonder everyone is focused on keeping their personal data secure. But what about preventing unauthorized access to enterprise software data?
Companies are held to a high standard by both the public and external compliance requirements, with IT security playing an important role in meeting those expectations. Though the SAP IT Operations Analytics (SAP ITOA) User's Guide outlines securing the browser, communication with adapters, and the SAP HANA connection, today we’ll focus on how SAP ITOA handles security on an individual user level.
Fundamental SAP HANA Security
SAP ITOA began as a co-innovation project between SAP’s IT department and the SAP HANA development team, making SAP ITOA a HANA-native application. As a result, all of the security features that are part of SAP HANA are also built into SAP ITOA.
For example, SAP HANA differentiates users based on the roles, or collection of privileges, they have been assigned within the database. These privileges could be related to the underlying system, objects such as tables and schemas, or access to specific applications. This allows administrators to ensure that only authorized users have access to privileged information, creating a system of security layers within the IT architecture. As SAP ITOA sits on top of SAP HANA, these security features cannot be overruled and must be taken into consideration when designing your SAP ITOA implementation.
Predefined SAP ITOA Roles
In addition to the roles related to SAP HANA, SAP ITOA has its own set of predefined roles that can be assigned to users:
Users assigned the Admin role can create and delete any data container, known in SAP ITOA as "buckets", as well as edit bucket configuration and grant other users access. These privileges are extended to all objects associated with buckets such as dashboards, custom rules for additional attributes, alert definitions, prediction dashboards, and stories. As the Admin role has full access to the SAP ITOA system and can therefore setup, install, and configure SAP ITOA, these roles are typically assigned to the SAP ITOA administrator.
Users with the Expert role can create buckets and as creator, retain admin privileges for those buckets and all associated objects. Experts can also be granted permissions for additional buckets and related objects at the application level by an SAP ITOA Admin user. The ability for Experts to be granted permissions means a user can have different permissions for different buckets and associated objects. Experts can be thought of as content creators – users that create stories, dashboards, alerts, and other functional pieces of the SAP ITOA environment.
The last type of role available in SAP ITOA is the Viewer, who can be granted permissions for one or more buckets, and associated objects, by both Admin and Expert users. Users with a Viewer role cannot change or edit buckets, but since different permissions can be extended for different buckets, the same user may be granted an Expert role for some buckets while only being a Viewer for others. A typical SAP ITOA Viewer would be a manager that needs access to dashboards to know what’s going on but doesn’t necessarily understand how SAP ITOA is configured so you’d rather not have them change anything in the system. You know the type.
By assigning different roles to different users, SAP ITOA administrators can control who has access to what information within an IT department. These designations increase the number of security layers so that unauthorized parties do not immediately gain access to all the information contained within SAP ITOA.
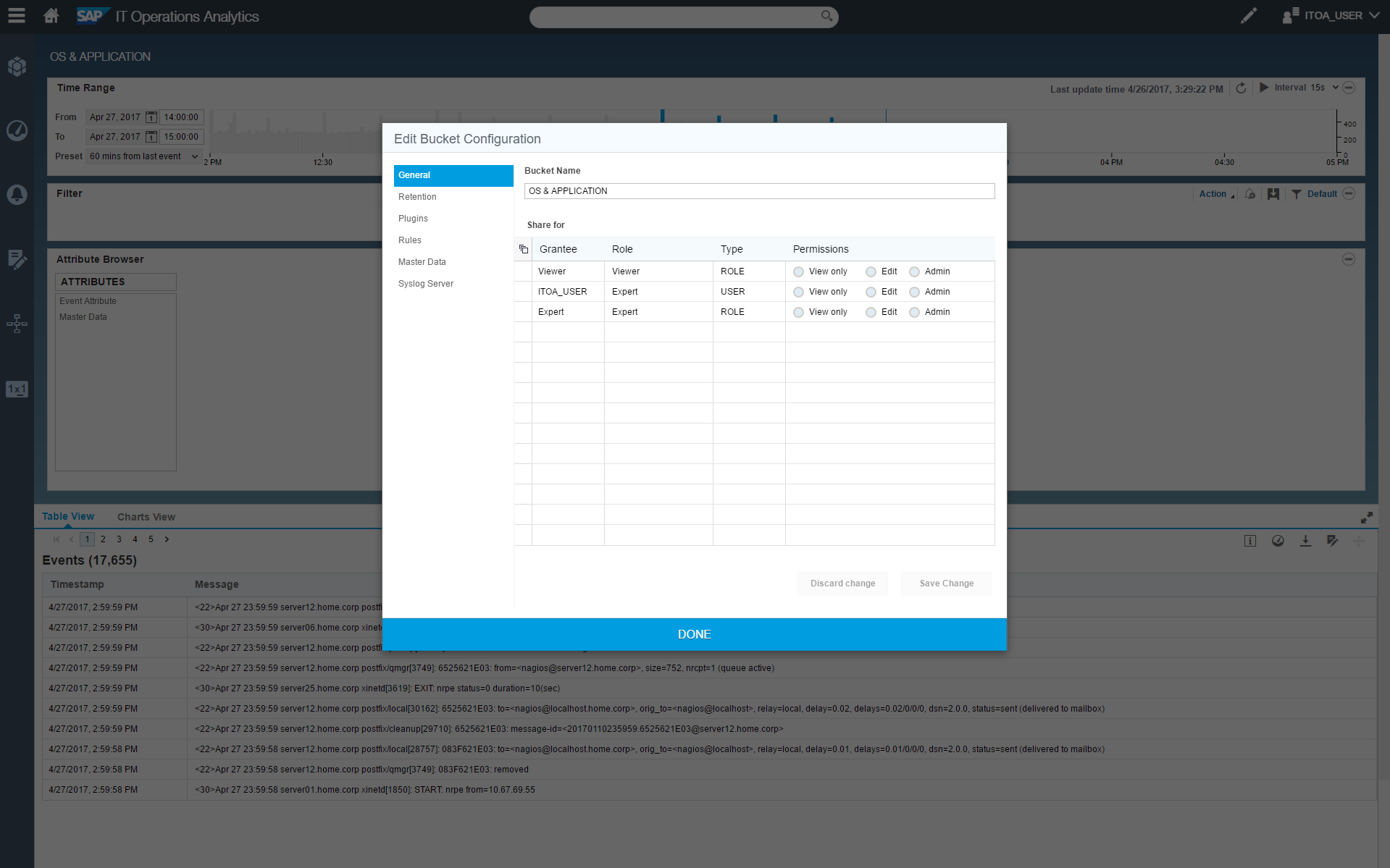
A screenshot showing the different roles for users of a bucket and how easy it is to assign or change permissions in SAP ITOA.
Permissions for SAP ITOA Objects
Though SAP ITOA offers three roles out of the box, more granularity may be required for some organizations. Using custom roles created in SAP HANA, permissions can be granted to groups of users for different SAP ITOA objects such as buckets, dashboards, and stories. These groupings can be as large as a regional division, like North America, or as small as a single person working on a specific area of the data center. With these custom roles, you can support all users from the CIO who needs access to all data for their high-level dashboards down to the intern who is only allowed to work on specific databases.
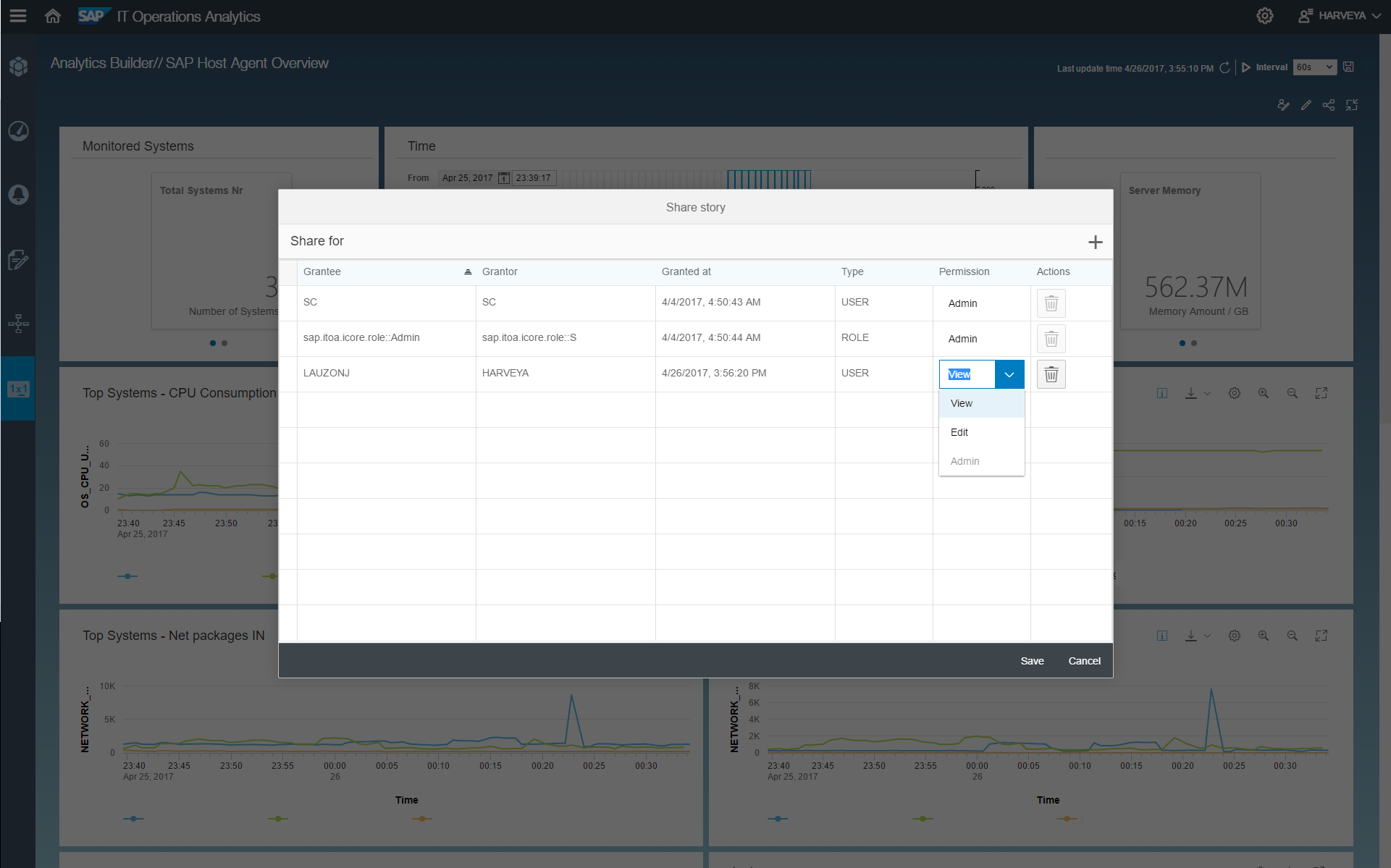
A screenshot showing how to grant permissions for a specific object in SAP ITOA, in this case a story.
Breaking Down Silos to Build Up Walls
I know what you’re thinking: the whole point of SAP ITOA is to break down silos and gain a holistic view of the IT landscape but now we’re building the walls back up from within! With the combination of predefined and custom roles available to users of SAP ITOA, the administrator is easily able to control which users can view or edit buckets. To illustrate this point, let’s consider a situation with network administrator Jane.
As a network administrator, Jane needs access to all the relevant network data within SAP ITOA and is consequently assigned an Expert role for the network bucket. However, Jane needs to be able to access data in other buckets, such as compute and storage, when investigating the root cause of an issue. Therefore, Jane is assigned a Viewer role for the compute and storage buckets, giving her a clear path of site into other areas of the data center so that she may find the root cause efficiently.
If the issue originated in the network, Jane has the access required to fix the issue herself and set up alerts or automatic actions within the network bucket to prevent the issue from happening in the future. If she discovers the issue was initiated from a storage server, she can alert her colleagues that have Expert roles for the storage bucket so they can take over the process.
With the range of predefined and custom roles available, it is easy to see how SAP ITOA breaks down silos to give a holistic view of the IT landscape without compromising security. By using the Expert and Viewer roles, as well as making specific objects available to custom groupings, SAP ITOA users can access the data they need from across the data center while administrators rest assured that no one can perform nefarious actions on the entire system.
Companies are held to a high standard by both the public and external compliance requirements, with IT security playing an important role in meeting those expectations. Though the SAP IT Operations Analytics (SAP ITOA) User's Guide outlines securing the browser, communication with adapters, and the SAP HANA connection, today we’ll focus on how SAP ITOA handles security on an individual user level.
Fundamental SAP HANA Security
SAP ITOA began as a co-innovation project between SAP’s IT department and the SAP HANA development team, making SAP ITOA a HANA-native application. As a result, all of the security features that are part of SAP HANA are also built into SAP ITOA.
For example, SAP HANA differentiates users based on the roles, or collection of privileges, they have been assigned within the database. These privileges could be related to the underlying system, objects such as tables and schemas, or access to specific applications. This allows administrators to ensure that only authorized users have access to privileged information, creating a system of security layers within the IT architecture. As SAP ITOA sits on top of SAP HANA, these security features cannot be overruled and must be taken into consideration when designing your SAP ITOA implementation.
Predefined SAP ITOA Roles
In addition to the roles related to SAP HANA, SAP ITOA has its own set of predefined roles that can be assigned to users:
- Admin (SAP ITOA System Administration)
- Expert (Content Management)
- Viewer (Consumer)
Users assigned the Admin role can create and delete any data container, known in SAP ITOA as "buckets", as well as edit bucket configuration and grant other users access. These privileges are extended to all objects associated with buckets such as dashboards, custom rules for additional attributes, alert definitions, prediction dashboards, and stories. As the Admin role has full access to the SAP ITOA system and can therefore setup, install, and configure SAP ITOA, these roles are typically assigned to the SAP ITOA administrator.
Users with the Expert role can create buckets and as creator, retain admin privileges for those buckets and all associated objects. Experts can also be granted permissions for additional buckets and related objects at the application level by an SAP ITOA Admin user. The ability for Experts to be granted permissions means a user can have different permissions for different buckets and associated objects. Experts can be thought of as content creators – users that create stories, dashboards, alerts, and other functional pieces of the SAP ITOA environment.
The last type of role available in SAP ITOA is the Viewer, who can be granted permissions for one or more buckets, and associated objects, by both Admin and Expert users. Users with a Viewer role cannot change or edit buckets, but since different permissions can be extended for different buckets, the same user may be granted an Expert role for some buckets while only being a Viewer for others. A typical SAP ITOA Viewer would be a manager that needs access to dashboards to know what’s going on but doesn’t necessarily understand how SAP ITOA is configured so you’d rather not have them change anything in the system. You know the type.
By assigning different roles to different users, SAP ITOA administrators can control who has access to what information within an IT department. These designations increase the number of security layers so that unauthorized parties do not immediately gain access to all the information contained within SAP ITOA.

A screenshot showing the different roles for users of a bucket and how easy it is to assign or change permissions in SAP ITOA.
Permissions for SAP ITOA Objects
Though SAP ITOA offers three roles out of the box, more granularity may be required for some organizations. Using custom roles created in SAP HANA, permissions can be granted to groups of users for different SAP ITOA objects such as buckets, dashboards, and stories. These groupings can be as large as a regional division, like North America, or as small as a single person working on a specific area of the data center. With these custom roles, you can support all users from the CIO who needs access to all data for their high-level dashboards down to the intern who is only allowed to work on specific databases.

A screenshot showing how to grant permissions for a specific object in SAP ITOA, in this case a story.
Breaking Down Silos to Build Up Walls
I know what you’re thinking: the whole point of SAP ITOA is to break down silos and gain a holistic view of the IT landscape but now we’re building the walls back up from within! With the combination of predefined and custom roles available to users of SAP ITOA, the administrator is easily able to control which users can view or edit buckets. To illustrate this point, let’s consider a situation with network administrator Jane.
As a network administrator, Jane needs access to all the relevant network data within SAP ITOA and is consequently assigned an Expert role for the network bucket. However, Jane needs to be able to access data in other buckets, such as compute and storage, when investigating the root cause of an issue. Therefore, Jane is assigned a Viewer role for the compute and storage buckets, giving her a clear path of site into other areas of the data center so that she may find the root cause efficiently.
If the issue originated in the network, Jane has the access required to fix the issue herself and set up alerts or automatic actions within the network bucket to prevent the issue from happening in the future. If she discovers the issue was initiated from a storage server, she can alert her colleagues that have Expert roles for the storage bucket so they can take over the process.
With the range of predefined and custom roles available, it is easy to see how SAP ITOA breaks down silos to give a holistic view of the IT landscape without compromising security. By using the Expert and Viewer roles, as well as making specific objects available to custom groupings, SAP ITOA users can access the data they need from across the data center while administrators rest assured that no one can perform nefarious actions on the entire system.
- SAP Managed Tags:
- SAP Sapphire,
- SAP IT Operations Analytics
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
324 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
402 -
Workload Fluctuations
1
Related Content
- 10+ ways to reshape your SAP landscape with SAP BTP - Blog 4 Interview in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform – Blog 4 in Technology Blogs by SAP
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Cloud Integration: Manually Sign / Verify XML payload based on XML Signature Standard in Technology Blogs by SAP
- Trustable AI thanks to - SAP AI Core & SAP HANA Cloud & SAP S/4HANA & Enterprise Blockchain 🚀 in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 | |
| 4 |