
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Getting Started with Kapsel – Part 8 — AuthProxy(S...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-17-2017
5:59 PM
Previous Home Next
The AuthProxy plugin in combination with the Logon plugin handles authentication challenges both in the regular WebView on iOS, the WebView on Android and in Android Crosswalk. It will automatically handle basic authentication and display a certificate selection dialog for X 509 certificate challenges. It stores previously entered credentials in the Logon plugin's secure data vault and will use those when requests for credentials occur in the future.
When an app needs to provide a certificate to the server to identify itself this is known as client authentication or mutual authentication. An example of this is if you are required to provide a client certificate as part of the onboarding process to register with an application or perhaps to access an OData provider (not needed to complete the example). This occurs mostly in Business to Business (B2B) applications. This is different from most business to consumer or B2C websites where it is only the server that authenticates itself to the client with a certificate that has been signed by a certificate authority (CA) such as an online banking site.
For additional details on the AuthProxy plugin see C:\SAP\MobileSDK3\KapselSDK\docs\api\sap.AuthProxy.html or Using the AuthProxy Plugin.
The following steps will demonstrate what happens when a request is sent that does not contain credentials or contains incorrect ones to a backend OData endpoint and how this behavior can be improved with the AuthProxy plugin.
Note that the AuthProxy plugin only handles basic authentication challenges and not form based challenges. Handling of form based challenges may be a new feature of the Fiori Client in SP 15.
Previous Home Next
The AuthProxy plugin in combination with the Logon plugin handles authentication challenges both in the regular WebView on iOS, the WebView on Android and in Android Crosswalk. It will automatically handle basic authentication and display a certificate selection dialog for X 509 certificate challenges. It stores previously entered credentials in the Logon plugin's secure data vault and will use those when requests for credentials occur in the future.
When an app needs to provide a certificate to the server to identify itself this is known as client authentication or mutual authentication. An example of this is if you are required to provide a client certificate as part of the onboarding process to register with an application or perhaps to access an OData provider (not needed to complete the example). This occurs mostly in Business to Business (B2B) applications. This is different from most business to consumer or B2C websites where it is only the server that authenticates itself to the client with a certificate that has been signed by a certificate authority (CA) such as an online banking site.
For additional details on the AuthProxy plugin see C:\SAP\MobileSDK3\KapselSDK\docs\api\sap.AuthProxy.html or Using the AuthProxy Plugin.
Handling Authentication Challenges
The following steps will demonstrate what happens when a request is sent that does not contain credentials or contains incorrect ones to a backend OData endpoint and how this behavior can be improved with the AuthProxy plugin.
Note that the AuthProxy plugin only handles basic authentication challenges and not form based challenges. Handling of form based challenges may be a new feature of the Fiori Client in SP 15.
- Modify the sample from the Logon Plugin section.
In index.html, add the following buttons below the Unlock button.
<button id="chgPwd" onclick="sap.Logon.changePassword(logonSuccessCallback, errorCallback)">Change Password</button>
<button id="clearCreds" onclick="sap.AuthProxy.clearClientCertPreferences(clearClientCertSuccessCallback, clearClientCertErrorCallback)">Clear Certs</button>
Also add the following two methods.
function clearClientCertSuccessCallback() {
console.log("EventLogging: clearClientCertSuccessCallback");
}
function clearClientCertErrorCallback(error) {
console.log("EventLogging: clearClientCertErrorCallback " + JSON.stringify(result));
}
- Edit C:\Kapsel_Projects\LogonDemo\config.xml and add the following setting. The below settings when set to false disables the handling of authentication challenges by the AuthProxy plugin.
<platform name="android">
<preference name="SAPKapselHandleBasicAuthChallenges" value="false" />
<preference name="SAPKapselHandleX509Challenges" value="false" />
...
</platform>
<platform name="ios">
<preference name="SAPKapselHandleHttpRequests" value="false" />
...
</platform>
- Note that there is a method that can change the stored password called sap.Logon.changePassword(). This is not really needed though as when 401 authentication challenge occurs and the user enters the correct credentials they are then saved. Also note that the sap.Logon.changePassword does not work if the Logon plugin was initialized with sap.Logon.initPasscodeManager.
- Remove the Push and Settings plugins if present.
cordova plugin remove kapsel-plugin-push
cordova plugin remove kapsel-plugin-settings
- Prepare, build and deploy the project.
cordova run android
cordova run ios
Click on Read. Notice that the data is returned.

Now exit and remove the app from memory. Open it again and press the Read button. Notice that the data is not shown and a 401 error message is displayed on Android. On iOS, the read call fails silently.

Removing the app from memory clears any session cookies. When a request is successfully made to the SMP server such as a registration, a temporary session is established via a session cookie and subsequent requests do not need to send credentials until the session has expired. - Modify the config.xml file and set SAPKapselHandleBasicAuthChallenges and SAPKapselHandleHttpRequests to true.
- Redeploy the app.
cordova run android
cordova run ios
- Click on the Change Password button and change the password to be incorrect.
Remove the app from memory (to clear the session cookies) and restart it.
Press the Read button. Notice that there is now a prompt for credentials.


Enter the correct credentials.
After seeing that the data appears, exit the app, remove it from memory, restart it, and then click the Read button.
Notice that the read succeeds again without having to enter credentials as the HandleBasicAuth and HandleHttpRequests settings were set to true.
Note in versions less than SP 15, the page is reloaded after changing credentials. - On Android, modify the config.xml and set SAPKapselHandleX509Challenges to true.
Note this example does not work on iOS as an iOS app can only view certificates that are stored in the app's keychain. For further details see Making Certificates and Keys Available To Your App. - In index.html, comment out sap.Logon.init and uncomment sap.Logon.initPasscodeManager. Also comment out sap.Logon.core.deleteRegistration and uncomment sap.Logon.deletePasscodeManager.
- Delete the app and redeploy it. Notice that this time when a read request is made, a dialog is shown asking the user to select an X 509 certificate to log on with.
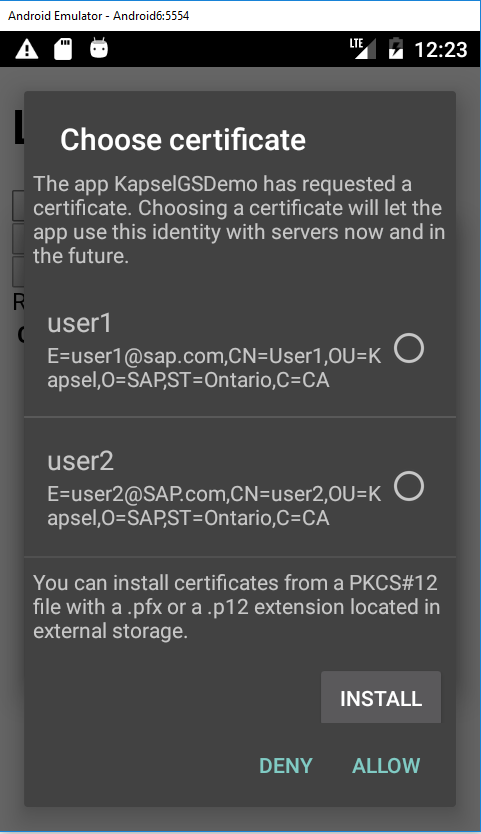 This occurs because in this case we are not proxying the OData connection through the SMP or HCPms server and the backend https://sapes4.sapdevcenter.com/sap/opu/odata/IWFND/RMTSAMPLEFLIGHT allows for authentication using a client cert or a user name and password.
This occurs because in this case we are not proxying the OData connection through the SMP or HCPms server and the backend https://sapes4.sapdevcenter.com/sap/opu/odata/IWFND/RMTSAMPLEFLIGHT allows for authentication using a client cert or a user name and password.
Client certs can be installed on an Android device by pressing Install. The certs would first need to be placed on the device. One command to do so is shown below.
adb push C:\OpenSSL-Win64\certs\user1.p12 /mnt/sdcard/
The client cert if one exists there could be exported from Chrome under Settings > HTTPS/SSL > Manage certificates > Personal (Certificate intended purposes = Client Authentication) or could be provided by your companies security department. - After selecting a cert and choosing allow, if the Clear Certs button is pressed followed by the Read button, the cert selection screen is shown again rather than reusing the previously selected cert.
Previous Home Next
- SAP Managed Tags:
- Android,
- iOS,
- SAP Mobile Platform SDK
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
276 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
329 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
407 -
Workload Fluctuations
1
Related Content
- Switch on gCTS (for existing packages) in Technology Blogs by SAP
- SAP BTP, Kyma Runtime internally available on SAP Converged Cloud in Technology Blogs by SAP
- Activation of IAS in Technology Q&A
- FCO-00011 The step start with step key |NW_ABAP_OneHost|ind|ind|ind|ind|0|0|NW_Onehost_System|ind|i in Technology Q&A
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform - Blog 7 in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 13 | |
| 10 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |