
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Developing multi-tenant applications on HCP : Iden...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-19-2016
6:37 AM
Welcome to the two-part blog which will be #5 in the blog series on "Developing Multi-tenant applications on the SAP HANA Cloud Platform".
In Part1, we introduced the concept of multi-tenant applications and the use case,
in Part2, we showcased a technical overview of the demo application built in the series and in Part3, the setup of the project for building the multi-tenant application was discussed.
In Part4, we looked at bringing in multi-tenancy in the persistence layer and initialized the data for our application.
In this blog (Part 5.1), we will look at one of the important aspects of application development and operations, namely, Security and Identity Management. We will establish trust between HCP and the consumer's IDP and import/update the users required for our application in the IDP (SCI).
In Part 5.2, we will look at assigning application specific roles to the company users (from IDP), configure SAML assertion attributes to be passed from SCI to the HCP application and validate the complete setup.
Let's go!....
Consider the following scenario:
Emily from ABC PetroCorp, has already setup the subscription in HCP for the Pollution Monitoring application provided by ITeLO Consulting. Now Emily wants to make this app available for the employees in her company, ABC PetroCorp. She has plans to reuse the corporate IDP of ABC PetroCorp, but wants to understand how access and authorization to the application can be controlled.
A consumer of any HCP application can hook up his/her corporate IDP to the HANA Cloud Platform and configure the security and identity management of his application.
For the sake of demonstration, we will showcase the SAP HANA Cloud Platform, Identity Authentication service (earlier known as SAP Cloud Identity/SCI) which can provide simple and secure cloud-based access to the business processes, applications, and data you need.

Now Emily will have to execute the following steps in her SCI tenant and HCP account, before she makes the application available for users in her company:
Section 1: Setup trust between SCI tenant and HCP Account
Section 2: Import users into the SCI tenant and update attributes
Section 3: Assign application roles to users in HCP (covered in Part 5.2)
Section 4: Configure assertion attributes in SCI and HCP to pass onto the application (covered in Part 5.2)
Section 5: Validation of the setup (covered in Part 5.2)
Emily who is the HCP administrator and has administrator access to the SCI tenant will execute the following steps to use the SCI tenant as the user store for her multi-tenant app subscription on HCP. First of all, she will need to setup trust between the SCI tenant and the HCP account of the consumer ABC PetroCorp.
Completed! We have successfully setup the trust between the consumer HCP account and the SCI tenant.
Note: Stephen will have to repeat the same steps for XYZ EnergyCorp
Emily would need to ensure the users of the application are registered with the corporate IDP of her company ABC PetroCorp.
Ideally, the corporate IDP (SCI in this case) would already have the master list of all users in the company. For demonstration purposes, we will import some demo users into the SCI tenant, who will then be given appropriate authorizations and will be used as the End users of the multi-tenant application.
The demo users for the app are stored as csv files in the Github location. Download/Clone the CSV file for ABC PetroCorp from the above github location. The csv file has 2 users in it:

Completed! We have successfully imported the users to the ABC PetroCorp application in the SCI tenant and updated the plant information for the Plant Supervisor user.
Note: Stephen will have to repeat the same steps for XYZ EnergyCorp
In this Part 5.1, we have completed Sections 1 and 2 where we established trust between the HCP account and the IDP (SCI tenant). We also imported the necessary application users into SCI.
In the next part of this blog:Part 5.2, we will look at Sections 3 to 5, i.e. assigning application specific roles to the IDP users, configuring SAML assertion attributes to be passed from SCI to the HCP application and finally validate the complete setup.
Stay tuned!
In Part1, we introduced the concept of multi-tenant applications and the use case,
in Part2, we showcased a technical overview of the demo application built in the series and in Part3, the setup of the project for building the multi-tenant application was discussed.
In Part4, we looked at bringing in multi-tenancy in the persistence layer and initialized the data for our application.
In this blog (Part 5.1), we will look at one of the important aspects of application development and operations, namely, Security and Identity Management. We will establish trust between HCP and the consumer's IDP and import/update the users required for our application in the IDP (SCI).
In Part 5.2, we will look at assigning application specific roles to the company users (from IDP), configure SAML assertion attributes to be passed from SCI to the HCP application and validate the complete setup.
Let's go!....
Consider the following scenario:
Emily from ABC PetroCorp, has already setup the subscription in HCP for the Pollution Monitoring application provided by ITeLO Consulting. Now Emily wants to make this app available for the employees in her company, ABC PetroCorp. She has plans to reuse the corporate IDP of ABC PetroCorp, but wants to understand how access and authorization to the application can be controlled.
A consumer of any HCP application can hook up his/her corporate IDP to the HANA Cloud Platform and configure the security and identity management of his application.
For the sake of demonstration, we will showcase the SAP HANA Cloud Platform, Identity Authentication service (earlier known as SAP Cloud Identity/SCI) which can provide simple and secure cloud-based access to the business processes, applications, and data you need.

Prerequisites:
- A productive SAP HANA Cloud Platform, Identity Authentication service (henceforth called SCI) tenant
- An admin user in the SCI tenant i.e. your user should be able to access the SCI Administration Console
Now Emily will have to execute the following steps in her SCI tenant and HCP account, before she makes the application available for users in her company:
Section 1: Setup trust between SCI tenant and HCP Account
Section 2: Import users into the SCI tenant and update attributes
Section 3: Assign application roles to users in HCP (covered in Part 5.2)
Section 4: Configure assertion attributes in SCI and HCP to pass onto the application (covered in Part 5.2)
Section 5: Validation of the setup (covered in Part 5.2)
Section 1: Setup trust between SCI tenant and HCP Account
Emily who is the HCP administrator and has administrator access to the SCI tenant will execute the following steps to use the SCI tenant as the user store for her multi-tenant app subscription on HCP. First of all, she will need to setup trust between the SCI tenant and the HCP account of the consumer ABC PetroCorp.
| Steps | Screenshot |
| Open and login to the SCI Administration Console. URL : https://<tenantID>.accounts .ondemand.com/admin |  |
| Login to the HCP account cockpit. URL : https://account.<landscapehost>/cockpit |  |
| Navigate to Security -> Trust |  |
| In the Trust Management screen, click on Edit. |  |
| 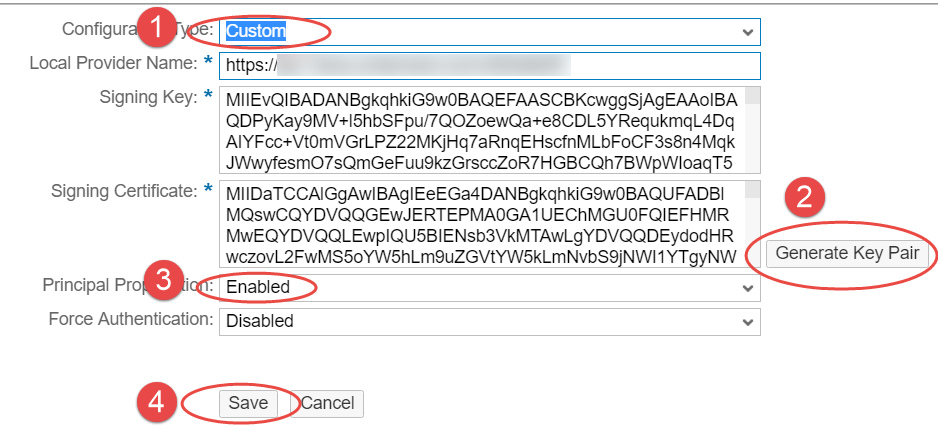 |
| Click on Get Metadata to download the metadata xml file containing the configurations created above. This will be used to setup trust with SCI. |  |
| In the SCI Admin Console, navigate to Applications & Resources -> Applications |  |
| In the Applications pane, click on Add to add a new application entry, corresponding to your HCP account. |  |
| In the pop-up enter the name as ABC_PetroCorp_IDP and click on Save. A new application entry is created. |  |
| In the created application, go to Trust tab and click on SAML 2.0 Configuration. |  |
| In the Define Metadata section, click on Browse and navigate to select the metadata.xml file downloaded from your HCP account.Note that the details of the configuration are automatically filled. Click on Save. The configuration is created and saved. |  |
| Click on Home URL and enter the URL as https://pollutionmonitoringui-<accountname>.dispatcher.<landscapehost>. (generally the URL of the subscribed HTML5 application) Click on Save. The Home URL is updated.Note: Account name can be obtained from the HCP cockpit. |  |
| Navigate to Applications & Resources -> Tenant Settings |  |
| In the settings page click on SAML 2.0 Configuration. | 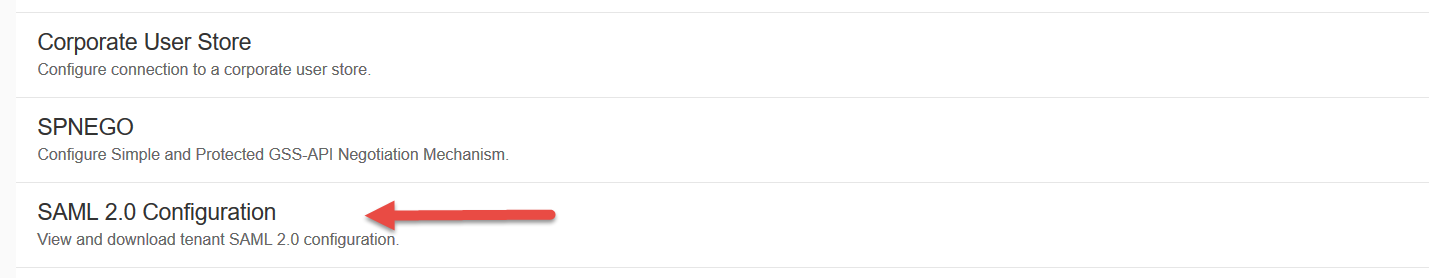 |
| Click on Download Metadata File to download the xml file containing the configurations of the SCI tenant. This will be used to setup trust with HCP. |  |
| Go back to the HCP cockpit and navigate to the Security -> Trust page and select the Trusted Identity Provider tab. |  |
| Click on Add Trusted Identity Provider to add the details of the SCI tenant. |  |
| In the General tab, click on Browse and navigate to select the metadata.xml file downloaded from your SCI tenant. Note that the details of the configuration are automacally filled.Unselect the Only for IDP-Initiated SSO option if selected. Click on Save.The configuration is created and saved. |  |
| Ensure that the identity provider is selected as Default. |  |
Completed! We have successfully setup the trust between the consumer HCP account and the SCI tenant.
Note: Stephen will have to repeat the same steps for XYZ EnergyCorp
Section 2: Import users into the SCI tenant and update attributes
Emily would need to ensure the users of the application are registered with the corporate IDP of her company ABC PetroCorp.
Ideally, the corporate IDP (SCI in this case) would already have the master list of all users in the company. For demonstration purposes, we will import some demo users into the SCI tenant, who will then be given appropriate authorizations and will be used as the End users of the multi-tenant application.
The demo users for the app are stored as csv files in the Github location. Download/Clone the CSV file for ABC PetroCorp from the above github location. The csv file has 2 users in it:
- ABCPlantSupervisor: This user will be the supervisor of a particular plant of ABC PetroCorp and should be able to view the data of his plant only.
- ABCAreaManager: This user will be the manager of an entire area, which may consist of many plants of ABC PetroCorp. He will be able to view the data of all plants in his area.

| Steps | Screenshot |
| In the csv file, there are aliases mentioned for the email id, we need to replace the alias with valid email details. For example if your email id is john.smith@sap.com:Replace <<insert your email id>> with john.smith and Replace <<insert_your_company>> with sap. Save the file. |  |
| In the SCI Admin Console, navigate to Users &Authorizations -> Import Users. |  |
| Select the appropriate application name from the list of Custom Applications. |  |
| In the Upload CSV File section, click on Browse and navigate to select the updated ABCPetroCorp.csv file (with correct email details).Click on Import. |  |
| The users need to be activated via email (hence a proper email id should have been updated in the csv file).Click on Send to send out the activation emails. |  |
| Check your mail box (of the user mentioned in csv file) and you will find two activation emails (1 for Area Manager and 1 for Plant Supervisor).Click on the links to activate and provide a password and activate your SCI user accounts. |  |
| In the SCI Admin Console, navigate to Users &Authorizations -> User Management. |  |
The Area Manager and Plant Supervisor users should be present in the list. Note the User ID for the two users, so that future logins are easy. |  |
| For the Plant Supervisor user we need to maintain his plant id as the Company information. This will be reused and explained in Section 4.Click on the Plant Supervisor user. |  |
| Scroll down to the Company Information section and click on Edit. |  |
Update the Company field as 101 (201 for XYZ EnergyCorp) and click on Save. Note: This company data will be used to pass to the assertion attribute 'plant id' in the multitenant application The user details are updated. |  |
Completed! We have successfully imported the users to the ABC PetroCorp application in the SCI tenant and updated the plant information for the Plant Supervisor user.
Note: Stephen will have to repeat the same steps for XYZ EnergyCorp
In this Part 5.1, we have completed Sections 1 and 2 where we established trust between the HCP account and the IDP (SCI tenant). We also imported the necessary application users into SCI.
In the next part of this blog:Part 5.2, we will look at Sections 3 to 5, i.e. assigning application specific roles to the IDP users, configuring SAML assertion attributes to be passed from SCI to the HCP application and finally validate the complete setup.
Stay tuned!
- SAP Managed Tags:
- SAP Cloud Identity Services,
- SAP Business Technology Platform
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
85 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
269 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
10 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,578 -
Product Updates
317 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
389 -
Workload Fluctuations
1
Related Content
- Consuming SAP with SAP Build Apps - Connectivity options for low-code development - part 2 in Technology Blogs by SAP
- Unlocking Full-Stack Potential using SAP build code - Part 1 in Technology Blogs by Members
- Part 2:- SAP Basis OS support on SUSE Linux for beginners in Technology Blogs by Members
- Value Unlocked! How customers benefit from SAP HANA Cloud in Technology Blogs by SAP
- 2405 Early Release Series for SAP Procurement and SAP Business Network releases in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 11 | |
| 11 | |
| 9 | |
| 9 | |
| 9 | |
| 9 | |
| 8 | |
| 8 | |
| 7 |