
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP HANA 2.0 SPS 00 What's New: Security - by the ...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-01-2016
10:30 PM
Introduction
In the upcoming weeks, we will be posting new videos to the SAP HANA Academy to show new features and functionality introduced in SAP HANA 2.0 Support Package Stack (SPS) 00.
The topic of this blog is security.
For the previous versions of this blog, see
- SAP HANA 1.0 SPS 12 What’s New: Security – by the SAP HANA Academy
- SAP HANA 1.0 SPS 11 What’s New: Security – by the SAP HANA Academy
- SAP HANA 1.0 SPS 10 What’s New: Security – by the SAP HANA Academy
For the full SAP HANA 2.0 SPS 00 blog list, see
- What’s New with SAP HANA 2.0 SPS 00 – by the SAP HANA Academy
Tutorial Video
What's New?
Encryption
Data volume encryption was introduced with SAP HANA 1.0 SPS 09. With 2.0, log volume encryption is now also supported. You enable log volume encryption using SQL. Data volume encryption can also be enabled using the new SAP HANA cockpit.
-- enable data volume encryption
ALTER SYSTEM PERSISTENCE ENCRYPTION ON
-- ALTER SYSTEM PERSISTENCE ENCRYPTION OFF
-- enable redo log encryption
ALTER SYSTEM LOG ENCRYPTION ON
-- ALTER SYSTEM LOG ENCRYPTION OFF
-- Query status
SELECT * FROM M_ENCRYPTION_OVERVIEWThe management of the encryption root keys used for data volume encryption, redo log encryption, and the internal application encryption service has been enhanced:
- You can now update all three root keys by SQL statement
- You can now backup all three root keys to a dedicated password-protected file
For this, a new system privilege has been added: ENCRYPTION ROOT KEY ADMIN.
You may recall that to change encryption root keys in HANA 1.0, you could SQL for the data volume encryption root key but to change the application encryption service root key, only the command line tool hdbnsutil was available.

This illustration shows the three root keys stored in the Instance SSFS (Secure Store in the File System); think of it as a safe.
- application encryption service (orange)
- data volume (persistence) encryption (green)
- log volume encryption (blue)
The contents of the Instance SSFS can be exported in a password protected file.
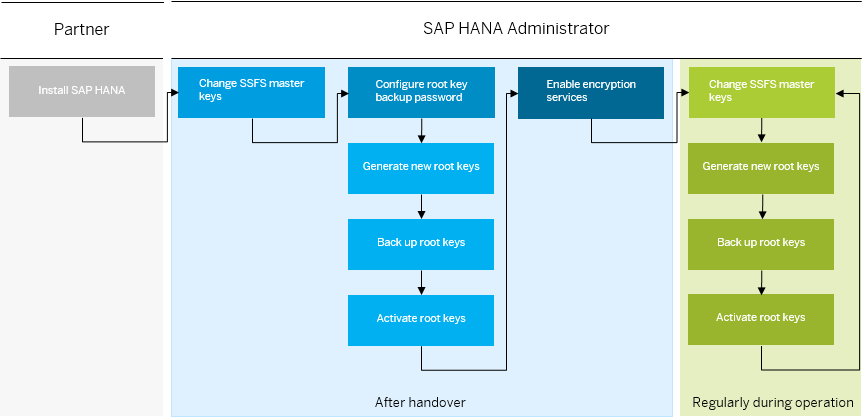
This illustration shows the hand-over flow for changing master and root keys. You would follow this flow when you receive SAP HANA as an appliance from a hardware vendor, or SAP HANA express edition on a virtual machine (for production use).
To avoid any data loss in a disaster scenario, the best approach is to first create a new key in the safe (SSFS) but not activate it:
-- change encryption root keys
ALTER SYSTEM PERSISTENCE ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATE
ALTER SYSTEM LOG ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATE
ALTER SYSTEM APPLICATION ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATENext, perform the backup of the root key(s). This will ensure that you have a backup of the new key before it is actually being used by HANA. Should you need to recover the encryption root key store, you can be confident that your backup contains all the root keys that are potentially needed.
To backup the root keys, you can use the follow SQL statement:
ALTER SYSTEM SET ENCRYPTION ROOT KEYS BACKUP PASSWORD <passphrase>Next, create the root key backup file with RKB extension, using either SQL:
SELECT ENCRYPTION_ROOT_KEYS_EXTRACT_KEYS
('PERSISTENCE, APPLICATION, LOG') FROM DUMMY
-- copy the CLOB result and save it to a file
-- at a secure external location (with extension *.rkb)... or the hdbnsutil tool with -backupRootKeys flag:
# alternatively use command line
hdbnsutil -backupRootKeys <filename>.rkb --type='ALL' [--dbid=dbid ]
hdbnsutil -validateRootKeysBackup <filename> [--password=<passphrase>]You can backup each key separately or you can backup all keys together.
The DBID parameter is used for tenant databases, as in multitenant database containers systems each tenant has its own root keys.
Then, when you are confident that the root key backup is good, that is the validation is successful (and maybe have tested recovering the key on a test system), you can now activate the new root key(s):
-- activate the key
ALTER SYSTEM PERSISTENCE ENCRYPTION ACTIVATE NEW ROOT KEY
ALTER SYSTEM LOG ENCRYPTION ACTIVATE NEW ROOT KEY
ALTER SYSTEM APPLICATION ENCRYPTION ACTIVATE NEW ROOT KEYShould you need to recover the keys, here is the command:
hdbnsutil -recoverRootKeys <filename>.rkb --type='ALL' [--dbid=<dbid>]
[--password=<passphrase>]Authorization - LDAP Groups
You can now take advantage of LDAP group membership to authorize SAP HANA users, for those environments that use an LDAP-compliant identity management server to manage users and their access to resources. There are many different LDAP-compliant IdM implementations, SAP provides one, but also Microsoft with Active Directory, others are open source.
The new system privilege LDAP ADMIN is required to configure LDAP group authorization.
The following figures illustrates how a user is authorized on the basis of their LDAP group membership:

You can create an LDAP provider by SQL statement:
-- create LDAP provider
CREATE LDAP PROVIDER my_ldap_provider
CREDENTIAL TYPE ‘PASSWORD’
USING ‘user=cn=LookupAccount,o=sap.com;password=hUWe8ZTiQyG’
USER LOOKUP URL
'ldap://idp.sap.com:389/ou=Users,dc=sap,dc=com??sub?(&(objectClass=user)(sAMAccountName=*))'
ATTRIBUTE DN 'distinguishedName'
ATTRIBUTE MEMBER_OF 'memberOf'
SSL ON
DEFAULT ON
ENABLE PROVIDER
User authorization is then delegated to the LDAP provider:
-- validate the LDAP provider
VALIDATE LDAP PROVIDER my_ldap_provider CHECK USER user1
-- create user with LDAP authorization
CREATE USER user1 PASSWORD <password> AUTHORIZATION LDAP
For more information, see
- LDAP group authorization - by aleks.aleksic
Authorization - GRANT | REVOKE PUBLIC role
Restricted users can now be converted into a standard user (or vice versa) by SQL statement:
-- granting (or revoking) the PUBLIC role
ALTER USER <username> GRANT ROLE PUBLIC;
ALTER USER <username> REVOKE ROLE PUBLIC;
-- granting (or revoking) authorization to create objects in the user's own schema
ALTER USER <username> GRANT CREATE ANY ON OWN SCHEMA;
ALTER USER <username> REVOKE CREATE ANY ON OWN SCHEMA;
-- enabling (or disabling) full SQL
ALTER USER <user_name> ENABLE CLIENT CONNECT ;Security Administration with SAP HANA Cockpit
The SAP HANA cockpit for SAP HANA 2.0 has been completely redesigned both from an architecture perspective as in the way the cockpit looks (within the Fiori framework).
The three tiles, Data Storage Security, Auditing, and Authentication, clearly show important security information, for example when SSFS master keys or the SYSTEM user password were last changed.
Selecting the tile will open the respective app, to configure data volume encryption, auditing or password policies.

New is that in cockpit 2.0, you can also create and configure database users, both standard and restricted.

Playlist
On the SAP HANA Academy, there is a full playlist covering all aspects of security: bit.ly/SAPHANASecurity
Documentation
For more information see:
SAP HANA
- SAP HANA Security on sap.com
- SAP HANA Security Whitepaper
- LDAP group authorization - by aleks.aleksic
SAP Help Portal
- How and when to change encryption keys (SAP HANA Security Guide)
- Root Key Backup
- Internal Application Encryption Service
- Configure LDAP Group Authorization
- SAP HANA Cockpit
SAP Notes
- 2380257 - SAP HANA Platform 2.0 SPS 00 Release Note
- 2159014 - FAQ: SAP HANA Security
- 2380291 - SAP HANA 2.0 Cockpit Central Release Note
Thank you for watching
The SAP HANA Academy provides technical enablement, implementation and adoption support for customers and partners with 1000’s of free tutorial videos.
For the full library, see SAP HANA Academy Library - by the SAP HANA Academy
For the full list of blogs, see Blog Posts – by the SAP HANA Academy
- Subscribe to our YouTube channel for updates
- Join us on LinkedIn: linkedin.com/in/saphanaacademy
- Follow us on Twitter: @saphanaacademy
- Google+: plus.google.com/+saphanaacademy
- Facebook: facebook.com/saphanaacademy

You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
417 -
Workload Fluctuations
1
Related Content
- SAP IDM/SAC Support for SAC roles and TEAM liaison in IDM in Technology Q&A
- SAP Migration to AWS - Considerations from Infrastructure side in Technology Blogs by Members
- SAP HANA Cloud の「マルチ環境」のサポートと SAP HANA Cloud の Kyma 環境からの使用 in Technology Blogs by SAP
- BTP - Configuring the basics! A proposed set of steps, thinking and how-to... in Technology Blogs by Members
- To become an SAP BTP Security expert what certification would help? in Technology Q&A
Top kudoed authors
| User | Count |
|---|---|
| 33 | |
| 25 | |
| 10 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |