
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Message Signature and Validation between HCI IFlow...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
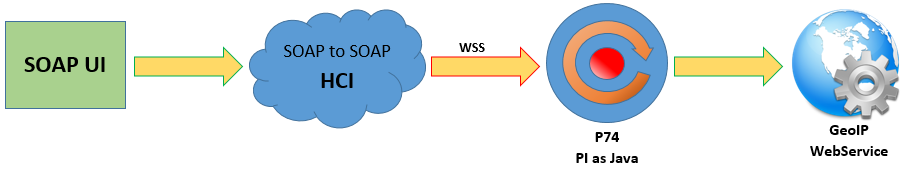
My goal in this blog is to show how to setup message signature and validation between HCI and PI systems. Right now i will show only the „Sign” and „Validate” parts from WSS. The basic message flow in the scenario is the following:
SOAPUI -> HCI -> AEX (SID: P74) -> WebService
The WSS in my example will be used only between the HCI and AEX systems.
Prerequisites:
The message flow in HCI and in AEX is a simple SOAP – to – SOAP scenario. This needs to be setup, and in this blog i am not dealing with these configuration steps. Also in the below steps i am dealing with self signed certificates, which can be ok for testing purpose, but in a real productive scenario use certificates which are signed by the CA you trust.
Configuration steps:
- ) Download the system.jks keystore from the HCI tenant, and create a new alias there named like „sign”. (To edit the keystore entries i used the KeyStore Explorer program.) Into this alias create a new keypair. The HCI flow will use the private key from this keystore alias to sign the message.
- ) Create a second alias in this keystore and import the AEX system’s public certificate. This will be needed to validate the reply message from AEX system. In AEX just to make the example more simple we will use the AEX system’s private key (from the corresponding ICM keystore view) for sign the reply message, therefore from this view the public certificate is needed for HCI to validate the reply message.

So at the end your system.jks keystore should look like this:

The alias named „sign” is for signing the message by HCI, and the other alias is a Trusted Certificate entry – this is the public certificate of the AEX system.
3.) Deploy the new system.jks keystore into the HCI tenant.
4.) Create a new keystore in NWA of the AEX system and import the public certificate which will be used to validate the request message coming from the HCI flow:
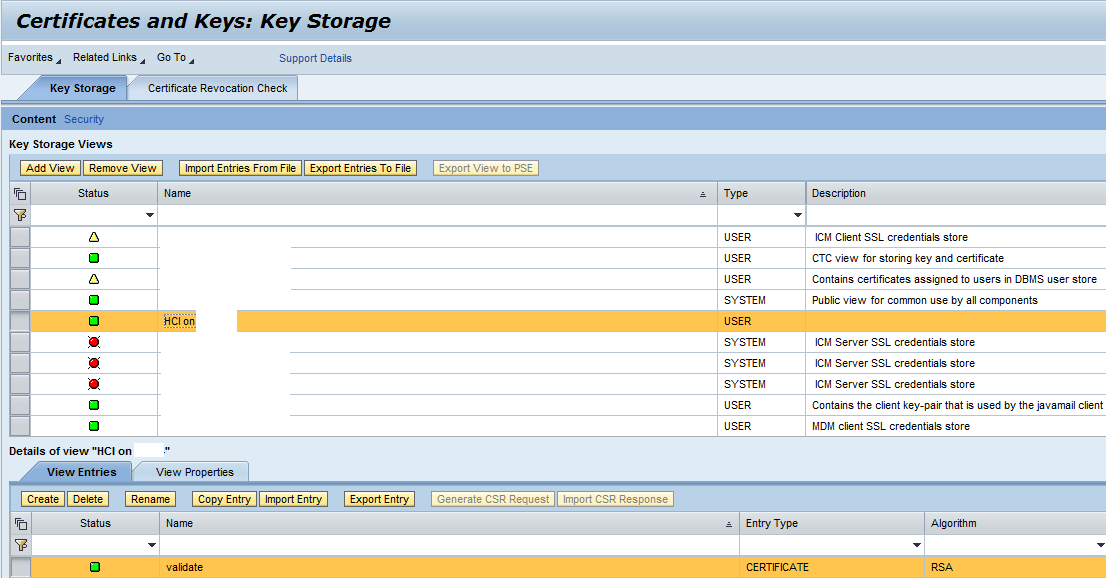
Here you will need to import the public certificate from the point 1. With KeyStore Explorer you can easily export the public certificate from the „sign” alias, and use it in the NWA keystore of the AEX system.

5.) In the receiver SOAP channel of the HCI’s IFlow set the following setting on the „WS-Security” TAB:

6.) In the AEX system in the SOAP sender channel select the security profile:

7.) And in the ICO specify the validation for the incoming request message. You will need to refer to the public certificate from point 4:
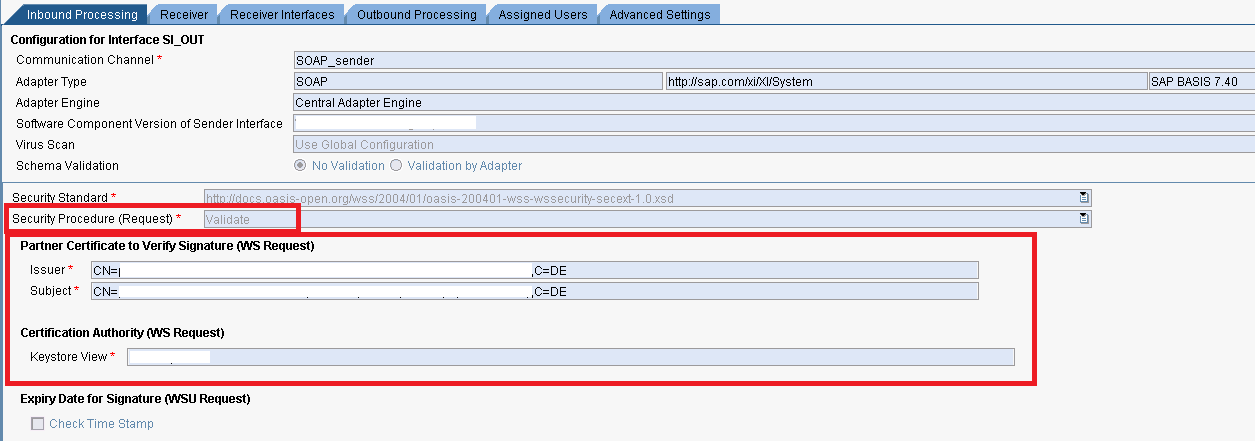
8.) The response message from AEX to HCI will be signed by the AEX system’s private key :

So select the option „Sign” from the Security Procedure (Response), and fill the Keystore View and Keystore Entry fields. As i mentioned just to make the case simple i used the private key from the ICM keystore view of the AEX system.
9.) And run a test in SOAPUI tool and call the Endpoint of the HCI IFlow:

10.) The messages are processed successfully both in HCI and in AEX, and in SOAPUI we got the correct response:

- SAP Managed Tags:
- Cloud Integration,
- SAP Process Integration
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
326 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
403 -
Workload Fluctuations
1
- SAP BPA Read Barcode/QR code and validate digital signature from pdf documents in Technology Q&A
- Copy a Tenant Database using system replication in Technology Blogs by SAP
- SAP Cloud Integration: How to use mTLS for calling external App from iFlow (Outbound) in Technology Blogs by SAP
- Work Zone Dynamic Tile for CAP applications in Technology Blogs by Members
- Consume services of an on-premise system securely from SAP S/4HANA Cloud, Public Edition or SAP BTP, ABAP Environment in Technology Blogs by SAP
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |