
- SAP Community
- Groups
- Interest Groups
- Application Development
- Blog Posts
- Integrating SAP Enterprise Threat Detection with F...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
SAP runs enterprises; any impact to an SAP system could put a halt to business operations and cause downtime to enterprises. Unfortunately, for this very reason attackers target SAP systems; from a business perspective, SAP is the critical infrastructure and the lifeline to the ability to provide goods and services to their customers. By taking down SAP systems, businesses can come to a standstill. At the very least, SAP systems hold critical information and in this day and age, when data is more valuable than gold, everyone from insiders to consultants is accessing sensitive information and with motivations from corporate espionage to terrorism, your systems are at risk.
There have been public references to corporate espionage, targeted attacks and possible state sponsored attacks targeting SAP systems and the critical information these systems hold. The only way to track these targeted attacks is through forensic evidence such as logs – including firewall logs, security event logs, and SAP application trace logs. Often these threats sit dormant, leveraging backdoors and unpatched vulnerabilities to take hold of a system and gather data, and then exfiltrating this sensitive information back to the attackers, often encrypting the evidence to go undetected, and sweeping away the evidence when the task is complete.
Why run both solutions integrated?
SAP Enterprise Threat Detection has a strong focus on protecting the SAP business landscape by analyzing security information on the application level and enriching it with context data. So the solution can detect direct attacks against systems or can analyze the impact of a known attack. But sometimes the SAP system is the target, but was not compromised. In these cases the end user devices are compromised and the hacker may get access to a SAP system with the user’s stolen identity. The kinds of attacks targeting an end user device can be detected with FireEye through monitoring the suspicious activities (network, mail, files …). So would it not make sense that FireEye would send that information to SAP Enterprise Threat Detection, to find out if the hacker already accessed confidential information? Yes, it would and that is what the blog is about.
But why integrate both solutions if the attack can be detected before the attacker accesses the endpoint? Attackers can obtain legitimate credentials in a variety of ways. Organizations could be breached when a trusted third party is compromised and the attacker exploits the trust between the parties to access the victim organization with legitimate credentials. A malicious insider can also obtain credentials without any malicious tools on the network. Advanced attackers also cannot be blocked like a firewall opens or close a port. The potential malicious code used by advanced attackers will be executed in a virtual environment (FireEye MVX) to analyze the behavior and to correlate the outcome with other security events to identify an advanced attack. Alerts from the FireEye device combined with the SAP Enterprise Threat Detection can alert you to attacks against your end users and against your SAP systems.
Example scenario
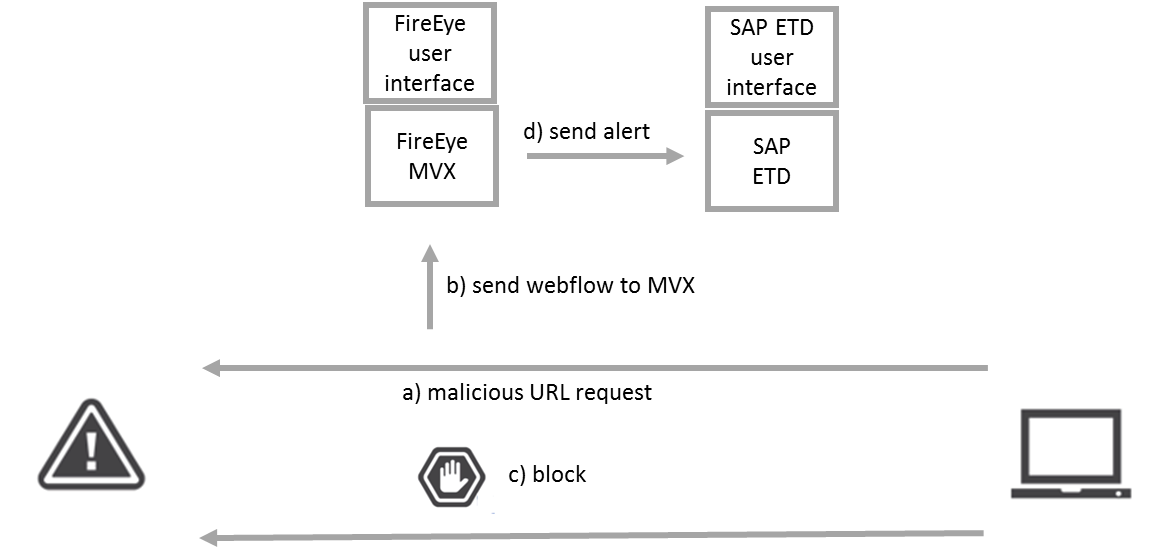
Professional attackers keep getting more determined and organized. The tactics they use are targeted, customized, and persistent. They can attack their targets via the web or a malicious email and use previously unseen malware to achieve their goals. A financially motivated criminal often sends a malicious email to an end user. That email can include a link to send the victim to an infected web page. If the end user clicks on the link, the attacker can gain full access to the victim's computer with access to all its business applications. In our example, an organization can identify attacker tools that are trying to connect to malicious infrastructure to receive commands or send data out, via FireEye's MVX technology.
APT detection example:
- A user receive an email with a malicious web link and open it
- FireEye sends the potential malicious webflow into MVX for analysis, without blocking the user
- FireEye detects the malicious behavior and create an alert. Detected command & control communication will be blocked.
- FireEye send an alert to SAP Enterprise Threat Detection about the infected device
Security team:
- FireEye: Alert about infected device in console
- SAP Enterprise Threat detection: Provide insight if something happened on the SAP business systems
Integrating the FireEye MVX with SAP Enterprise Threat Detection enables a security analyst to understand, if and how a SAP landscape has been affected. So the security analyst is better prepared to respond in the first crucial minutes following a breach. The longer an intrusion goes unnoticed, the more access attackers have to data that’s no longer secure. The pairing of SAP Enterprise Threat Detection and FireEye MVX gives the analyst the advantage of being able to quickly address a breach, potentially saving significant time, money, and loss of data.
Below is a FireEye detailed report of an analyzed malware object.

Technical configuration
In our case we want to configure the integration between SAP Enterprise Threat Detection and a FireEye MVX engine. The MVX engine sends its notifications in the Common Event Format (CEF). This example uses the sample web-infection event taken from the FireEye Alert Notifications (Release 7.7):
CEF:0|FireEye|CMS|7.6.0.334042|WI|web-infection|4|rt=Mar 25 2015 22:07:50 UTC src=xxx.xx.x.xxx dproc=InternetExplorer 7.0 cs3Label=osinfo cs3=Microsoft WindowsXP 32-bit 5.1 sp3 15.0210 filePath=xxx.xx.x.xx:xxxx/metasploit dvchost=axhwmps dvc=xxx.xx.xx.x smac=00:0c:29:d9:2e:e1 cn1Label=vlan cn1=0 externalId=11646 cs4Label=link cs4=https://www.fireeye.com/event_stream/events_for_bot?inc_id\=11646 act=notified cs2Label=anomaly cs2=misc-anomaly cs1Label=sname cs1=Malware.Binary.url\n
To send the CEF notifications to the SAP Enterprise Threat Detection add the relevant information under the notifications area in setting on your FireEye device:

Ok, so what needs to be done to integrate the products?
- Import the FireEye ESP example project which is delivered with SAP Enterprise Threat Detection 1.0 SP3
- Configure the SAP ESP project and execute it
- Test the integration and some troubleshooting tips
The goal is, that the FireEye MVX engine sends critical alerts in the CEF format via TCP/IP to SAP Event Stream Processor (ESP), which is part of SAP Enterprise Threat Detection (ETD). SAP Event Stream Processor will then map the data to the SAP Enterprise Threat Detection (ETD) internal format and store the data into the SAP HANA database. After that, the data will be available in the ETD user interface.
The SAP Enterprise Threat Detection installation package (HCO_SECURITY_MON.tgz), which you downloaded from the SAP Service Marketplace (http://service.sap.com/), also contains the FireEye example project for SAP ESP. If you do not have the package, please download it again from the SAP Service Marketplace (alternatively you can also export it from the SAP HANA repository).
Now we have to import this project to SAP ESP. Please open your SAP ESP studio and change to the ESP authoring perspective. Please import the FireEye project file (fireeye_events_over_tcp_in_etd).

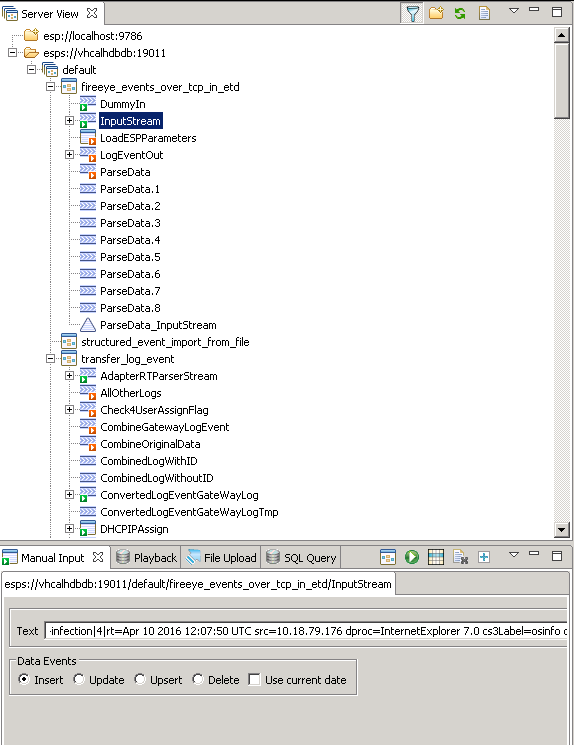
On the picture below you can see the structure of the FireEye project. There is a “Socket_Input”, which is a TCP/IP socket, since FireEye will send the data via TCP/IP. The next box is “InputStream”, which is handling incoming data streams. Then the FireEye specific part comes with “Parse Data”. Here is the mapping of the FireEye format to the SAP ETD format. After that there is a “stream out” component (LogEventOut). In the configuration file (*.ccr) there is an existing binding for that output stream. The output stream of the FireEye project will be linked to the ESP project transfer_log_event and its module LogEventIn. So the FireEye project itself is not writing the data into the SAP HANA database, it uses the standard project transfer_log_event, which is delivered by SAP (this means also, if the standard project transfer_log_event is not running, the FireEye project cannot work).

On the next picture you can see the bindings of the FireEye project. Please ensure the Remote Stream settings are correct.

Please also click on parameters. Here you can find the TCP/IP port of the socket. This is required, if you want to send alerts from FireEye to SAP ESP (server name and port is required.)

Now you can run the FireEye project on your SAP ESP server (you can use local for testing or your can choose your productive instance on the server)

Now we will test it manually (without a FireEye system sending the data). Please change the perspective to “ESP Run” in the SAP ESP studio. Click on the input stream and choose “Select the Stream for Manual Input”.

You can paste a test string into the text input field and use the string below. Please adjust the time settings (actual time and date), otherwise it will be tricky to find that data later in the SAP ETD user interface. Click on run button.
CEF:0|FireEye|CMS|7.6.0.334042|WI|web-infection|4|rt=Mar 25 2015 22:07:50 UTC src=xxx.xx.x.xxx dproc=InternetExplorer 7.0 cs3Label=osinfo cs3=Microsoft WindowsXP 32-bit 5.1 sp3 15.0210 filePath=xxx.xx.x.xx:xxxx/metasploit dvchost=axhwmps dvc=xxx.xx.xx.x smac=00:0c:29:d9:2e:e1 cn1Label=vlan cn1=0 externalId=11646 cs4Label=link cs4=https://www.fireeye.com/event_stream/events_for_bot?inc_id\=11646 act=notified cs2Label=anomaly cs2=misc-anomaly cs1Label=sname cs1=Malware.Binary.url\n
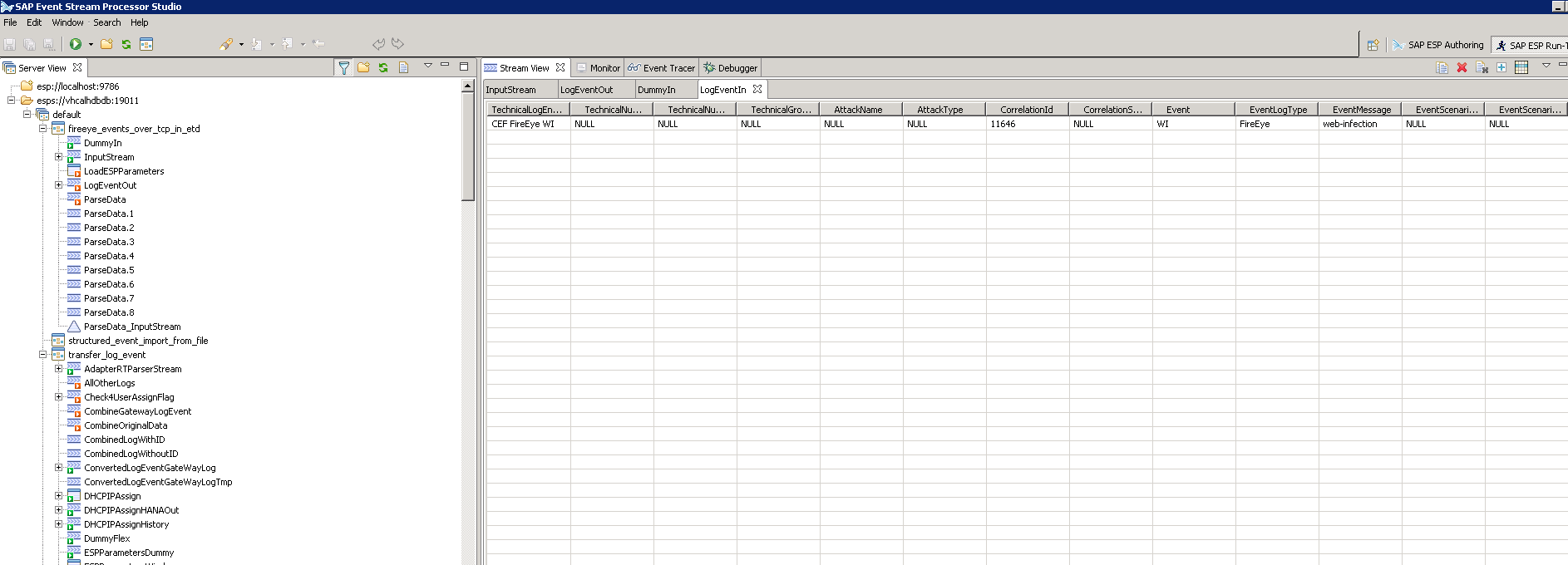
Troubleshooting tip:
If you have problems, you can monitor in the “ESP Run” perspective, if there are new data coming in. Here an example of the “Output stream” of the FireEye project:

Below “Input stream” of the “transfer_log_event“ project, which is reused by the FireEye project (the data will be refreshed every 3-5 seconds, so if you do not see anything, just send the test string again).
Result
Let us check now the SAP Enterprise Threat Detection user interface (forensic lab). We can see a new FireEye log type. So there is data from FireEye available in SAP ETD.

Now it is very easy to create a view or a pattern with the data from FireEye. So you can easily find out, which transaction or function modules where called in SAP, from a PC which is infected with malware (reported by FireEye).
- SAP Managed Tags:
- Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
A Dynamic Memory Allocation Tool
1 -
ABAP
8 -
abap cds
1 -
ABAP CDS Views
14 -
ABAP class
1 -
ABAP Cloud
1 -
ABAP Development
4 -
ABAP in Eclipse
1 -
ABAP Keyword Documentation
2 -
ABAP OOABAP
2 -
ABAP Programming
1 -
abap technical
1 -
ABAP test cockpit
7 -
ABAP test cokpit
1 -
ADT
1 -
Advanced Event Mesh
1 -
AEM
1 -
AI
1 -
API and Integration
1 -
APIs
8 -
APIs ABAP
1 -
App Dev and Integration
1 -
Application Development
2 -
application job
1 -
archivelinks
1 -
Automation
4 -
BTP
1 -
CAP
1 -
CAPM
1 -
Career Development
3 -
CL_GUI_FRONTEND_SERVICES
1 -
CL_SALV_TABLE
1 -
Cloud Extensibility
8 -
Cloud Native
7 -
Cloud Platform Integration
1 -
CloudEvents
2 -
CMIS
1 -
Connection
1 -
container
1 -
Debugging
2 -
Developer extensibility
1 -
Developing at Scale
4 -
DMS
1 -
dynamic logpoints
1 -
Eclipse ADT ABAP Development Tools
1 -
EDA
1 -
Event Mesh
1 -
Expert
1 -
Field Symbols in ABAP
1 -
Fiori
1 -
Fiori App Extension
1 -
Forms & Templates
1 -
IBM watsonx
1 -
Integration & Connectivity
10 -
JavaScripts used by Adobe Forms
1 -
joule
1 -
NodeJS
1 -
ODATA
3 -
OOABAP
3 -
Outbound queue
1 -
Product Updates
1 -
Programming Models
13 -
Restful webservices Using POST MAN
1 -
RFC
1 -
RFFOEDI1
1 -
SAP BAS
1 -
SAP BTP
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP CodeTalk
1 -
SAP Odata
1 -
SAP UI5
1 -
SAP UI5 Custom Library
1 -
SAPEnhancements
1 -
SapMachine
1 -
security
3 -
text editor
1 -
Tools
17 -
User Experience
5
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |