
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by Members
- SAP GRC 10/10.1/12.0 - Access Control Module relat...
Financial Management Blogs by Members
Dive into a treasure trove of SAP financial management wisdom shared by a vibrant community of bloggers. Submit a blog post of your own to share knowledge.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
madhusap
Active Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-17-2015
4:05 PM
Purpose
The purpose of this blog post is to explain the about the various tables related to GRC Access Control module and how these tables can be utilized in order to prepare reports or extract data as per your requirements:
1. Request Reason
Request reason is stored in SAPscript, with Text Object as "GRC" and ID as "LTXT". You can use standard SAPscript Function Module (READ_TEXT) to fetch request reason of a GRC request by passing the "TEXT" value to the Name field. This TEXT value can be fetched from table STXH
e.g: ACCREQ/00155D08DA361ED2A1BD201C710165A5/LONG_TEXT (For access requests ACCREQ/RequestID(GRACREQ Table)/LONG_TEXT



2. Request Comments
Request comments are stored as SAPscript objects. You can use standard SAPscript Function Module (READ_TEXT) to read the comments of a GRC request.

a. Retrieve the "EXTERNAL_KEY" value from GRFNMWRTINST table by passing the request number details in "EXTERNAL_KEY_DIS" field
 b. Retrieve the "TDNAME" value from STXH table by passing the "EXTERNAL_KEY" value retrieved from above step with * at the end as the comments get saved with timestamp and there could be multiple comments.
b. Retrieve the "TDNAME" value from STXH table by passing the "EXTERNAL_KEY" value retrieved from above step with * at the end as the comments get saved with timestamp and there could be multiple comments.

You have to pass following values to the function module:
ID = NOTE
NAME = TDNAME
OBJECT = GRC

3. GRACREQ - Request details table
This table will provide the information about Request ID, Request Type, Request Creation Date and Request Priority. (Note: You can also get UAR request details from this table)
4. GRACREQUSER - GRC Request User details table
This table will provide the information about user for whom GRC request has been raised and provides details about User ID, User First Name, User Last Name and User Email ID
5. GRACREQPROVITEM - GRC Request Line Item Details
This table will provide the information about the request and the below Line Items in the request with their corresponding VALID FROM and VALID TO dates.
Role
System
Fire Fighter Id
User
Profile
PD Profile
Firefighter Role
6. GRACREQPROVLOG - GRC Request Provisioning Logs
This table will provide the information about the request and the Line Items in the request with their provisioning status (Success or Failure or Warning)
7. GRFNMWRTINST - GRC Request Instance Details
This table will provide the information about the request and its corresponding instance status.
8. GRFNMWRTDATLG - GRC Request Line Item Approval Status
Get the details of Instance ID from GRFNMWRTINST table by passing the request number in "EXTERNAL_KEY_DIS" field. Based on the Instance ID you can get the details of each Line Item approval status in the request, Path ID, Stage Sequence Number and Approver User column in this table gives the details of the approvers.
Based on Path ID you can get the stage details by using the tables "GRFNMWCNPATH" and "GRFNMWCNSTG"
9. GRFNMWRTAPPR - Current Approver for Request Line Items
This table will provide the information about the request and current approvers for corresponding Line Items in the request.
10. GRFNMWRTMSGLG - Workflow Instance Message Logs
This table hold all the details about the message number and variables and these are used by code logic and data is displayed in audit logs of access requests. You can ask your ABAP programmer to use this table as reference to pull out the required details for Audit logs.
Class: CL_GRFN_MSMP_INSTANCE_MODEL
Method: GET_INSTANCE_AUDIT_MESSAGES
11. GRACROLE & GRACROLEAPPRVR
These tables will provide the information about the roles and their corresponding role owners maintained in BRM.
12. GRACRLCONNVAL
This table will provide you the details about Auto provisioning status for a role
13. HRUS_D2 - Approver Delegation Table
This table will provide the information about the delegated approvers in GRC
14. GRACSTDROLE and GRACSTDROLESYS
These tables will provide the information about the default roles maintained in GRC.
15. GRPCCHKO and GRPCPHIO - GRC Request Attachment Details
These tables will provide the information about the attachments in the GRC request.
Get Request ID for a GRC request from GRACREQ Table
Input Request ID retrieved above in the field PROP08 of table GRPCPHIO.Get PHIO_ID from GRPCPHIO table. This table also gives attachment description details.
Input PHIO_ID to table GRPCCHKO. This table will provide Attachment Name and Type details.
16. Mitigating Control Vs. Risk/Monitor/Approver Details
Retrieve OBJID from table HRP5354 by inputting the Mitigating Control ID in SHORT_KEY1 field
Retrieve KEY 1 and KEY 2 from HRT5320 by passing OBJID retrieved above into T_OBJID field which will give Risk/MC Monitor/MC Owner Details
17. Mitigating Control Short Text and Long Text
Short Text
Retrieve "OBJID" from table HRP5354 by passing Mitigating Control ID into "SHORT_KEY1" field
Retrieve 'STEXT' from table HRP1000 by passing 'OBJID' value retrieved from above table
Long Text
Retrieve "OBJID" from table HRP5354 by passing Mitigating Control ID into "SHORT_KEY1" field
Retrieve "TABNR" values by sorting 'AEDTM' and take the latest last modification date from table HRP1002 by passing PLVAR = '01', OTYPE = 'P2', OBJID = value retrieved from above table and SUBTY = '0001'
Retrieve "TLINE" values from table HRT1002 by passing TABNR value retrieved from above table
18. Risk Long Text
Class: CL_GRFN_SAPSCRIPT
Method: RETRIEVE_STRING
Pass following values:
IV_LANGUAGE = EN
IV_OBJECT_ID = SOD_RISK/<RiskID>
IV_CLASS = LTXT
IV_TOKEN = RSK
IV_APPLICATION = GRC
19. Control Assignment request Items table
GRACMITMSMPVALI - This table will have the Control Assignment request and corresponding Lineitems of that request.
MSMP Instance and External Key in this table are referenced from GRFNMWRTINST table.
20. Mitigating Controls related tables
GRACMITUSER - mitigating controls assigned to User Level Risk violations
GRACMITUSERORG - mitigating controls assigned to User Org Level Risk violations
GRACMITROLE - mitigating controls assigned to Role Level Risk violations
GRACMITROLEORG - mitigating controls assigned to Role Org Level Risk violations
GRACMITPROF - mitigating controls assigned to Profile Risk violations
GRACMITOBJECT - mitigating controls assigned to HR Objects Risk violations
21. Mitigation-Violation Tables for Access Request (temporary storage while workflow is running)
GRACMITUSERAR - stores mitigating controls assigned to User Level Risk violations during Access Request approval process. Once request is finished, if access is provisioned, mitigations are transferred to GRACMITUSER
GRACMITUSERORGAR - stores mitigating controls assigned to User Org Level Risk violations during Access Request approval process. Once request is finished, if access is provisioned, mitigations are transferred to GRACMITUSERORG
22. GRC User Access Review (UAR) related tables:
GRACREQ - This table will provide the information about Request ID, Request Type, Request Creation Date and Request Priority for UAR requests also.
GRACREJREASON - REJECTION reasons for UAR requests are stored in this table.
GRACREVCORDMAP - This table will store the Reviewer - Coordinator mapping defined in GRC system.
GRACREVITEM - For GRC access requests, the line item details can be retrieved from table GRACREQPROVITEM. Similarly for UAR requests, the line item details can be retrieved from table GRACREVITEM.
This table will provide the information about the UAR request and the lineitems with details mentioned below:
User ID - Connector - Review Item ID (Need to use GRACROLE to get the review item name which is role name) - Review Item usage.
GRACREVREJUSER - This table stores details of users rejected in UAR requests with the correpsonding rejection reasons referenced from tables GRACREJREASON and GRACREJREASONT.
GRACREQPROVLOG - GRC Access Request Provisioning Logs
The same table will provide the information about the UAR requests and the Line Items in the request with their provisioning status (Success or Failure or Warning)
GRFNMWRTMSGLG - GRC Access Request Audit Log table
This table hold all the details about the message number and variables and these are used by code logic and data is displayed in audit logs of access requests.
E.g. If you want to know which user saved the UAR request in Draft status, the details can be seen in the audit log and in the backend, the data will be in this table with SYMSGNO 317.
You can ask your ABAP programmer to use this table as reference to pull out the required details from Audit logs.
Class: CL_GRFN_MSMP_INSTANCE_MODEL
Method: GET_INSTANCE_AUDIT_MESSAGES
23. GRC Emergency Access Management (EAM) related tables:
GRACFFOWNER / GRACFFOWNERT - This table will store the mapping between Firefighter ID Owners and corresponding Firefighter IDs
GRACFFCTRL - This table will store the mapping between Firefighter ID Controllers and corresponding Firefighter IDs along with the log delivery options (Email, Workflow or Log Display) for the controller. If the delivery option is left BLANK then by default the option considered is "Log Display".
GRACFFOBJECT / GRACFFOBJECTT - This is the master table which stores details of all Firefighter IDs in various ABAP systems and also stores the last logon date of Firefighter IDs.
GRACFFUSER / GRACFFUSERT - This table will store the mapping between Firefighter IDs and users assigned to those Firefighter IDs
GRACREASONCOD / GRACREASONCODT - This is a master table will store the details of all EAM reason codes, reason code descriptions and status.
GRACREASONSYS - This table will store the mapping between reason codes and corresponding target connectors
GRACFFLOG - When Firefighter Log Sync job is executed the details of Firefighter ID, Firefighter User, Logon and Logoff time, Reason Code used and Workflow Status (whether sent or not) are updated in GRACFFLOG table.
GRACFFREPMAPP - For every entry in GRACFFLOG table, if the corresponding transaction usage details are synced to GRACACTUSAGE table, then the mapping between FF LOG ID in GRACFFLOG table and ACTION ID in GRACACTUAGE table is stored in GRACFFREPMAPP table.
Reason Code, Actions and Additional Activity Details - These details are required when you are building custom reports for internal or audit reporting.
a. Retrieve the "EXTERNAL_KEY" value from GRFNMWRTINST table by passing the request number details in "EXTERNAL_KEY_DIS" field with process ID as SAP_GRAC_FIREFIGHT_LOG_REPORT

b. Pass the external key value excluding "FFLOG\" into WF_ID as shown below and retrieve Text Object ID.
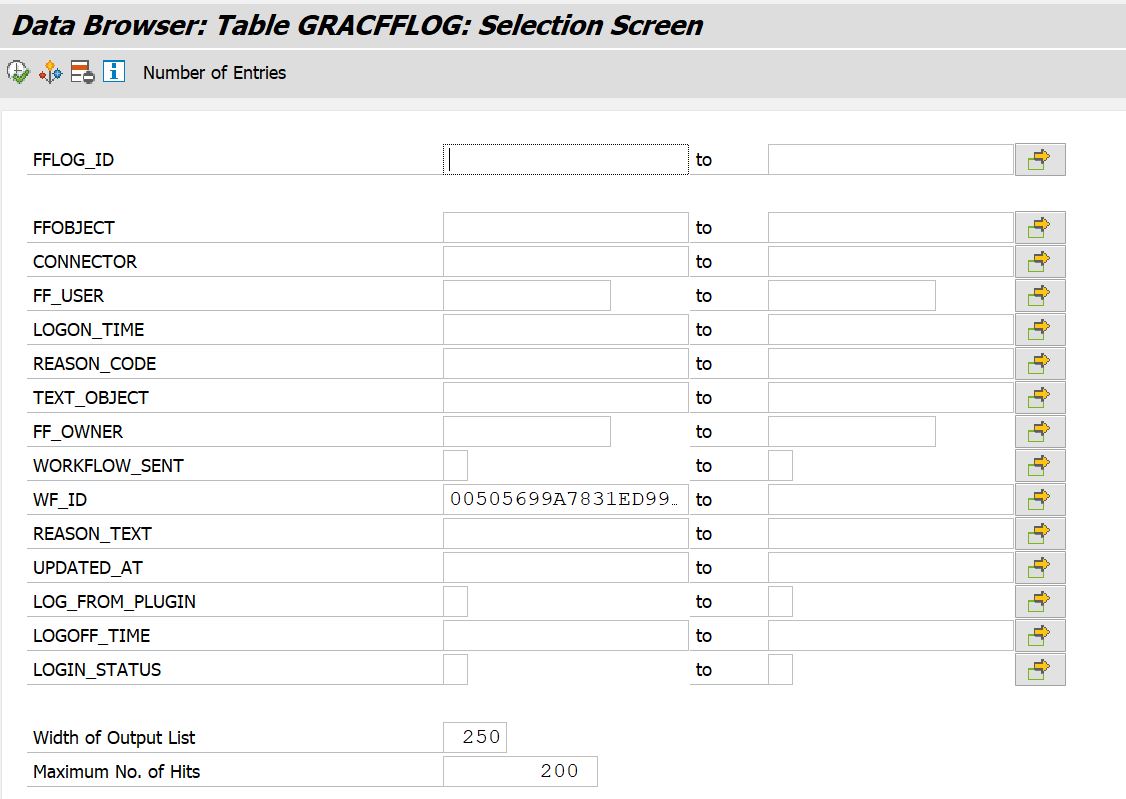

For retrieving the Reason Code , Actions and Additional Actions pass the Text Object ID retrieved from GRACFFLOG table in the following method:
Reason Code

Action Details

Additional Activity Details

SAP GRC will capture the following logs during a Firefighter session and creates an automated workflow request for log review by Firefighter ID controllers.
Transaction Logs: Retrieves transactions executed by the Firefighter ID from transaction STAD and then stores them in GRACACTUSAGE table
Change Logs: Retrieves all the change logs based on activities performed by the Firefighter ID from change document tables CDPOS, CDHDR and DBTABLOG and then stores them in GRACCHANGELOG table
System Logs: Retrieves all the system logs based on activities performed by the Firefighter ID from transaction SM21 and then stores them in GRACSYSTEMLOG table
Security Audit Log: Retrieves all security audit Logs for the activities performed by the Firefighter ID from transaction SM20 and then stores them in GRACAUDITLOG table
OS Command Log: Retrieves changes to OS commands by the Firefighter ID from transaction SM49 and then stores them in GRACOSCMDLOG table
Note: SAP GRC will retrieve the logs only if they are recorded in the target systems (e.g. S4HANA, ECC etc.)
22. GRC Process Control Tables
HRP1000 - Mitigating Control ID and Short Description
HRP1002 - Mitigating Control Long Description
HRP1001 - Organization Unit, Business Process and Sub process details.
HRP5354 - Mitigating Control Owners & Monitors
E.g. If you want to retrieve the Sub Process details based on a Mitigating Control name, then you can follow below steps:
- Retrieve ‘OBJID’ from table HRP1000 by passing Control short description in the ‘MC_STEXT’ field.
- Pass the 'OBJID' and SCLAS as 'P1' or 'PL' based on Local/Central sub process and retrieve related object ID (SOBJID) from table HRP1001
- Now, use the OBJID retrieved in the above step and extract Sub process description (STEXT) from HRP1000 table
Looking forward for all your inputs in improving this blog by including additional table details (if any missing)
Thanks for reading.
Best Regards,
Madhu Babu Sai (#MJ)
- SAP Managed Tags:
- SAP GRC Access Approver,
- SAP Access Control,
- SAP Access Control for SAP S/4HANA
20 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Assign Missing Authorization Objects
1 -
Bank Reconciliation Accounts
1 -
CLM
1 -
FIN-CS
1 -
Finance
2 -
GRIR
1 -
Group Reporting
1 -
Invoice Printing Lock
2 -
Mapping of Catalog & Group
1 -
Mapping with User Profile
1 -
matching concept and accounting treatment
1 -
Oil & Gas
1 -
Payment Batch Configurations
1 -
Public Cloud
1 -
Revenue Recognition
1 -
review booklet
1 -
SAP BRIM
1 -
SAP CI
1 -
SAP RAR
1 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP Treasury Hedge Accounting
1 -
Z Catalog
1 -
Z Group
1
Related Content
- How to retrieve Amt in Transaction Curr, Amt in Company Code Curr, Amt in Group Curr fields. in Financial Management Q&A
- GRC Tuesdays: Takeaways from the 2024 Internal Controls, Compliance and Risk Management Conference in Financial Management Blogs by SAP
- Budget center setup with cost center allocation in Financial Management Q&A
- Mode of Transport at the Border without GTS in Financial Management Q&A
- Single supplier declaration per transaction - Preference Management in Financial Management Q&A