
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Tracing and debugging LDAP configuration issues
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Tracing and debugging LDAP configuration issues.
Purpose
To correctly isolate LDAP issue via the SAP Managed Cockpit. Turn on LDAP tracking it two locations
to isolate possible issues and some recommendations on possible solutions.
Environment :
- SMP 3.0 SP08 Maincar.
- Microsoft Directory Services
- Open LDAP
- Windows or Linux Operating System.
Issue outline
After configuring the LDAP connection profile in the SAP Managed Cockpit the login fails.

Figure 1.
The following outlined steps will help the Administrator isolate the errors there are two tracing option that
are built in to the SAP Control Center.
The first tracing option is under the logs Server LOGS Settings.
The option is called Security the debug output will be logging to the SMP server log file.
To turn on the debugging go to security under the column Log Level pull down and select debug.
Next top left hand side select or click on Save.
It should look like Figure 2.
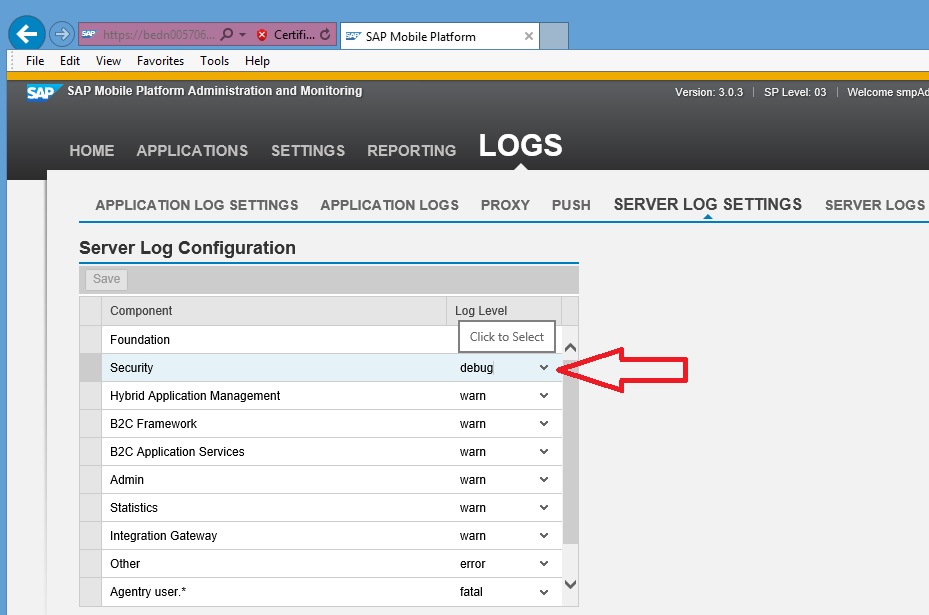
Figure 2.
Next we will want to turn on the LDAP tracing for the Security Profile.
Log in to SAP Managed Cockpit then go to SETTINGS Select your security profile in this scenario we
have created a LDAP connection under the admin. Next check the Enable LDAP Connection Trace.

Figure 3.
After configuring the LDAP connection security profile the login is failing another scenario is you configure
the LDAP connection security profile but the test connection fails.
NOTE: There are two location where the files are stored.
You can access the Server logs thru the SAP Managed cockpit or from the following directory
C:\SAP\MobilePlatform3\Server\log
For the Server LDAP Connection tracing the files are stored in the following directory
C:\SAP\MobilePlatform3\Server\work\tmp.
ERROR 1
2015 11 11 09:47:04#0-500#DEBUG#com.sybase.security.internal.SecSubjectImpl##anonymous#http-bio-
8083-exec-7###Record matching LDAP filter (&(sAMAccountName={0})(objectclass=user)) in the search base
OU=UNITED STATES,OU=North America,DC=test,DC=com was not found.
Verify that the user exists and the bind user has permissions to read the user properties. com.sybase.security.ldap.
LDAPAuthenticationFailureWarning:
Record matching LDAP filter (&(sAMAccountName={0})(objectclass=user))
in the search base OU=UNITED STATES,OU=North America,DC=test,DC=com was not found.
Verify that the user exists and the bind user has permissions to read the user properties.
NOTE the Error:
Record matching LDAP filter (&(sAMAccountName={0})(objectclass=user))
in the search base OU=UNITED STATES,OU=North America,DC=test,DC=com was not found.
Here is the trace to and from the LDAP server.
-> mytown.test.com:389
0000: 30 65 02 01 01 60 60 02 01 03 04 51 43 4E 3D 77 0e...``....QCN=t
0010: 73 6D 69 74 68 2C 4F 55 3D 5F 55 73 65 72 73 2C est,OU=_Users,
0020: 4F 55 3D 43 6F 6E 63 6F 72 64 2C 4F 55 3D 55 4E OU=mytown,OU=UN
0030: 49 54 45 44 20 53 54 41 54 45 53 2C 4F 55 3D 4E ITED STATES,OU=N
0040: 6F 72 74 68 20 41 6D 65 72 69 63 61 2C 44 43 3D orthAmerica,DC=
0050: 73 79 62 61 73 65 2C 44 43 3D 63 6F 6D 80 08 5A test,DC=com..
0060: 61 71 31 32 77 73 78 AbCdEfGHIJKL
<- mytown.test.com:389
0000: 30 84 00 00 00 10 02 01 01 61 84 00 00 00 07 0A 0........a......
0010: 01 00 04 00 04 00 ......
-> mytown.test.com:389
0000: 30 65 02 01 02 60 60 02 01 03 04 51 43 4E 3D 77 0e...``....QCN=t
0010: 73 6D 69 74 68 2C 4F 55 3D 5F 55 73 65 72 73 2C est,OU=_Users,
0020: 4F 55 3D 43 6F 6E 63 6F 72 64 2C 4F 55 3D 55 4E OU=mytown,OU=UN
0030: 49 54 45 44 20 53 54 41 54 45 53 2C 4F 55 3D 4E ITED STATES,OU=N
0040: 6F 72 74 68 20 41 6D 65 72 69 63 61 2C 44 43 3D orthAmerica,DC=
0050: 73 79 62 61 73 65 2C 44 43 3D 63 6F 6D 80 08 5A test,DC=com..
0060: 61 71 31 32 77 73 78 AbCdEfGHIJKL
<- mytown.test.com:389
0000: 30 84 00 00 00 10 02 01 02 61 84 00 00 00 07 0A 0........a......
0010: 01 00 04 00 04 00 ......
-> mytown.test.com:389
0000: 30 2B 02 01 03 42 00 A0 24 30 22 04 16 31 2E 32 0+...B..$0"..1.2
0010: 2E 38 34 30 2E 31 31 33 35 35 36 2E 31 2E 34 2E .840.113556.1.4.
0020: 33 31 39 04 08 30 06 02 02 03 E8 04 00 319..0.......
Note The responce token from the LDAP 319..0 the short meaning is failed
hand shake
Cause:
Adding the OU=UNITED STATES, OU=North America,DC=test,DC=com to the
Role search base caused the issue. The Role search can’t resolved an entry like this. 
Figure 4.
Solution:
Remove the entry from the Role Search Base see Figure 4.
Figure 5.
If you do need a Role Search Base it should look similar to this (&(objectClass=domainDNS)(fSMORoleOwner=*))
Please referrer to your LDAP configuration for Active Directory please see the following link.
http://social.technet.microsoft.com/wiki/contents/articles/5392.active-directory-ldap-syntax-filters...
ERROR 2:
Logging in the SAP Managed Cockpit throws an error invalid user name or password.
With the Enable LDAP client trace enabled we can see the error in the trace.
-> mytown.test.com:389
0000: 30 66 02 01 01 60 61 02 01 03 04 52 43 4E 3D 77 0f...`a....RCN=test
0010: 73 6D 69 74 68 2C 4F 55 3D 5F 55 73 65 72 73 2C ,OU=_Users,
0020: 4F 55 3D 77 61 74 65 72 6C 6F 6F 2C 4F 55 3D 55 OU=mytown,OU=U
0030: 4E 49 54 45 44 20 53 54 41 54 45 53 2C 4F 55 3D NITED STATES,OU=
0040: 4E 6F 72 74 68 20 41 6D 65 72 69 63 61 2C 44 43 North America,DC
0050: 3D 73 79 62 61 73 65 2C 44 43 3D 63 6F 6D 80 08 =test,DC=com..
0060: 5A 61 71 31 32 77 73 78 AbCdEfGHIJKL
<- mytown.test.com:389
0000: 30 84 00 00 00 68 02 01 01 61 84 00 00 00 5F 0A 0....h...a...._.
0010: 01 31 04 00 04 58 38 30 30 39 30 33 30 38 3A 20 .1...X80090308:
0020: 4C 64 61 70 45 72 72 3A 20 44 53 49 44 2D 30 43 LdapErr: DSID-0C
0030: 30 39 30 33 41 39 2C 20 63 6F 6D 6D 65 6E 74 3A 0903A9, comment:
0040: 20 41 63 63 65 70 74 53 65 63 75 72 69 74 79 43 AcceptSecurityC
0050: 6F 6E 74 65 78 74 20 65 72 72 6F 72 2C 20 64 61 ontext error, da
0060: 74 61 20 35 32 65 2C 20 76 31 64 62 31 00 ta 52e, v1db1.
Cause:
In this case there was two issues.
First issue was the user was passing in the wrong user name and password.
The second issue was the configuration for Role Search Base string was incorrect
The admin had OU=_Users OU=North America,DC=test ,DC=com.
Another common cause is not setting the Referral to follow and Authentication to Subtree
and Role Scope to Subtree.
Solution:
Correct the following configuration values
Role Search Base string = OU=North America,DC=test,DC=com
Referral = follow
Authentication = subtree
And Role Scope = Subtree
Now that the adjustments have been made I can successfully log in as
we can see in figure 6.

Figure 6.
Conclusion :
First thjing is to make sure the LDAP configuration parameters are correct by using a LDAP browser.
In this scenario it would of helped in creating the correct values that where needed to configure the
proper LDAP URL. By turning on the Security debug with the addtion of enabling the LDAP client tracing
we where able to isolte and adjust the configuration of the LDAP properties and correct the error messages.
In general it can be diffucult to track down and isolate the meaning of the errors.
with the combination of the two option for tracing and debugging it make it much easier to make adjustment
in the LDAP configuration. The is also very useful when having issues in the configuration of the Certificates
and LDAP so take advantage of logging and debugging.
- SAP Managed Tags:
- Mobile
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
429 -
Workload Fluctuations
1
- Kyma Integration with SAP Cloud Logging. Part 2: Let's ship some traces in Technology Blogs by SAP
- Kyma Integration with SAP Cloud Logging. Part 1: Introduction and shipping Logs in Technology Blogs by SAP
- What's New in the Newly Repackaged SAP Integration Suite, advanced event mesh in Technology Blogs by SAP
- Consume Machine Learning API in SAPUI5, SAP Build, SAP ABAP Cloud and SAP Fiori IOS SDK in Technology Blogs by Members
- Dealing with Unstable Tests in Technology Blogs by SAP
| User | Count |
|---|---|
| 35 | |
| 21 | |
| 17 | |
| 15 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |