
- SAP Community
- Products and Technology
- CRM and Customer Experience
- CRM and CX Blogs by SAP
- Access Control Management: Access restrictions exp...
CRM and CX Blogs by SAP
Stay up-to-date on the latest developments and product news about intelligent customer experience and CRM technologies through blog posts from SAP experts.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Bernd_Fledderma
Active Participant
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-30-2015
3:47 PM
Welcome to the blog series on access control management in SAP Hybris Cloud for Customer (C4C). The series discusses various access control topics in C4C. The goal of this blog series is to provide a complete overview on the access control concept and capabilities in C4C and to let you know on how it works in detail.
Here are the blogs of that series:
- Basics of access control and business roles
- Access Control Management: Access restrictions explained – Access Context
- Access Control Management: Access restrictions explained – Restriction Rules (this blog)
- Access Control Management Example: Global versus local admin
- Access Control Management Example: Access forwarding
- How to analyze access control issues
- How to analyze access control issues – Check User’s Authorization
- Special Access Control Topics
The translation of the setup of the access restrictions defined in an unspecific role to the access restrictions of a specific user is handled through the restriction rules.
Example:
You have created a role for sales representatives. This role provides access to the work center views Account, Contacts, Opportunity and Sales Quote. You want to assign this role to all of your global sales representatives in the different organizations. By choosing the restriction rule “Assigned Territories and Employees (for Managers)”. The system will automatically provide access restriction set up to the accounts where a user is assigned in the account team or in the territory team”. As the system generates the access restriction for the user automatically it is not necessary to create a role for each individual territory.
How does the system actually translate the access restrictions for the individual business users?
Sales Representative Nils Watt
Nils is a sales representative of the BFT Company Inc. Organizationally he is assigned to the corporate org unit of the company. He also is a member of the territory “Germany” which has further sub territories assigned. Nils user has the role “BFT DE SALES ASSISTANT” assigned. For the Accounts work center view the access restriction rule “Assigned Territories and Employees (for Managers)” is selected.
Nils Watt - Organizational assignment

Nils Watt – Territory assignment

Nils Watt User Role
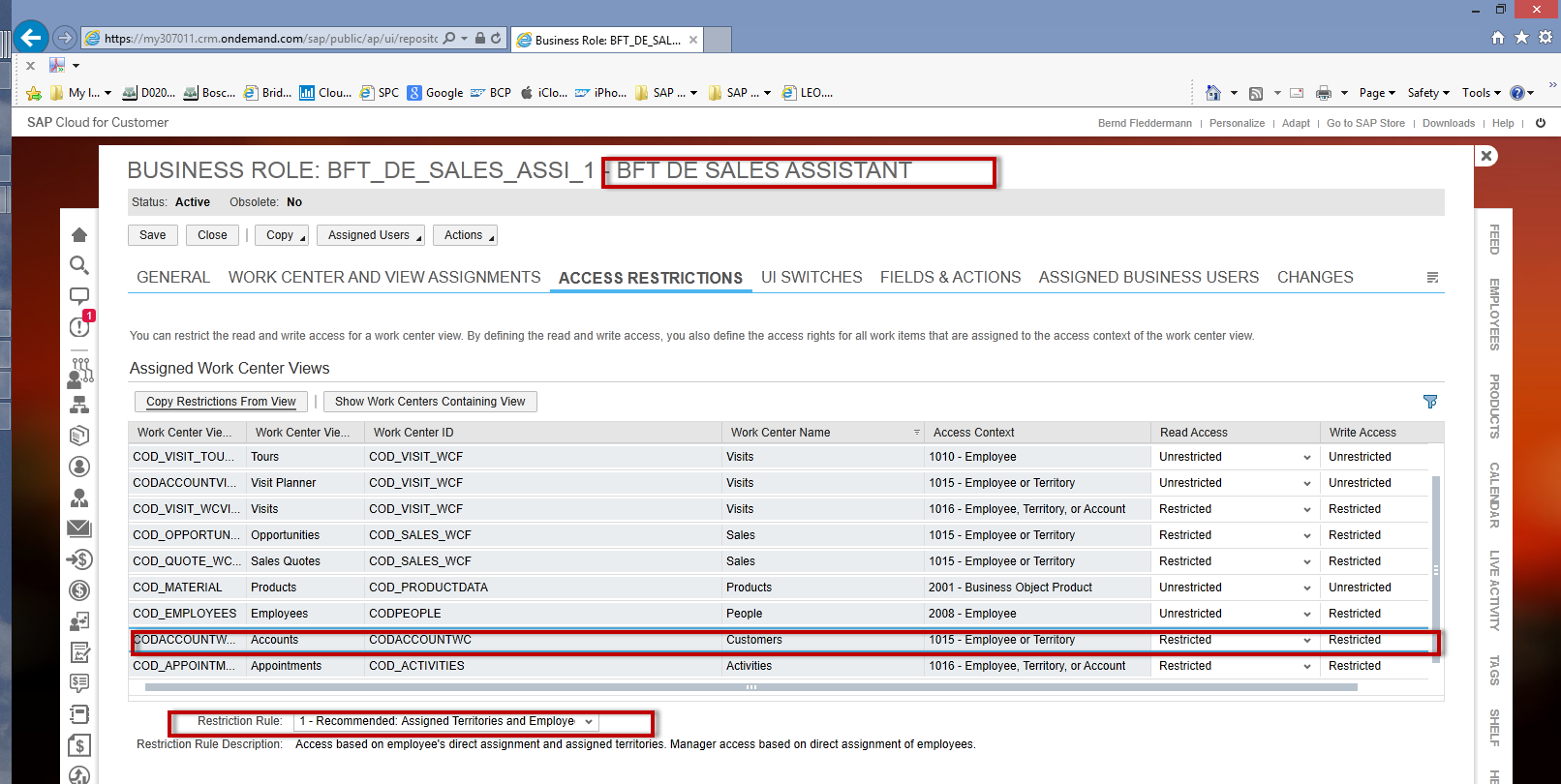
The following screen shots shows access rights for the account work center view of the user of Nils Watt. These access rights were automatically generated:
- As Nils is assigned as an employee (and not as a Manager) to his organizational unit. He has access granted only for those accounts (and contacts) where he is assigned as a member of the account team (no access to accounts of other account team members!).

- As Nils is assigned to the territory Germany he has access to all accounts which are assigned to this territory but in addition also to all the accounts assigned to its sub territories.

Nils’ access is a combination of the employee part of his access context (--> Accounts where he is directly assigned as an account team member) and the territory part of his access context (-> Accounts which are assigned to a territory (and sub territory) he is a member of.
The restriction rule of the role which is assigned to Nils’ user has dynamically generated access rights. Dynamically means that a change of his territory assignment will lead to a change of his territory related access rights.
Please note that there are some situation where the access for the users of a role must explicitly be update (e.g. the sales area in the employee is changed). In those cases enter the relevant role --> assigned Users --> Update Users. This action will trigger a background job which set the access rights of the assigned users according to their current territory or sales area assignment. The user update of a role is also an action you can do in case the access control does not provide expected access results (in my blog How to analyze access control issues I will provide some more details on how to proceed in case of issues)
Sales Manager Bodo Mann
Bodo is the manager of the BFT Company Inc. Organization. Bodo’s user has the same role “BFT DE SALES ASSISTANT” assigned as for his employee Nils. Bodo is not assigned to any territory:
- As a manager Bodo has access to all accounts where employees of his own organizational unit and sub units are assigned in the account team. Please note that the organizational unit must be flagged as a sales unit (functional unit sales) to be effective in the access restrictions.

Does Bodo also has access to an account where his employee Nils Watt can access because he is member of the territory team of the account but not member of the account team?
The answer is no! The employee part of the access context only considers the organizational assignment of the employees of the manager.
When setting up a role I recommended to use access restriction rules rather than defining specific rules. This might not always be possible for all customer use cases but using restriction rules can reduce the number of different business roles as the same role can be used for users of different organizations, territories etc. By this maintenance and administration effort on handling the roles can be reduced.

The restriction rule can be maintained in the “Access Restriction” by individual work center view. It is depending on the access context of the work center view/business object. In the screen shot above you see the available restriction rules for the access context 1015 – Employee or Territory or Sales Data. Other work center views/business objects which are assigned to different access contexts will provide a different set of restriction rules.
The restriction rules are defined by the standard and cannot be changed or extended customer specifically.
I have attached an XLS with a table is intended to provide an overview on our current restriction rule setup
Legend
- Empl.: The difference between Employee and User is that if the employee is a manger, then for employees also the OrgUnits of the manager are considered (the manager gets access for all employees in his/her OrgUnits). For both managers and employees the own user is added.
- Workforce: Access based on the employees supervised by the user in the relationship hierarchy
- User: user only is added, even for managers
- Org: OrgUnits of the user are added. The function of them is derived from the access context
- Territory: Territories of the user
- Partner: only meaningful for users that are partner contacts. The partner of the partner contact
- SalesArea: the sales areas maintained in the employee's master data
- Sorg+Dist: sales organization combined with all distribution channels in the system.
please find more details on the restriction rules under the following link:
https://www.sap.com/documents/2018/10/347453e7-217d-0010-87a3-c30de2ffd8ff.html
- SAP Managed Tags:
- SAP Cloud for Customer add-ins
54 Comments
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Business Trends
270 -
Business Trends
11 -
chitchat
1 -
customerexperience
1 -
Event Information
256 -
Event Information
18 -
Expert Insights
30 -
Expert Insights
50 -
Life at SAP
133 -
Life at SAP
1 -
Product Updates
666 -
Product Updates
24 -
SAP HANA Service
1 -
SAPHANACloud
1 -
SAPHANAService
1 -
Technology Updates
453 -
Technology Updates
15
Related Content
- Leveraging Backoffice Roles: Effective Restriction of Backoffice Access in SAP Commerce Cloud in CRM and CX Blogs by SAP
- SAP Premium Engagement Session 'A new SAP UX experience utilizing the BTP platform', April 11, 2024 in CRM and CX Blogs by SAP
- Opportunity Access restrictions based on Product Category in CRM and CX Questions
- Introduction to Permission Marketing in CRM and CX Blogs by SAP
- What is planned for the 2402 release of SAP Variant Configuration and Pricing? in CRM and CX Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |