
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Enabling SSL (HTTPS) on SAP Gateway
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Enabling SSL (HTTPS) on SAP Gateway
Topics
- CommonCryptoLib
- Maintain Instance Profile Parameter
- Maintain Certificates in STRUST
- Testing OData Service with HTTPS connection
- Proper System Certificate Signing
Introduction
There are already many guides out there how to configure the SAP Netweaver Gateway so that you can use HTTPS connections. Anyway this here is my documentation, it should also serve as a documentation for myself.
In the first step the netweaver gateway needs to be setup for https/ssl.
So that you can call e.g. OData services by calling
https://gateway:port/sap/opu/...
Transport Layer Security on SAP NetWeaver AS for ABAP
CommonCryptoLib 8
Successor of SAPCryptoLib
Inside NetWeaver 74X SAPCRYPTOLIB is available in the new variant CommonCryptoLib 8
Following steps are based on SAP Note: 510007 - Setting up SSL on Application Server ABAP
http://service.sap.com/sap/support/notes/510007
Before adding and modifiying necessary profile parameter, we should check
if the CommonCryptoLib and its variable is available
SE38 and execute report RSPARAM

Check if $(SAPCRYPTOLIB) is defined

You can also check if you find the sapcrypto files on the file system
(e.g. on Windows sapcrypto.dll)

Maintain Instance Profile Parameter
Go to transaction RZ10 and open the Instance profile with “Extended
maintenance”
(Info: You also can check a single parameter in transaction RZ11)

| Note: SAP system starts in a sequence:
Parameters in Default profile are the ones which are applicable to all instances, i.e. a set of common system parameters for e.g. message server hostname... Instance profiles contains parameters that only take effect for that particular instance for e.g. number of dialog work processes If a parameter is defined in both the profiles, then the value of the parameter in instance profile will be effective for that instance. |
Make sure following values are set (if not set, add them as new parameter)
Parameter | Value | Description |
ssf/name | SAPSECULIB | CommonCryptoLib |
ssf/ssfapi_lib | $(SAPCRYPTOLIB) | CommonCryptoLib |
sec/libsapsecu | $(SAPCRYPTOLIB) | CommonCryptoLib |
ssl/ssl_lib | $(SAPCRYPTOLIB) | CommonCryptoLib |
icm/server_port_1 | PROT=HTTPS, PORT=8200 | HTTPS Port |
icm/HTTPS/verify_client | 1 | Permit use of client |
icm/host_name_full | $(SAPLOCALHOST).dhcp.wdf.sap.corp | Full qualified domain name |
login/certificate_mapping_rulebased | 1 | Use dynamic mapping |
If variable $(SAPCRYPTOLIB) is not set (verified in last step), use $(DIR_EXECUTABLE)$(DIR_SEP)$(FT_DLL_PREFIX)sapcrypto$(FT_DLL) instead
icm/server_port_X = PROT=HTTPS,PORT=<TCP port number for HTTPS>
Replace the X with the number of configured ports (usually https port is 1)
Set icm/HTTPS/verify_client for handling user certificates, it can be set to 0 (suppress) / 1 (default) (permit) or 2 (enforce)
The value login/certificate_mapping_rulebased will enable the use of dynamic mapping through transaction CERTRULE, might be not supported by old
netweaver systems. By setting this parameter to 1 old entries entered manually into table VUSREXTID will not be used any longer.

Note! After changing the profile parameter you need to restart the
netweaver system
Maintain Certificates in STRUST
Go to transaction STRUST
Right click on “SSL server Standard” and choose “Create”

Enter values for your default certificate Organizational Unit and Company Name. Do not change the asterix ( * ) inside name. Best Practice to create at first a default wildcard certificate. Use a key length of 2048. The value in field CA should match your CA’s values. Same CA that will be used later to sign this certificate.

I will use my own CA for this testing…
My CA certificate:

The instance specific PSEs will be created automatically. In this test landscape I only have one instance.


Now it should be possible already to access your server via browser and https:

Testing OData Service with HTTPS connection
We can enable the ping service for further testing. Go to transaction SICF and enable the node /sap/bc/ping

Test Ping Service in browser by accessing https://<gw server>:<https port>/sap/bc/ping
You should get asked for user and password…

After authenticating we can see a success screen

Proper System Certificate Signing
Until now the HTTPS certificate is still self-signed in STRUST we can create a certificate signing request (copy it into clipboard or export it as csr file), that can be signed by a CA.

Because I am using XCA (freeware tool) to simulate my own CA, I can import the certificate request there and sign it. I exported the CSR response “PEM
with Certificate chain”. This will also include the public certificate of the signing CA.
Tip:
I prefer setting also the Issuer Alternative Name to IP:<ip address of server> . By doing so the browser will be also trusting the certificate if the ip adress instead of the fqdn is called).
Finally import the certificate response in STRUST

After that you should see, that the CA is now the new issuer of the server’s certificate.
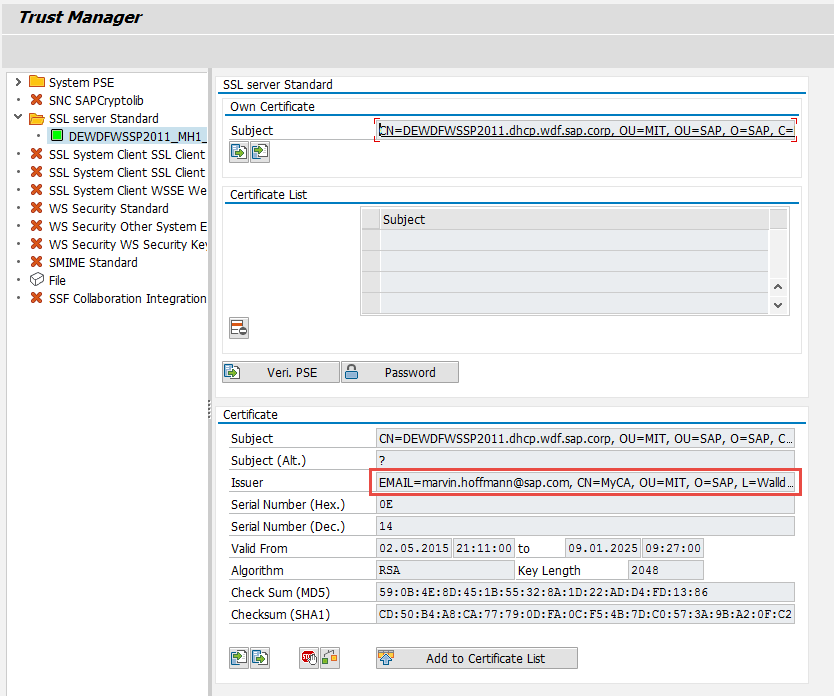
Save it. And call the ping service again inside your browser. If you have imported the CA certificate into your system store (under Trusted Certificate Authorities), you should see that now the browser is trusting your server.

The SAP Gateway is now prepared for proper HTTPS communication ...
- SAP Managed Tags:
- SAP Gateway
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
344 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
423 -
Workload Fluctuations
1
- Start page of SAP Signavio Process Insights, discovery edition, the 4 pillars and documentation in Technology Blogs by SAP
- What’s new in Mobile development kit client 24.4 in Technology Blogs by SAP
- How to host static webpages through SAP CPI-Iflow in Technology Blogs by Members
- New Machine Learning features in SAP HANA Cloud in Technology Blogs by SAP
- Kyma Integration with SAP Cloud Logging. Part 2: Let's ship some traces in Technology Blogs by SAP
| User | Count |
|---|---|
| 40 | |
| 25 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |