
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- How to Connect Your Cloud Applications with Your C...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-02-2015
3:08 PM
Overview
Most companies today strive to integrate the cloud into their environment. That way the company consumers can use the applications running in the cloud from any location and without any additional development. However, most companies do not want to expose all their user data in the cloud for security reasons. With the new functionality that we offer, users registered in the corporate user store are able to access cloud applications without the need for the identity information to be replicated. Furthermore, those users can log on with their corporate credentials.
For this scenario, we use SAP Cloud Platform Identity Authentication service (former SAP Cloud Identity service) for authentication and single sign-on to cloud applications. Identity Authentication can be configured to use information from the corporate user store.
In this blog, we use Microsoft Active Directory as a corporate user store, but this scenario is applicable for other user stores. For more information about the other scenarios, see Configure Connection to a Corporate User Store in Corporate User Store.

Prerequisites
- You have an SAP Cloud Platform account on a productive landscape.
- You have installed the SAP Cloud connector inside your corporate network.For more information, see Installing the Cloud Connector.Note: Make sure you have installed the right JVM that is referenced as a JAVA_HOME variable.
Configure SAP Cloud Platform
In this setup, the administrator’s name is Donna Moore with a user ID I000001. Donna’s SAP Cloud Platform account is named consumer_account. Donna is configuring connection to Microsoft Active Directory with servusr service user and the following user and group subtrees: DC=sec,DC=company,DC=boston. She is also accessing the active directory server with a samplehost:389 host. The service user is necessary for the Cloud connector to connect with the Microsoft Active Directory, and the subtree paths are needed for the system to know where to find the corporate users.
- In SAP Cloud Platform cockpit, choose Services in the navigation area, select the Identity Authentication Add-On tile, and choose Enable in the detailed view of the service.This will enable the extension service of Identity Authentication named proxy and provided by an SAP Cloud Platform account named sci.Note: If you don't see the Identity Authentication Add-On tile in the cockpit, you need to create an Incident with a subject Enable Corporate User Store Feature on SAP Support Portal under the component BC-IAM-IDS. You have to provide information about your SAP Cloud Platform account name and data center.
- Go to OAuth –> Clients and register a client for the subscribed proxy application provided by the sci account.
 For more information about this procedure, see Registering an OAuth Client.Note: Since Identity Authentication will create the subscription to the proxy application, the Prerequisites section in the respective document is not relevant for the current scenario.
For more information about this procedure, see Registering an OAuth Client.Note: Since Identity Authentication will create the subscription to the proxy application, the Prerequisites section in the respective document is not relevant for the current scenario.
- For Subscription, select sci/proxy.
- For Authorization Grant, select Client Credentials.
- Connect the Cloud connector with your SAP Cloud Platform account.
- If you haven't used your cloud connector before, see Initial Configuration.
- If you have used your cloud connector before, you can start the configuration from Set up Connection Parameters and HTTPS Proxy.

- Configure the connection between the Microsoft Active Directory user store and the cloud connector.Specify the settings described in Configuring User Store in the Cloud Connector.Note: The Prerequisites section in the document describing the configuration is already configured for the proxy application, and you should proceed with the configuration steps. The User Name field must be in the <service_user_name>@<domain> format. For the User Path and Group Path fields, specify the LDAP tree that contains the users and groups, respectively.

- Optionally you can change the default attributes or include additional attributes.For more information, see step 6 (optionally, change the default attributes or include additional attributes) in the section Configure SAP Cloud Platform When Connecting to an LDAP User Store.
Configure Identity Authentication Service
- If it is the first time you use Identity Authentication, open your activation email. Activate your Identity Authentication account and access the administration console.Note: After the account activation, you are automatically redirected to the administration console.The URL of the administration console has the https://<tenant ID>.accounts.ondemand.com/admin pattern. The tenant ID is an automatically generated ID by the system. The first administrator created for the tenant receives an activation e-mail with a URL in it. This URL contains the tenant ID.
- Choose the Tenant Settings tile in the administration console.

- Choose the Corporate User Store list item.

- Select your SAP Cloud Platform account's data center, enter your SAP Cloud Platform consumer account, and the OAuth client ID and secret.Note: The Client ID and Client Secret fields in the administration console for Identity Authentication service have to match the ID and secret registered on SAP Cloud Platform under the OAuth Settings tab for your consumer account.The Account field in the administration console for Identity Authentication service has to match your SAP Cloud Platform account name.
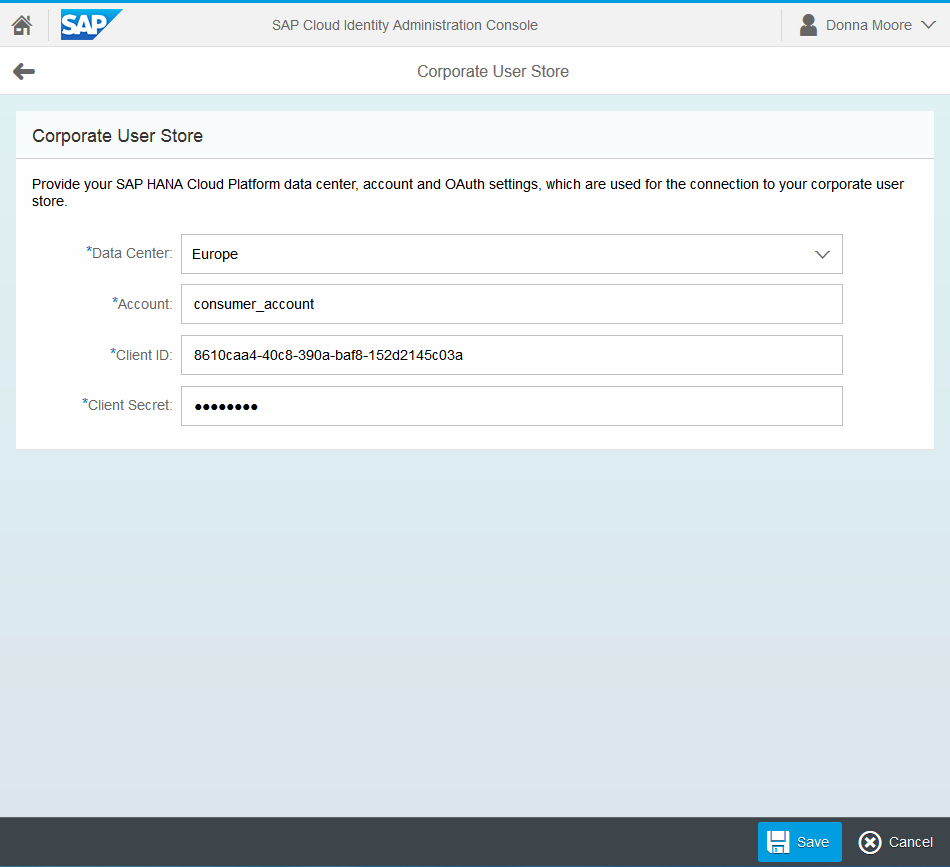
- Save your settings.If the operation is successful, you receive the message Connection settings saved.
- Log on to an application using Identity Authentication service with a Microsoft Active Directory user and verify that the authentication is successful. Note: Make sure that this user does not exist in the user store of Identity Authentication, and the user has an email set in Microsoft Active Directory.
- SAP Managed Tags:
- SAP Business Technology Platform
19 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
281 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
Related Content
- SAP BTP, Kyma Runtime internally available on SAP Converged Cloud in Technology Blogs by SAP
- Corporate Git Setup on SAP BTP versus connecting to Corporate Git directly from SAP BAS in Technology Q&A
- SAP HANA Cloud Vector Engine: Quick FAQ Reference in Technology Blogs by SAP
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- What’s New in SAP Analytics Cloud Release 2024.08 in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 13 | |
| 10 | |
| 10 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |