
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by Members
- Security Process (Functional) – Add, Modify, and R...
Financial Management Blogs by Members
Dive into a treasure trove of SAP financial management wisdom shared by a vibrant community of bloggers. Submit a blog post of your own to share knowledge.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Former Member
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-13-2015
5:55 PM
Before You Begin
Who Should Use this Document?
This document is intended for technical and business resources who have an interest in the security process for the SAP BPC solution.
How Should You Use this Document?
This document details the process flow and other related content associated with the process and approvals of managing the
security for SAP BPC content.
Add a New User
Process Flow
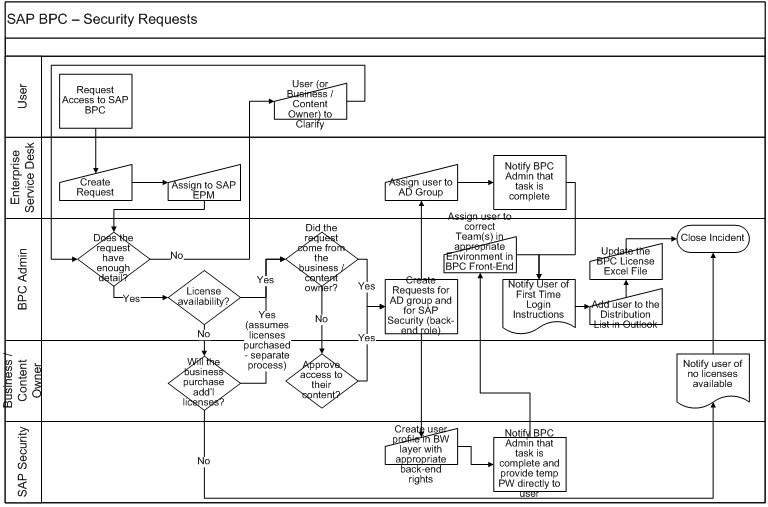
Initiating and Approving the Request
- The business makes a request to have access to either SAP Business Planning and Consolidation (BPC) and/or the EPM Add-In for MS Excel
- The user, their manager, a peer, or a content owner may make the request
- The request should come through the Enterprise Service Desk (ESD) – there is no formal document or form required
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- The environment in BPC the user needs access to
- Where the user can access data (data access profile)
- What the user can do (task profile)
- Often times, the easiest thing might be to communicate whose rights to mirror
- Enough information to ensure the correct user is being added to the system
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- The ESD creates a ticket and routes it to the SAP Enterprise Performance Management group.
- The BPC Administrator reviews the request and clarifies any questions with the business.
- At this point, the BPC Administrator determines whether there are any licenses available to extend.
- In addition, the BPC Administrator gains approval from the content owner in the business
Processing the Request
- Once all required approvals are obtained, the BPC Administrator proceeds with processing the request
- The BPC Administrator creates two new, related tickets:
- One to the ESD to assign the new user to the appropriate Active Directory (AD) group for access to the Citrix connection for the EPM Add-In for MS Excel
- ESD notifies the BPC Administrator that their
task is complete
- ESD notifies the BPC Administrator that their
- One to SAP Security to add the user to the production instance under one of three profiles in the back-end so the BPC Administrator can assign the user to the appropriate rights in the front-end
- Z1:BPC_GENERAL_ALLUSER – for most all business users
- Z3:BPC_DEVELOPER – requires above and adds the ability to run ZUJBR (business initiated backup in BPC but not restore
functionality) - Z4:BPC_ADMINISTRATOR – for IT resources who support and develop in the BPC solution
- SAP Security notifies the BPC Administrator that their task is complete
- One to the ESD to assign the new user to the appropriate Active Directory (AD) group for access to the Citrix connection for the EPM Add-In for MS Excel
- Once SAP Security adds the user to the back-end, the BPC Administrator can pull the user in to the front-end security in the BPC web administration and assign the user to the appropriate team(s).
Communications and Closing the Request
- SAP Security notifies the user of their temporary password, directly
- The BPC Administrator notifies the new user that the security request has been completed and provides first time user instructions for changing their temporary password and accessing the content via the web and the EPM Add-In for MS Excel via Citrix
- The BPC Administrator will add the user to the appropriate Outlook distribution list:
- *SAP_BPC-KeyStakeholders – used to communicate to power users and content owners in the solution
- *SAP_BPC-Users – used to communicate to all users from report viewers only to business developers and their managers
- The BPC Administrator will update the BPC Security spreadsheet for managing licenses.
- The BPC Administrator will close out the original Remedy incident associated with the user’s request for access to SAP BPC / EPM Add-In for MS Excel
- SAP Security will close out the Remedy incident associated with adding the user to the back-end of SAP BPC
- ESD will close out the Remedy incident associated with adding the user to the AD group
Modify an Existing User
Process Flow

Initiating and Approving the Request
- The business makes a request to modify access to either SAP Business Planning and Consolidation (BPC) and/or the EPM Add-In for MS Excel
- The user, their manager, a peer, or a content owner may make the request
- The request should come through the Enterprise Service Desk (ESD) – there is no formal document or form required
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- The environment in BPC the user needs access modifications to
- Modifications related to where the user can access data (data access profile)
- Modifications related to what the user can do (task profile)
- Often times, the easiest thing might be to communicate whose rights to mirror
- Enough information to ensure the correct modification(s) is(are) being made to the system
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- The ESD creates a ticket and routes it to the SAP Enterprise Performance Management group.
- The BPC Administrator reviews the request and clarifies any questions with the business.
- The BPC Administrator gains approval from the content owner in the business
Processing the Request
- Once all required approvals are obtained, the BPC Administrator proceeds with processing the request
- The BPC Administrator possibly creates one new, related ticket:
- One to SAP Security to modify the user’s access in the production instance, provided the modification to
rights in the front-end warrants a change in the back-end. This is rare, and would typically only happen in a case where a business user is
changing to/from the Business Developer Role from the General User Role.- Z1:BPC_GENERAL_ALLUSER – for most all business users
- Z3:BPC_DEVELOPER – requires above and adds the ability to run ZUJBR (business initiated backup in BPC but not restore functionality)
- Z4:BPC_ADMINISTRATOR – for IT resources who support and develop in the BPC solution
- SAP Security notifies the BPC Administrator that their task is complete
- One to SAP Security to modify the user’s access in the production instance, provided the modification to
- Once SAP Security modifies the user in the back-end, the BPC Administrator can modify the user’s rights in the front-end security in the BPC web administration by modifying the user assignment to the appropriate team(s).
Communications and Closing the Request
- The BPC Administrator notifies the user that the security modification has been completed.
- The BPC Administrator will modify the user enrollment for the appropriate Outlook distribution list, if necessary:
- *SAP_BPC-KeyStakeholders – used to communicate to power users and content owners in the solution
- *SAP_BPC-Users – used to communicate to all users from report viewers only to business developers and their managers
- The BPC Administrator will update the BPC Security spreadsheet for managing licenses, if necessary.
- The BPC Administrator will close out the original Remedy incident associated with the user’s request to modify access to SAP BPC / EPM Add-In for MS Excel
- SAP Security will close out the Remedy incident associated with modifying the access for the user in the back-end of SAP BPC
Delete a User
Process Flow

Initiating and Approving the Request
- The business makes a request to have a user removed from SAP Business Planning and Consolidation (BPC) and/or the EPM Add-In for MS Excel
- The user, their manager, a peer, or a content owner may make the request
- The request should come through the Enterprise Service Desk (ESD) – there is no formal document or form required
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- Enough information to ensure the correct user is being removed from the system
- The request, however, should denote the following things, although the content owner(s) may need to provide assistance
- The ESD creates a ticket and routes it to the SAP Enterprise Performance Management group.
- The BPC Administrator reviews the request and clarifies any questions with the business.
Processing the Request
- Beyond clarifying / confirming the request to remove a user, there are no approvals required.
- The BPC Administrator proceeds with processing the request.
- The BPC Administrator creates two new, related tickets:
- One to the ESD to remove the user from the appropriate Active Directory (AD) group for access to the Citrix connection for the EPM Add-In for MS Excel
- ESD notifies the BPC Administrator that their task is complete
- One to SAP Security to remove or disable (consistent with SAP Security’s current processes) the user from the production instance
- SAP Security notifies the BPC Administrator that their task is complete
- One to the ESD to remove the user from the appropriate Active Directory (AD) group for access to the Citrix connection for the EPM Add-In for MS Excel
- Once SAP Security removes the user from the back-end, the BPC Administrator can confirm that the user has been removed from the front-end security in the BPC web administration.
Communications and Closing the Request
- The BPC Administrator will remove the user from the appropriate Outlook distribution list(s):
- *SAP_BPC-KeyStakeholders – used to communicate to power users and content owners in the solution
- *SAP_BPC-Users – used to communicate to all users from report viewers only to business developers and their managers
- The BPC Administrator will update the BPC Security spreadsheet for managing licenses.
- The BPC Administrator notifies the Content Owner of the license recovery
- The BPC Administrator will close out the original Remedy incident associated with the request to remove the user from SAP BPC / EPM Add-In for MS Excel
- SAP Security will close out the Remedy incident associated with removing the user from the back-end of SAP BPC
- ESD will close out the Remedy incident associated with removing the user from the AD group
- SAP Managed Tags:
- SAP Business Planning and Consolidation, version for SAP NetWeaver,
- Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Assign Missing Authorization Objects
1 -
Bank Reconciliation Accounts
1 -
CLM
1 -
FIN-CS
1 -
Finance
2 -
GRIR
1 -
Group Reporting
1 -
Invoice Printing Lock
2 -
Mapping of Catalog & Group
1 -
Mapping with User Profile
1 -
matching concept and accounting treatment
1 -
Oil & Gas
1 -
Payment Batch Configurations
1 -
Public Cloud
1 -
Revenue Recognition
1 -
review booklet
1 -
SAP BRIM
1 -
SAP CI
1 -
SAP RAR
1 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP Treasury Hedge Accounting
1 -
Z Catalog
1 -
Z Group
1
Related Content
- GRC Tuesdays: Takeaways from the 2024 Internal Controls, Compliance and Risk Management Conference in Financial Management Blogs by SAP
- Digital Banking Add-on Package for RISE and GROW with SAP in Financial Management Blogs by SAP
- GRC Process Control: How CCM can be leveraged to monitor HANA Databases in Financial Management Q&A
- Payment Batch Configurations SAP BCM - S4HANA in Financial Management Blogs by Members
- SAP ECC Conversion to S/4HANA - Focus in CO-PA Costing-Based to Margin Analysis in Financial Management Blogs by SAP