
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Enabling cookie based SSO Authentication for BEP (...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Use Case:
To access SAP Gateway exposed services via SMP 3.0 using SSO Cookie based authentication
Pre-requisites:
SAP Gateway system is capable of handling cookies eg: MYSAPSSO2
Steps to Create MYSAPSSO2 Scenario
I) Enable SMP to access the backend https url:
- Open File->Open Keystor fFile in portecle
Tool and go the Location where the smp_keystore.jks file is Located. i.e. SMP
server->Configurations and click ok to open the
Keystore.jks, Password for the keystore is "changeit".
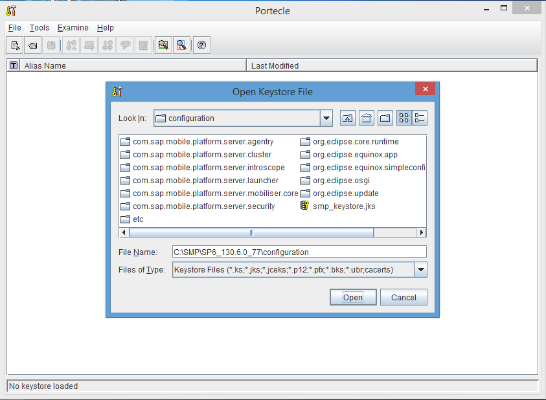
2) Go to Tools-> Import Trusted Certificate
and select the Back End System's Certificate from your system and click on
import

3) Click on the ok and yes buttons as shown below.


4) Enter the Alias Name for the
Certificate which is getting imported
5) Save the Keystore in the
portecle Tools once the certificate is imported. Otherwise the imported
certificate will not be Reflected in SMP server's Configurations.

II) SMP Gateway Cockpit Steps:
- Log on to the SMP Admin Cockpit https://<host>:8083/gateway/cockpit and go to the Destinations-> New
Destination
Provide the Destination Name, select destination type as HTTP, provide Destination URL, and Select Authentication
Type as SSO Mechanism

Click on Add button to select from various SSO Mechanisms.
Select Technical User(Basic) authentication as authentication mechanism,
and click on Save button.

Different SSO Mechanisms at the Gateway cockpit is mainly used to test the destination connection and to initially test
the services in the cockpit.
The security profile created at the SMP Admin will overwrite the destination configurations created at the gateway
cockpit.
In a productive scenario we need to consume the services exposed in gateway cockpit through SMP.
For different SSO Mechanisms refer to the link
http://help.sap.com/saphelp_smp306svr/helpdata/en/7c/2dd0d470061014a8bfb9194fa26274/content.htm
Once the destination is created, in the https://<host>:8083/gateway/cockpit Click on register button,
provide the destination created and search for the service required to be
registered.

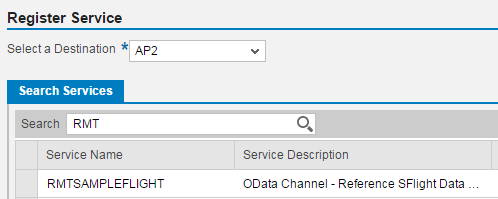
With this we have registered the service in gateway cockpit. If we need to access this service by cookie based SSO
mechanism through SMP follow the steps mentioned in the next section.
III) SMP ADMIN Cockpit Steps
1. Log on to the SMP Admin Cockpit https://<host>:8083/Admin and go to the Settings-> Security
Profile tab.
2. Create a security profile with HTTP/HTTPS Authentication and provide the URL of the Back end System from where odata
service is hosted and MYSAPSSO2 Cookie is enabled. Click on Save as Shown Below.


3. In the SMP Admin Cockpit https://<host>:8083/Admin create the application for the service
document url exposed in gateway cockpit as shown in screen shots below:


Provide the odata service exposed through gateway cockpit, and mark the service as internal.


Once this is done, application is ready to be consumed.
IV) Onboarding through REST CLIENT
Onboard to the created application in the REST client/Mobile Application though a
device
Onboarding URL:
http://<host>:8080/odata/applications/latest/<application id created in SMP>/Connections
Onboarding Headers:
Content-Type: application/xml
x-smp-appcid: <application1>
Onboarding Post Body:
<?xml version='1.0' encoding='utf-8'?>
<entry xmlns="http://www.w3.org/2005/Atom"
xmlns:d="http://schemas.microsoft.com/ado/2007/08/dataservices"
xmlns:m="http://schemas.microsoft.com/ado/2007/08/dataservices/metadata">
<title type="text"/>
<updated>2012-06-15T02:23:29Z</updated>
<author>
<name/>
</author>
<category
term="applications.Connection"
scheme="http://schemas.microsoft.com/ado/2007/08/dataservices/scheme"/>
<content type="application/xml">
<m:properties>
<d:DeviceType>IOS</d:DeviceType>
<d:DeviceModel m:null="true" />
</m:properties>
</content>
</entry>
Onboarding Operation: POST
While onboarding it will initially ask for the user details, and for the subsequent requests it will use the Cookie we have configured.
After onboarding the entities of the application can be accessed via the url
http://<host>:8080/ <application id created in SMP>/<entites>
Headers:
Content-Type: application/xml
x-smp-appcid: <application1>
- SAP Managed Tags:
- SAP Mobile Platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
65 -
Expert
1 -
Expert Insights
178 -
Expert Insights
280 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
- SAP Partners unleash Business AI potential at global Hack2Build in Technology Blogs by SAP
- It’s Official - SAP BTP is Again a Leader in G2’s Reports in Technology Blogs by SAP
- Unify your process and task mining insights: How SAP UEM by Knoa integrates with SAP Signavio in Technology Blogs by SAP
- SAP HANA Cloud Vector Engine: Quick FAQ Reference in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform - Blog 7 in Technology Blogs by SAP
| User | Count |
|---|---|
| 13 | |
| 10 | |
| 10 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |