
- SAP Community
- Groups
- Interest Groups
- Welcome Corner
- Blog Posts
- Social Login on SCN (and elsewhere) - a few remind...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
I saw charles.carney 's post this morning (through a tweet by gali.klingschneider ) which talks about LinkedIn now being the third available Social Login option on SCN (after Twitter and Facebook).

Being the security scarecrow here this reminded me of LinkedIn being hacked and having all their passwords exposed, but that was a while ago and I'm sure that has been properly fixed by now. Still, it's a good time to reflect on trust and security in social networks.
Every time you chose to login to a site you're handing over trust to a third party to use your identity to do stuff on your behalf, sometimes even without you being actively involved in the process. You usually want that, stuff like sending off a tweet every time you post a new image to InstaGram.
By the way, the authorizations work both ways - you allow the target application to be accessed with your social network credentials, but you also allow the host application to use your social network information. These authorizations are part of the initial account linking process.
Examples:
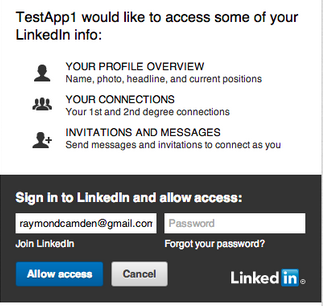

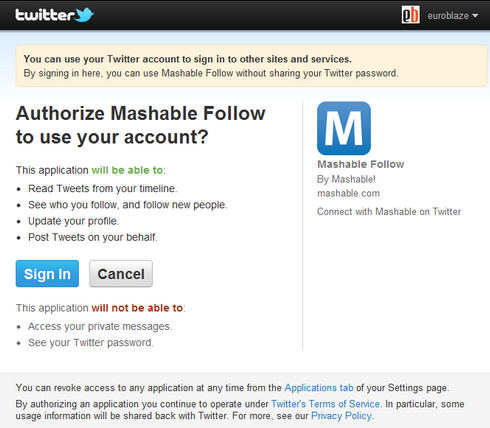
That's usually just fine, i.e. you want that, but we tend to forget what we granted after a while, and sometimes this leads to surprises. As a little awareness excercise, you can see which authorizations you already granted. Please go to each of the following links (provide you use that social network) and look at the apps, and consider if you still use the app, or if you even were aware you granted those privileges:
- LinkedIn https://www.linkedin.com/secure/settings?userAgree=&goback=%2Enas_*1_*1_*1
- Twitter https://twitter.com/settings/applications
- Facebook https://www.facebook.com/settings?tab=applications
Interesting, isn't it?
Next critical question: Are you using different passwords on each of your social networks? Because if you don't, if one gets exposed someone might use it to log on to another social network which in turn you may be using as a login to SCN or elsewhere.
Using different passwords may sound cumbersome (and it is), but it's well worth it. I recommend using a password manager that integrates into your browser like LastPass or 1Password to make it easier; they will also assist you in generating secure passwords.
In an SAP context, similar questions arise when you link your AS Java to Windows login. We did this for many customers with GRC AccessControl 5.3 scenarios. It's incredibly simple to set up, but it needs follow-up activities in the organisation:
- Your Windows password now works as an SAP logon. Do your password rules take that into account (i.e. are your Windows passwords strong enough)?
- People may share Windows passwords for whatever purpose - this is no longer acceptable if it suddenly also grants you access to, say, ESS scenarios.
- Password reset procedures may be rather lax for Windows passwords, which will need to change. I've seen many organisations where you could get your Windows password reset to a (well known) generic one by calling a help desk. Help desk staff needs to be made aware of the extended usage of Windows passwords.
So, to summarize: Social Login and identity federation are good and useful, but they need raised awareness also (or specifically) by the average user about the security side effects.
Related Posts:
http://scn.sap.com/community/security/blog/2012/06/07/on-passwords
http://scn.sap.com/community/security/blog/2012/08/08/initial1
Feel free to share your biggest AHA-moments when you looked at the list of linked applications in your social networks n the comments!
- SAP Managed Tags:
- SAP Community
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| User | Count |
|---|---|
| 9 | |
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |