
- SAP Community
- Groups
- Interest Groups
- Application Development
- Blog Posts
- How to Protect AS ABAP & AS Java Against BEAST Att...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The BEAST attack on SSL/TLS has gained popularity in the last two years and many administrators as well as security experts are often confronted with implementing a reasonable solution for mitigating that issue.
There are sufficient sources in the Internet on what the BEAST attack is and how it can be employed to eavesdrop connections and hijack user sessions, so I will not spend any time on that.
In this blog I will explain how you can configure your SAP NetWeaver AS ABAP (all versions) or AS Java (7.10 and newer) system to protect it against BEAST. For older AS Java releases I will write a separate blog on how to harden the cipher suite configuration and protect against BEAST.
Prerequisites:
Prerequisites for implementing the BEAST mitigation is that you have configured an appropriately running SSL/TLS configuration on your application server. Make sure also that you have installed and running the most current SAPCRYPTOLIB version on your system.
For ABAP systems you can check the version in transaction STRUST. Choose Environment -> Display SSF Version. You will get a pop-up like this one:

For current Java application servers starting with release 7.10 you can check the ICM trace to verify that you are running the most current SAPCRYPTOLIB on the system. The ICM trace can be viewed in SAP NetWeaver Administrator (/nwa) Log Viewer (/nwa/logs). In the Log Viewer choose View -> Open Expert View and select dev_icm from the Display Log File: drop down.

Alternatively you can find that information on file system level under: <drive>\usr\sap\<sid>\<instance>\work\dev_icm
You can download the most current version on the following site:
https://service.sap.com/security
BEAST Considerations
Fixing BEAST on the server side can be summarized in choosing the appropriate cipher suites allowed for establishing an SSL/TLS connection. The usual issue is that system owners have to balance security and usability of the service they offer. The application services should often be accessible by any browser type in different flavors and versions. This implies that the service operator should consider the use case of his application and the type of clients who consume his service. Enforcing only highly secure cipher suites on the server side may result in connectivity issues on the client side as clients may not support the highly secure ciphers allowed on the server. A reasonable balance between security and usability can be achieved by using prioritization of the ciphers used. This means, the server would try to establish an SSL/TLS connection with the client by using highly secure ciphers, which cannot be attacked by BEAST and only if the client does not support these ciphers, the server would fall back to more insecure or “BEAST attackable” ciphers. As the BEAST attack it targeting only CBC ciphers, a solution would be to prioritize RC4 ciphers higher as CBC.
BEAST Mitigation
SAPCRYPTOLIB offers all together 11 ciphers in different categories according to their strength – EXPORT, LOW, MEDIUM and HIGH. For the sake of eliminating ciphers which are insecure you should use only MEDIUM and HIGH ciphers. This leaves our set of choice to two MEDIUM RC4 ciphers and three HIGH CBC ciphers.
In order to protect against BEAST you should prioritize the RC4 ciphers to have higher priority than the CBC ciphers.
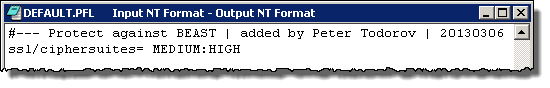
Cipher configuration is best performed in the default profile of the application server. The profile file is by default located at:
<drive>\usr\sap\<sid>\SYS\profile\DEFAULT.PFL
Open the file and locate the configuration parameter ssl/ciphersuites. If not available, you need to add it. Set the parameter as follows:
ssl/ciphersuites= MEDIUM:HIGH
Restart all ICM processes of your system and test your new configuration by using the different SSL/TLS scanners available in the Internet.
- SAP Managed Tags:
- Java
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
A Dynamic Memory Allocation Tool
1 -
ABAP
8 -
abap cds
1 -
ABAP CDS Views
14 -
ABAP class
1 -
ABAP Cloud
1 -
ABAP Development
4 -
ABAP in Eclipse
1 -
ABAP Keyword Documentation
2 -
ABAP OOABAP
2 -
ABAP Programming
1 -
abap technical
1 -
ABAP test cockpit
7 -
ABAP test cokpit
1 -
ADT
1 -
Advanced Event Mesh
1 -
AEM
1 -
AI
1 -
API and Integration
1 -
APIs
8 -
APIs ABAP
1 -
App Dev and Integration
1 -
Application Development
2 -
application job
1 -
archivelinks
1 -
Automation
4 -
BTP
1 -
CAP
1 -
CAPM
1 -
Career Development
3 -
CL_GUI_FRONTEND_SERVICES
1 -
CL_SALV_TABLE
1 -
Cloud Extensibility
8 -
Cloud Native
7 -
Cloud Platform Integration
1 -
CloudEvents
2 -
CMIS
1 -
Connection
1 -
container
1 -
Debugging
2 -
Developer extensibility
1 -
Developing at Scale
4 -
DMS
1 -
dynamic logpoints
1 -
Eclipse ADT ABAP Development Tools
1 -
EDA
1 -
Event Mesh
1 -
Expert
1 -
Field Symbols in ABAP
1 -
Fiori
1 -
Fiori App Extension
1 -
Forms & Templates
1 -
General
1 -
Getting Started
1 -
IBM watsonx
1 -
Integration & Connectivity
10 -
Introduction
1 -
JavaScripts used by Adobe Forms
1 -
joule
1 -
NodeJS
1 -
ODATA
3 -
OOABAP
3 -
Outbound queue
1 -
Product Updates
1 -
Programming Models
13 -
Restful webservices Using POST MAN
1 -
RFC
1 -
RFFOEDI1
1 -
SAP BAS
1 -
SAP BTP
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP CodeTalk
1 -
SAP Odata
1 -
SAP UI5
1 -
SAP UI5 Custom Library
1 -
SAPEnhancements
1 -
SapMachine
1 -
security
3 -
text editor
1 -
Tools
17 -
User Experience
5
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |