
- SAP Community
- Products and Technology
- Product Lifecycle Management
- PLM Blogs by SAP
- SAP in the CESSA project last year: a summary
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We successfully concluded our collaboration in French ANR CESSA project. We contributed to advance the state of the art in the separation of concerns for security in web services. This blog post summarizes the academic results we obtained in the last year of the project.
The CESSA PROJECT at SAP
Our role in the project was to investigate on how one can automate security in service oriented architectures, in particular, web services, using aspect oriented techniques. We provided proof of concepts which demonstrate that security can be better understood and administrated, as a separate concern from the core functionalities of SOA.
In the next sections, we present a summary of the main research work we have published in the last year of the project. For additional information, please refer to the CESSA project website.
Best paper award at Securware 2012 - Towards Assisted Remediation of Security Vulnerabilities
We have received the best paper award at the SECURWARE 2012 conference (The Sixth International Conference on Emerging Security Information, Systems and Technologies). The paper [1] describes our tool for vulnerability scanning and remediation with aspects. As screenshot is shown below, where the interface is gathering context information to perform remediation:
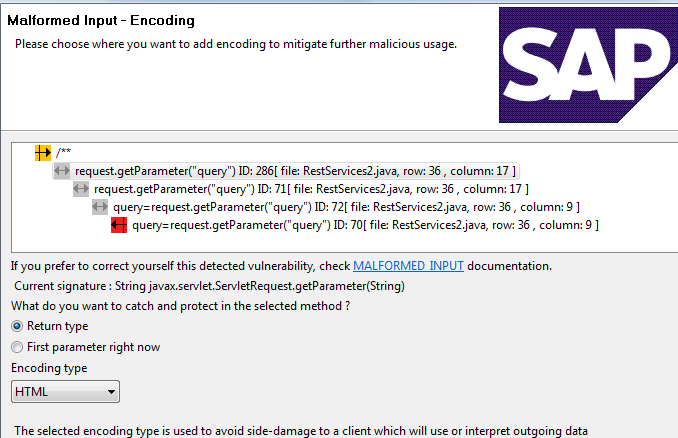
Security vulnerabilities are still prevalent in systems despite the existence of their countermeasures for several decades. In order to detect the security vulnerabilities missed by developers, complex solutions are undertaken like static analysis, often after the development phase and with a loss of context. Although vulnerabilities are found, there is also an absence of systematic protection against them.
In this work we introduce an integrated Eclipse plug-in to assist developers in the detection and mitigation of security vulnerabilities using Aspect-Oriented Programming early in the development life-cycle. The work is a combination of static analysis and protection code generation during the development phase. We leverage the developer interaction with the integrated tool to obtain more knowledge about the system, and to report back a better overview of the different security aspects already applied, and then we discuss challenges for such code correction approach. The results are an in-depth solution to assist developers to provide software with higher security standards.
For more information, see gabriel.serme/blog/2011/10/14/security-vulnerabilities-detection-and-protection-using-eclipse. The full reference for this work and full version can are available online [1].
Enabling Message Security for RESTful services
As we presented in a previous blog post, we presented at the 19th International Conference on Web Services (ICWS 2012) our proposal for securing RESTful services [2]. Currently, the security of RESTful services relies on ad-hoc security mechanisms (whose implementation is error-prone) or on the transport layer security (offering poor flexibility). We introduce the REST security protocol to provide secure service communication, together with its performance analysis when compared to equivalent WS-Security configuration. The paper brings several benchmarks for the protocol, such as the average processing time for messages when compared to SOAP when different operations are performed on the data, as depicted below:

The full paper can be found in the IEEE digital library [2].
Privacy Enforcement in the Cloud
We participated to the last Data Privacy Management Workshop, where we presented an advanced approach to privacy enforcement in cloud platforms [3]. We demonstrated the feasibility of our approach using the SAP NetWeaver Cloud platform, as explained in this blog post, by Jakub Sendor. The methodology is depicted in the figure below:

The solution we presented leverages Aspect-Oriented Programming paradigm, the fundamental technique we investigated in CESSA, thus increasing the code readability and maintainability. Furthermore, it simplifies developers work by providing the enforcement mechanism directly as a cloud platform component, decreasing the efforts concerning preparation of custom implementation. The full paper [3] can be found at the LNCS website.
We believe this can be a nice complement to initiatives such as the OASIS Privacy Management Reference Model (PMRM), in order to manage private data on the cloud.
Policy Language Definition for Distributed Systems
Expressing security policies to govern distributed systems is a complex and error-prone task. Policies are hard to understand, often expressed with unfriendly syntax, making it difficult to security administrators and to business analysts to create intelligible specifications. We introduce the Hierarchical Policy Language for Distributed Systems (HiPoLDS) [4]. HiPoLDS has been designed to enable the specification of security policies in distributed systems in a concise, readable, and extensible way.
HiPoLDS's design focuses on decentralized execution environments under the control of multiple stakeholders.Policy enforcement employs distributed reference monitors who control the flow of information between services. As illustrated in the figure below, where multiple distributed reference monitors are responsible for the protection at the borders of each domain.
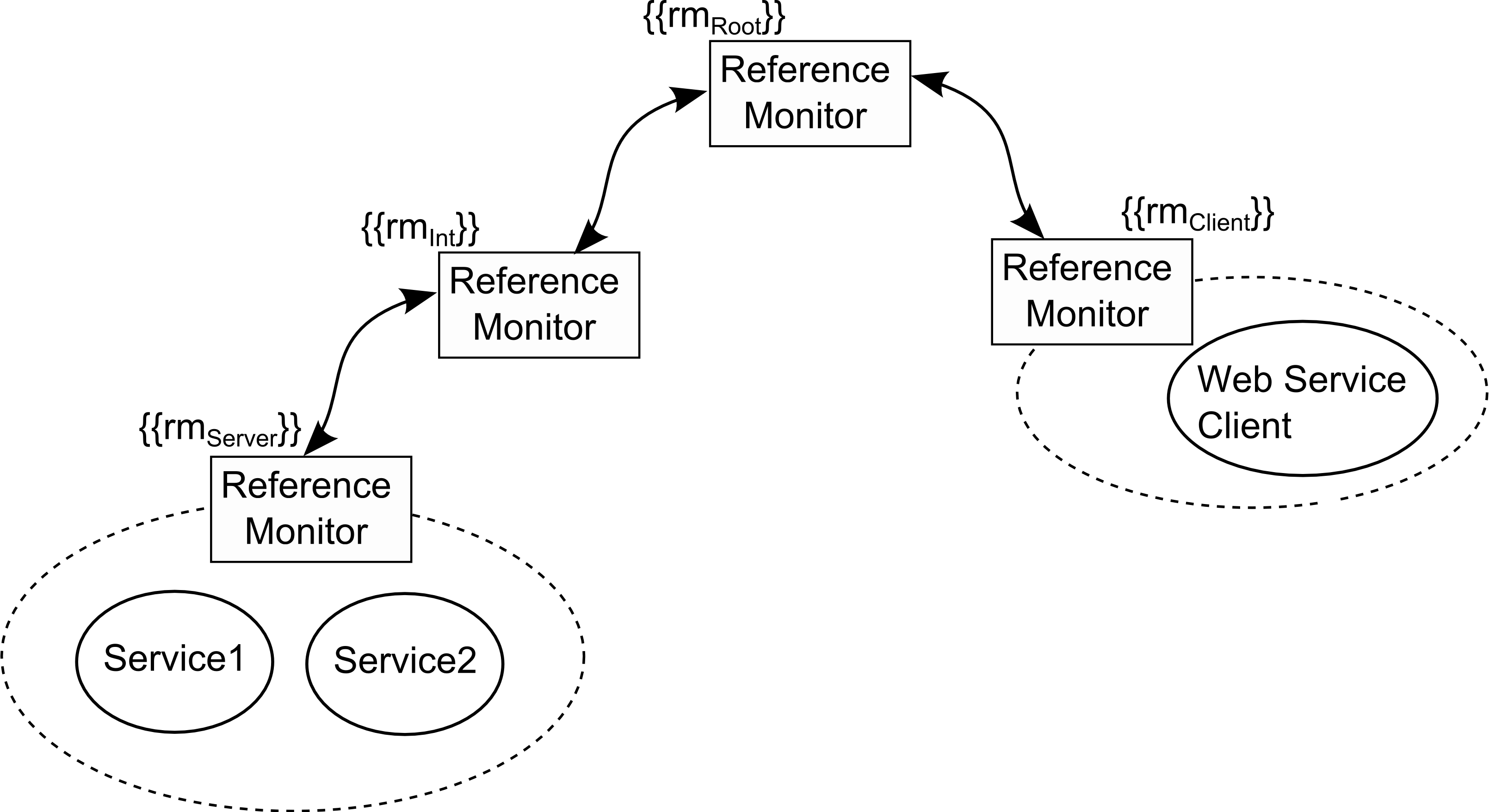
HiPoLDS allows the definition of both abstract and concrete policies, expressing respectively high-level properties required and concrete implementation details to be ultimately introduced into the service implementation. The electronic version of the paper [4] is available at LNCS [4] and an extended journal version [5] was published at the Information Security Technical Report.
Conclusions
CESSA was a very successful project from the SAP perspective, where we have contributed with a set of aspects and aspect interfaces for cross-boundary and crosscutting security properties on SOA [2, 4, and 5]. We implemented of common patterns for the provision of security functions [1, 2], remediating vulnerabilities in the code, or providing security for web services. We have also used aspects and interfaces to extend existing security functionality, in particular advanced role-base security models that are not supported in standard Web Service based SOAs, for instance, dealing with privacy concerns [3], which are becoming crucial with the emergence of the cloud, among other works.
We aim now at a longstanding transfer of technology within SAP, were the knowledge we have developed and the techniques we experimented with, will assist our business units in securing our solutions. We would like to thank all partners EMN, EURECOM, and IS2T for the great work and the ANR for the support (Grant 09-SEGI-002-01).
References
1. G. Serme, M. Guarnieri, P. El Khoury, and A. Santana De Oliveira. Towards assisted remediation of security vulnerabilities. Proceedings of the Sixth International Conference on Emerging Security Information, Systems and Technologies. SECURWARE 2012.
2. G. Serme, A. Santana de Oliveira, J. Massiera, and Y. Roudier. Enabling message security for restful services, Proceedings of the 19th International Conference on Web Services. ICWS 2012.
3. P. Yu, J. Sendor, G. Serme, and A. Santana de Oliveira. Automating privacy enforcement in cloud platforms. Proceedings of the 7th International Workshop on Data Privacy Management. DPM 2012, in conjunction with the 17th annual European research event in Computer Security symposium (ESORICS 2012), Springer.
4. M. Dell'Amico, G. Serme, M. S. Idrees, A. Santana de Oliveira, and Y. Roudier. Hipolds: A security policy language for distributed systems. Proceedings of the 6th Workshop in Information Security Theory and Practice. WISTP 2012.
5. M. Dell'Amico, G. Serme, M. S. Idrees, A. Santana de Olivera, and Y. Roudier. Hipolds: A security policy language for distributed systems. Information Security Technical Report , ISSN 1363-4127.
All project publications can be seem at the CESSA project publications page.
The CESSA TEAM at SAP (Present and former members)
- Julien Massiera
- jean-christophe.pazzaglia
- anderson.santanadeoliveira
- theodoor.scholte
- jakub.sendor
- gabriel.serme
We also thank all the internship students who worked with us at SAP: Peng Yu, Marco Guarnieri, and Yann Lehmann.
- SAP Managed Tags:
- SAP Innovation Management,
- Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Implementation Insights from Experts for SAP Enterprise Product Development in Product Lifecycle Management Blogs by SAP
- Extending SAP Digital Manufacturing with Azure, Part II: Applying the reference architecture to a visual inspection scenario in Product Lifecycle Management Blogs by Members
- Chemical inventories in EHS Health and Safety Management in Product Lifecycle Management Blogs by SAP
- Create your own custom Quick Financial Application in Product Lifecycle Management Blogs by SAP
- Analyzing the Project Management Workstream in an S/4 HANA Implementation Project in Product Lifecycle Management Blogs by Members