
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Securing Business Objects Content – Folder Level, ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Securing Business Objects Content – Folder Level, Top Level and Application Security
Applies to:
Business Objects Enterprise XI 3.0 / 3.1, for more information, SAP Business objects Solutions Homepage.
(http://www.sdn.sap.com/irj/sdn/sbo-solutions)
Summary
Unlike SAP systems, Business Object Enterprise XI 3.0/3.1 do not comprise of Roles, Profiles and
Authorization objects. Security in Business Objects is different than SAP and it consists of: Folder level
security, Application Security, Object Level Security and inheritance concepts. This document begins with
simple example on how to create users, user groups and ends with creating access Levels and basic
troubleshooting techniques using the Security Query.
Author(s): Shikha Baxi Dhiraj Wamanacharya & Milind Desai
Company: IBM India Pvt. Ltd
Created on: 18th May 2011
Author Bio
Shikha Baxi,Dhiraj Wamanacharya & Milind Desai are working with IBM and have more than 3.5 yrs of experience in SAP
Administration, Security, and have been extensively working in Business Objects in the area of
implementation and upgrade.
User and User Group Creation:
Users in Business Objects are of various types, and a user can login to Business Objects (CMC or InfoView)
using that particular authentication with which it has been created. The authentications are:
- 1. Enterprise
- 2. LDAP
- 3. Windows AD
- 4. SAP
The document covers Enterprise and SAP user administration from the above list.
Creating an Enterprise User:
The example below illustrates “How to create an Enterprise user” in Business Objects.
Login to CMC _ Go to Users and Groups
To create a new User click on  and for User group creation click on
and for User group creation click on 
OR
Click Manage:

Select the Authentication Type in the next screen and maintain the required fields.
1 ) Authentication Type as Enterprise :

2) Authentication Type as SAP :

When Authentication type is SAP (secSAPR3) then you only need to maintain Account Name as
<SAP SID>~<Client No.>/<SAP User ID> .
User will login in Business Object Using his SAP Login credentials.
Connection Type:
Concurrent - This user belongs to a license agreement that states the number of users allowed to be
connected at one time.
Named : This user belongs to a license agreement that associates a specific user with a license. Named
user licenses are useful for people who require access to Business Objects Enterprise regardless of the
number of other people who are currently connected.
Click Create & Close
“Administrator” is the default user that comes along with the Business Objects installation.
User Group Creation:
The user group is a collection of users who require same kind of authorization. So instead of assigning
authorization to every new user that is created, we can create a user group and assign the requisite
authorization to it, and later simply assign the user to that particular user Group.
Click Create User group:
Name the User Group:

To add a user to the group click (Add member to user group) 
You can add a newly created or existing group to some other group while you can also assign a user to a
- group.
Administrators and Everyone are the default groups that come along with the Business Objects installation.
Importing Roles from the backend SAP system:
Let us continue with ‘How to import roles’, which in turn import users from a backend SAP system to the
Business Objects System’.
Login to the CMC, Click Authentication _ SAP
Click the Options tab, now you need to check the field Automatic import User and click Update

Since your Business Objects System is connected to a Backend SAP System you are able to see a list of
Roles in the left Pane which belong to the SAP system. You can now Import the roles from the Backend SAP
system to the Business Objects system, select the role in the left pane and click  to import the
to import the
roles then click Update :

When a role is imported all the users assigned to that role in your backend SAP system, will also get
imported into the Business Objects system.

Here, PBW is our SAP system Id, while 100 is the client number from where the users arrive, hence the
naming convention: PBW~100 /
Whenever a user assignment is done to a role in backend (already imported in Business Objects) and user
should get created in Business Objects automatically, then you should also check Force Synchronization
under Options tab and click Update:

Now when a user get assigned to a role in backend , only you need to click Update button under Role
Import tab and the user will get created in the Business Objects system. To automate this activity also, we
have elaborated the step in the next section.

Schedule a SAP Authentication Role / Group update in Business Objects XI 3.1 using a java program
object:
To schedule (automate) the updating of SAP Users in the Business Objects system, you need to follow the
steps mentioned below:
1 .Download SAP Update. jar file from SAP Note : 1406037
2. Unzip the file
3. Login in Business Objects CMC ->Folders-->Manage_New _ folder called Objects ,

4. Select the folder "Objects" and click on Manage | Add | Program File

5. Choose as Program Type as Java and add SAPUpdate.jar
6. Right Click on SAPUpdate within your Objects folder and choose Properties | Default Settings | Program
Parameters
Specify as "Class to run:" sapupdate.Main
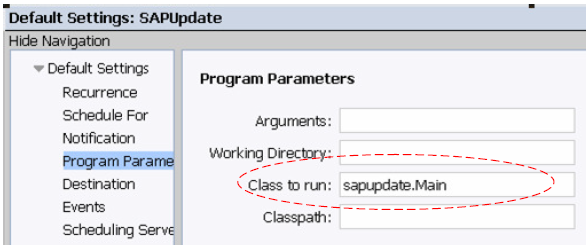
Using the "Run Now" and schedule the Program Object
Set the Recurrence for this Program as desired.

Under Authentication tab -> Options, you need to check the field Automatic import User and Force User
Synchronization
Go to Authentication Tab -> Select Role and Import, click update.

Now, the SAP user will get imported every time when it is created and assigned the role in the SAP system
which is already imported in Business Objects CMC. As such, there is no need to create a user in the
Business Object CMC every time a new user is created in the SAP system. .
Note: The statement assumes that every user which is created in the SAP system needs to be created in
Business Objects system. Else,if all the users are not required in the Business Objects system , the role
which is imported in the Business Objects system should not be assigned to such users in the SAP backend.
Access Levels in Business Objects:
Pre-Defined access levels:
There are four default access levels that come along with the Business Objects Installation for securing the content. These levels are explained as below:
1. Full Control: A principal has full administrative control of the object.
2. Schedule: A principal can generate instances by scheduling an Schedule object to run against a
specified data source once or on a recurring basis.
3. View: If set on the folder level, a principal can view the folder, View objects within the folder, and
each object's generated instances.
4. View on Demand: A principal can refresh data on demand against a data source.
5. No Access: The user or group is not able to access the object or folder.

To see what rights are included in an access level; go to CMC -> select Access Level, right click -> Include
rights

Custom Access Levels:
In addition to the predefined access levels, you can also create and customize your own access level, which
can greatly reduce administrative and maintenance costs associated with security.
How to create access levels: Login to CMC _ Select Access Levels.

Maintain Title and Description:

To include rights in an access level, select the Access level, right click -> included rights

Click Add/Remove Rights:
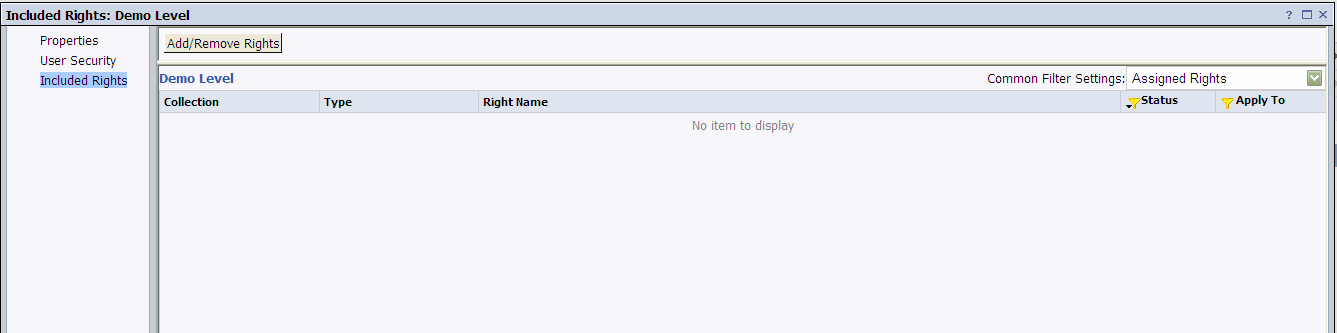
You will be able to see four types of rights collections in the left panel namely:
- General
- Content
- Application
- System
By default you will be guided to the “General Global rights” window. Now set your general global rights:
Each right can have a status of:
- Granted
- Denied
- Not Specified.
You can also choose whether to apply these rights to the object only or to their sub-objects only, or both.
To set type-specific rights for the access level, in the navigation list, click the Rights collection, and then
click the Subcollection that applies to the object type you want to set the rights for.

Folder level Security:
Folder-level security enables you to set access-level rights for a folder and the objects contained within that
- folder. While folders inherit security from the top-level folder (root folder), subfolders inherit the security of
their parent folder. Rights set explicitly at the folder level override inherited rights.
To set folder level security:
1. Login to CMC _ Select Folders
2. Right click on the particular folder & select User Security.

Select the Principal (user / group) you wish to add:
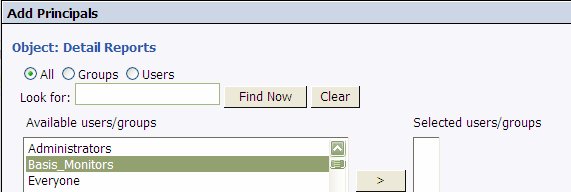
On the same screen in the bottom right corner click:
Provide the requisite Access Level to this Principal. Here we have provided “Full Control” to the
“Basis_Monitors” group.

Click Apply, and then Click OK.
To View, what access has been provided to the Principal click “View Security”
Assigned Rights:
Top Level Security:
The below example shows, how Top Level Security can be assigned to a principal against the Business
Objects Servers:
Manage the Top Level Security for Severs:
For this:
1. Login to CMC -> Servers-> Manage
2. Select Top Level Security _ All Servers/ All Server Groups.
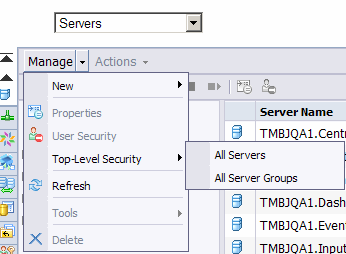
Click OK.

Break Inheritance:
If your Principal is a part of multiple groups and to avoid “Conflict of Rights” you can uncheck the:
- 1. Inherit From Parent Folder
- 2. Inherit From Parent Group.
Now, provide access/advanced level security as required.

Application Level Security:
Users need access to particular Business Objects applications to perform their jobs effectively. As a
Business Objects Administrator you are responsible for setting appropriate application security levels
according to the needs of your organization.
Application security is used to control the functionality that users and groups have to the Business Objects
Enterprise applications. The Manage area of the CMC allows you to control access for the following
Business Objects Enterprise applications:

Manage CMC User Security:
To Manage CMC security:
Logon to CMC -> Click Applications _ Select CMC
Now Right Click and select User Security.

Click Add Principals:
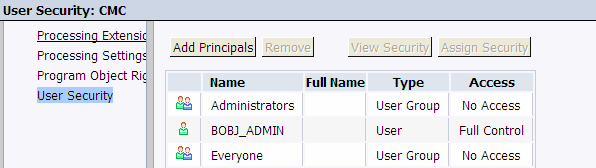
Select the principal for which you want to assign security.

On the same screen in the bottom right corner click:
Now assign the security as required:

Now Click “View Security” on the Next screen to check what access has been provided to “test” user:

Similarly you can manage Security, and access for rest of the applications.
Advance Rights :
You may sometimes need to override certain granular rights in an access level. Advanced rights let you
customize the rights for a principal on top of the access levels, the principal already has.
There are 3 Type of rights exist as explained earlier:
- Grant
- Denied
- Not Specified
Exception:
• In general, the rights that are set on child objects override the rights that are set on parent
- Object.
• In general, the rights that are set on subgroups or members of groups override the rights that are set on
- groups.
If a user belongs to more than one group, and there is a conflict in rights assignments between the groups to
which the user belongs to, the Denied (D) right wins over a Granted (G) right, and the Granted (G) right wins
over a Not Specified
Case Study I: (Advanced Rights)
We will be explaining, how advanced rights are used through this Case Study:
Consider an example where your user needs to have following access:
i) Needs to be provided no access to any folder or report , ii) Need to have access to schedule a report
(Material Plant) , iii) Need to view, pause and resume its scheduled instances iv)Need to be restricted to
delete a instance and view a report.
We proceed as below:
- 1. Maintain No Access at root level security at Folders:

2. Select the Material plant report and click User Security

Break inheritance and click Advance tab ->Add/Remove Rights

Once done, you are able to view the General global rights, Now maintain the rights by clicking on radio
buttons for grant denied or not specified
- Select the Grant radio button for providing access to schedule a report, view, pause and resume its
scheduled instances.
- Select Deny radio button to deny access to any folder or report, and to view, delete a report.
Rights are divided into the following collections based on the object types they apply to:

- You can also allow the rights to be applied to a Sub object, by checking the Object and Sub Object
check boxes, next to the Rights column.
- Only after you click grant or deny radio button, object and sub-object check boxes are enabled. Now
you can maintain the scope of rights.
- If you want to apply a right only for a folder and not for its sub folders, then uncheck sub-object check
- box.
Security Query:
Due to the complexities inherent in a security system as complicated as Business Objects Enterprise XI 3.1,
systems administrators sometimes find it difficult to pinpoint from where a particular user right is inherited.
Security queries let you determine which objects a principal has certain rights to and enables you to manage
user rights:
In the earlier part of our Case studies we have created a group called “Basis_Monitors”. In this exercise we
will find out what access Basis_Monitors have on Servers using the “Security Query”. For this:
Logon to CMC -> Select Query Results
Now select Security Queries -> Right click _ Create Security Query.
Provide the required inputs like :
i) Principal (Basis_Monitors).
ii) Check /Uncheck Query Permission as per the requirement.
iii) Select the Query Context (Servers)
After selecting the required parameters click OK.
Now, the next screen appears showing the result regarding what access the principal has on the Querycontext.
You can also click on the Source column to view, from where the Principal is obtaining its access:
In case you see, the source along with (Inherited) it implies that access comes either from the Parent group
or from the parent folder.
Related Content:
- 1. http://help.sap.com/businessobjects/
- 2. http://www.sdn.sap.com/irj/sdn/sbo-solutions
- 3. http://www.sap.com/services/education/catalog/businessobjectstraining/businessintelligence
For more information, visit https://www.sdn.sap.com/irj/sdn/nw-bi
Copyright
© Copyright 2010 SAP AG. All rights reserved.
No part of this publication may be reproduced or transmitted in any form or for any purpose without the express permission of SAP AG.
The information contained herein may be changed without prior notice.
Some software products marketed by SAP AG and its distributors contain proprietary software components of other software vendors.
Microsoft, Windows, Excel, Outlook, and PowerPoint are registered trademarks of Microsoft Corporation.
IBM, DB2, DB2 Universal Database, System i, System i5, System p, System p5, System x, System z, System z10, System z9, z10, z9,
iSeries, pSeries, xSeries, zSeries, eServer, z/VM, z/OS, i5/OS, S/390, OS/390, OS/400, AS/400, S/390 Parallel Enterprise Server,
PowerVM, Power Architecture, POWER6+, POWER6, POWER5+, POWER5, POWER, OpenPower, PowerPC, BatchPipes,
BladeCenter, System Storage, GPFS, HACMP, RETAIN, DB2 Connect, RACF, Redbooks, OS/2, Parallel Sysplex, MVS/ESA, AIX,
Intelligent Miner, WebSphere, Netfinity, Tivoli and Informix are trademarks or registered trademarks of IBM Corporation.
Linux is the registered trademark of Linus Torvalds in the U.S. and other countries.
Adobe, the Adobe logo, Acrobat, PostScript, and Reader are either trademarks or registered trademarks of Adobe Systems
Incorporated in the United States and/or other countries.
Oracle is a registered trademark of Oracle Corporation.
UNIX, X/Open, OSF/1, and Motif are registered trademarks of the Open Group.
Citrix, ICA, Program Neighborhood, MetaFrame, WinFrame, VideoFrame, and MultiWin are trademarks or registered trademarks of
Citrix Systems, Inc.
HTML, XML, XHTML and W3C are trademarks or registered trademarks of W3C®, World Wide WebConsortium, Massachusetts
Institute of Technology.
Java is a registered trademark of Sun Microsystems, Inc.
JavaScript is a registered trademark of Sun Microsystems, Inc., used under license for technology invented and implemented by
- Netscape.
SAP, R/3, SAP NetWeaver, Duet, PartnerEdge, ByDesign, SAP Business ByDesign, and other SAP products and services mentioned
herein as well as their respective logos are trademarks or registered trademarks of SAP AG in Germany and other countries.
Business Objects and the Business Objects logo, BusinessObjects, Crystal Reports, Crystal Decisions, Web Intelligence, Xcelsius, and
other Business Objects products and services mentioned herein as well as their respective logos are trademarks or registered
trademarks of Business Objects S.A. in the United States and in other countries. Business Objects is an SAP company.
All other product and service names mentioned are the trademarks of their respective companies. Data contained in this document
serves informational purposes only. National product specifications may vary.
These materials are subject to change without notice. These materials are provided by SAP AG and its affiliated companies ("SAP
Group") for informational purposes only, without representation or warranty of any kind, and SAP Group shall not be liable for errors or
omissions with respect to the materials. The only warranties for SAP Group products and services are those that are set forth in the
express warranty statements accompanying such products and services, if any. Nothing herein should be construed as constituting an
additional warranty.
- SAP Managed Tags:
- SAP BusinessObjects Business Intelligence platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
12 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
CA
1 -
calculation view
1 -
CAP
4 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
General Splitter
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
GraphQL
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Prettier
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
2 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
2 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
14 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- 5 Easy apps that can be created right away using Joule AI Assistant in Technology Blogs by SAP
- Dealy in updating custom values for Visibility Scenario SAP BUILD AUTOMATION in Technology Q&A
- Supporting Multiple API Gateways with SAP API Management – using Azure API Management as example in Technology Blogs by SAP
- SAP Cloud ALM and Identity Authentication Service (IAS) in Technology Blogs by SAP
- Configuring SAP CI/CD pipeline for Deploying ReactJS application in Cloud Foundry in Technology Q&A
| User | Count |
|---|---|
| 8 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |