
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Virtual Analysis Authorization implementation (BW ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Virtual Analysis Authorization implementation within BW 7.30+ and a zero management approach
Summary
Most flexible Analysis Authorization: The combination of a self-service maintenance of characteristic values and associated key figures to users with an automated and by runtime created "Virtual Analytics Security Object (ASO)" for the Query user allows either to reduce implementation time for authorization projects or especially reduces intensively the creation and maintenance time of user profile assignemts for new and changing security demands. The two aspects include the following:
- An online user interface (UI) for departments key users to maintain their users authorizations rights on characteristic values, key figures and hierarchies;
- an implementation of the BAdI for Virtual Analysis Authorization.
Both aspects will be covered within this BLOG.
Many thanks and appreciation to my current/last customer project - in person the SD/BI Developer Matthias Hommer - who felt confident either with the concept or the development/implementation to this new approach.
Architecture and implementation
Following picture represents the data model which will be explained with possible alternatives:

On the left hand side of the picture the basis to store user authorization values is displayed. On the right hand side you can see the aspects for virtual analysis authorization on query execution runtime.
Self-service maintenance for analysis authorization values, hierarchy values and key figures
Idea:
Following the principles of "data ownership" (by departement), "self-service BI administration szenarios" and "zero administration" the idea is to let a few key users of each department maintain the authorization values for each of their query users directly into the system. In detail they have to maintain following:
- characteristic values assigned to the departemental or organizational view to their users. They have to maintain eg. distribution channel down to customer number values to each user;
- key figures which are allowed to be reported by each user;
- hierarchies and hierarchie nodes which are allowed to be reported by each user.
Possible UI alternatives:
From our perspective there are multiple ways how you can enter and store this data:
- XLS or CSV file as UI which is maintained by the department and uploaded into any table or BI object (characteristic, DSO);
- (Web-)Dynpro as UI to store the data in any DDIC table(s);
- InfoObjects with the BW backend transaction to add/edit master data;
- Transactional InfoCube with planning query - use a key figure value for authorization rights on characteristic value combination: 0 = no right, 1 = data access allowed;
- not a question of UI but "loading" authority values:
- standard technical content DSO's for authorization object generation;
- assignment to ERP authorization eg to accounting fields;
To us all of the mentioned possibilities were not appropriate or had some minor / major disadvantages so we decided to use a different approach. Here some arguments we had: by using XLS or CSV you have a break within the media; Dynpro programming seemed to be too complex to us for a hand ful of fields; with InfoObject master data maintenance we did not want to shift authorization to the backend as an other area even for the key users; the concept to use a transactional InfoProvider needs to create (via exit) all possible characteristic value combinations to let the necessary key figure become by default 0 (= not authorized) or via planning query to modify the value combination to 1 (= authorized) by the key user ... also complex.
Implementation:
We have decided to use following - see "I" within the picture above:
- We wanted to use BW objects like InfoObjects or DSO's because of being able to use the already loaded InfoObject master data values. Also we wanted to be able to combine the objects by a MultiProvider in order to read user authorization values during runtime with a standard interface (please see later).
- missing asterics masks master data values like "abc*" or "1*" could we enhance manually within the InfoObject master data maintenance (text description eg: "for analysis authorization")
- We wanted to allow the maintenance of excluding values which is not possible for ASO's and standard analysis authorizaton - excluded values like "all customers beside 4711 and 4712" can be transformed during runtime into including values.
- We created DSO's which represent hierarchies, key figures and the department view to each reporting areas by the authorization relevant InfoObjects.
- The maintenance will be done by generated DDIC-maintenance-views on the active table of the DSO; to each maintenance view we can address a transaction code for authorization easily.
- we followed the template DSO's which are delivered by the technical content for analysis authorizations (0TCT*);
- all DSO's have some fields in common which will be filled automatically by maintenance view exit: BW Sys-ID, last changing user, last changing date;
- all DSO's have some fields in common which need to be maintained manually: User, InfoProvider, validity date and activity;
- The DSO structures for hierarchy includes the fields corresponding the technical content eg. InfoObject (to the hierarchy), hierarchy name, hierarchy version, hierarchy node, etc.;
- The DSO structures for key figures include the fields corresponding the technical content eg. key figure name;
- The DSO structures for reporting areas eg. 'Sales' includes the (authorization relevant flagged) InfoObjects as fields like distribution channel, customer and/or material class.
Virtual Analysis Authorization in combination with exit variables and authorized F4-Values in a class library
Idea:
Comparing
- to the "old" (and still common) idea - transaction RSECADMIN - of generation in fore front of Analysis Authorization Objects to all possible value combinations in addition to key figures and hierarchies and an assignment to user (roles) accordingly
- with the new concept of Virtual Analysis Authorization by (Query-)user the ASO is created and checked during runtime
--> only the authorization values for one single user at one processing time of a Query execution will be processed.
Possible alternatives:
Due to the fact of having a kind of "performance pressure" the alternatives tend to reduce processing time of creating and checking the ASO to each Query execution of a user. Possible is to read the authorization values faster by indexing the DSO's into the BWA (possible with BWA7.20). Also to consider is having instanced the reading of the authority values by the BAdI enhancement implementation already.
In our implementation and system environment we have not many (concurrent) users. So it would be very interesting how virtual ASO's will perform with hundred's or even thousands of Query execution users.
Implementation:
Our implementation is based on a customer class library - please see representing "A" within the picture. Here we combine as well as transformation coding encapsulation like start-, end- or field-routines or Query variable exit coding or other pieces of helping coding within the overall BW environment.
- One helping function is a class method to read all authorization values for one single user - please see the representing number "2" within the picture. With the standard function module RSDRI_INFOPROV_READ_RFC we are able to read via the MultiProvider all necessary authorization values to one user and to the exact list of requested query characteristics (which is provided during runtime by the BAdI interface). Also the coding checks the maintained authorization values for correctness:
- are the characteristics authorization relevant (with function module RSEC_GET_AUTHREL_INFOOBJECTS);
- include the key figure field names which are authorization relevant;
- include hierarchy authorization values (InfoObject of hierarchy, node, node InfoObject, level, etc.);
- turn maintained exclude filters into include filters;
- check asterics masks signs like "*" and change into "contains pattern" accordingly.
- When prompting for a variable we want to restrict to those F4 values for which the user is allowed. So when having a Query variable (see number "1" within the picture) we process the variable exit within the correct i_step within a class-method (see number "3" within the picture) which calls the class method just mentioned before (numer "2" within the picture).
- And before all of that will be called the exit for the new BAdI enhancement implementation method - see number "4" within the picture above).
- For that you can refer to the help-side however this is very spartanic.
- The reference within the system does help more by far - I have copied it into the Appendix so you can read through it.
- Also an example method helps to understand and even you can test it easily by un-commenting the delivered class-method ABAP code.
- The over-ruled method GET_AUTHS needs to be delivered in it's interface tables C_T_HIE and C_T_VAL; in our implementation the interface to the helping method to read the authorization values by user - see number "2" delivers the values within this type of format already.
- When you have understood the manual maintenance of security analysis objects within transaction RSECADMIN then it is easy to understand how to fill the interface tables and how the BAdI method is working.
- Here you can see our implementation:
- Transaction SE18:

- Enhancement implementation:

- Enhancement implementation element:

- Overruled class method "GET_AUTHS" implementation:
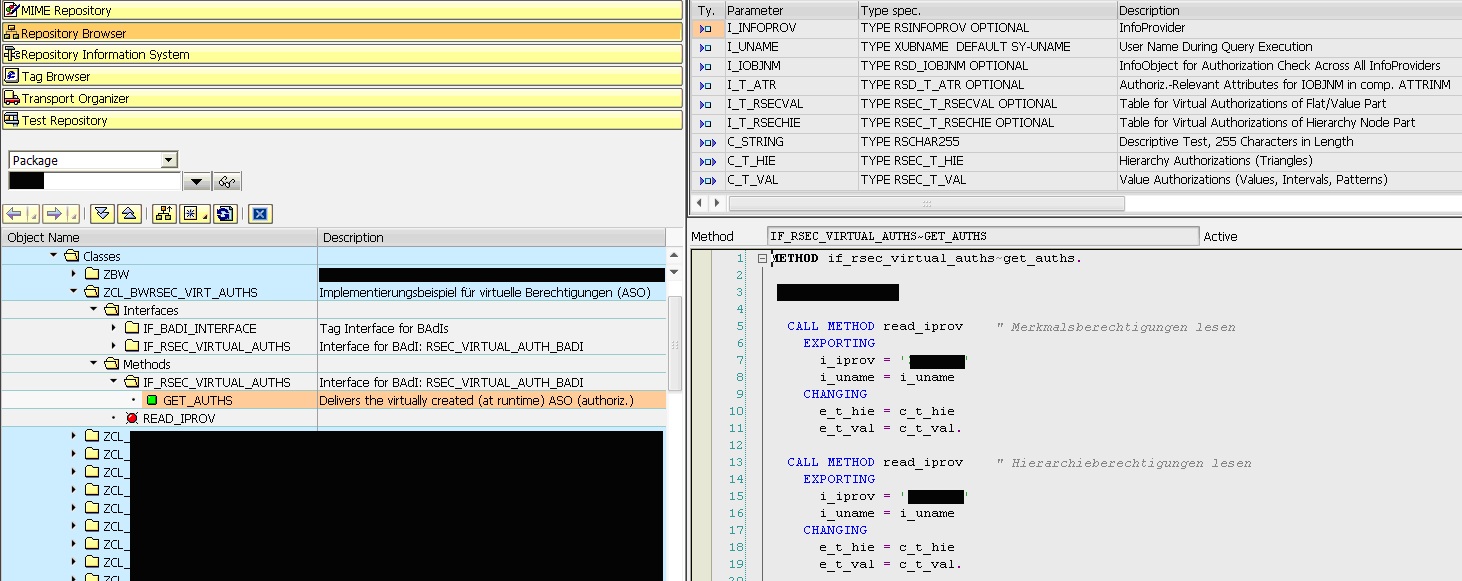
- Transaction SE18:
Final thoughts
From my personal point of view this new BAdI interface is exciting - it is just great when thinking of all these authorization projects out there and also how much work it is to maintain permanent shifting authorization rights for Query users out there. The combined approach seems to me a tremendous work load rejection of any BI- or system-administration-security team. Please feel free to comment or enhance this idea and/or implementation or give suggestions to similar ideas!
Appendix
RSEC_VIRTUAL_AUTHS
Description
This BAdI interface enables users to generate virtual analytics security objects (ASOs). These ASOs are generated at runtime and are checked as analysis authorizations.
It is therefore only possible to determine which authorizations the user has, at runtime. You can also enhance existing authorizations. Furthermore, you can use variables in virtual authorizations; these variables are then processed as normal customer exit variables as usual at runtime. For reasons of clarity, however, we do not recommend this since the required runtime operations could be executed during the implementation for the virtual ASOs.
Virtual authorizations (analytics security objects) can often actually replace variable processing in authorizations and can therefore make the process flow clearer.
Use
Method GET_AUTHS requests for the content as value authorizations and hierarchy authorizations in parameters C_T_HIE and C_T_VAL. These tables contain the ASO or authorization names and the relevant InfoObjects along with an authorization definition in the form of intervals (C_T_VAL) or hierarchy nodes with the authorization definition (C_T_HIE). One row is expected for each interval and each hierarchy node. The various authorization combinations are grouped together as rows for each authorization (TCTAUTH field). (See example.)
The method can be called in two ways; with or without InfoProviders:
If the InfoProvider is specified in parameter I_INFOPROV, only the authorizations for this InfoProvider are required. If the InfoProvider is not specified, InfoObject I_IOBJNM should generally be used if the module is called in the standard environment for a query. Both parameters can only be initial in the case of documents that are protected with authorizations. InfoProvider-independent, that is, cross-InfoProvider authorizations are then required. Since authorization-relevant attributes are generally specified for a particular InfoObject, these attributes are automatically entered in the input parameter I_T_ATR for the sake of simplicity and to accelerate processing. They can then, for example, be authorized explicitly (I CP * in C_T_VAL), or not authorized, if required.
The user name is also provided when a transaction is started with the function Execute as Other User (RSUDO); the user name does not have to match the value for sy-uname. This means the analysis authorization check is made with a user that differs from sy-uname. You should therefore always use parameter i_uname instead of sy-uname.
Example
Two virtual ASOs, 'ONE' and 'TWO', are to be created. In the first ASO, the interval [A, D] is to be authorized for characteristic 0EMPLOYEE, which is authorized for a specific cost center node. In addition, the combination [D, G] is to be authorized for another cost center.
This is to be done as follows:
Field in C_T_VAL:
TCTAUTH ONE TWO
TCTIOBJNM 0EMPLOYEE 0EMPLOYEE
TCTSIGN I I
TCTOPTION BT BT
TCTLOW A D
TCTHIGH D G
Field in C_T_HIE:
TCTAUTH ONE TWO (Name of authorization or ASO)
TCTIOBJNM 0COSTCENTER 0COSTCENTER
HIESID 123 123 (Field can be left empty)
HIEID AXYDGFHE... AXYDGFHE... (Field can be left empty)
TCTHIENM MYHIERARCHY MYHIERARCHY
TCTHIEVERS
TCTHIEDATE 99991231 99991231
TCTNIOBJNM 0HIER_NODE - (Empty means end node or leaf)
TCTNODE 100_all 100123
TCTATYPE 2 1 (Authtype; Authtype = 0 never permitted for leaves (only nodes))
TCTACOMPM 0 0
TCTTLEVEL 2 0
TCTHDATE 00000000 00000000
Notes
To find out what is used for interval and hierarchy authorization definitions, see database tables RSECVAL and RSECHIE.
Function module RSEC_GET_AUTHREL_INFOOBJECTS can be used to identify which InfoObjects are relevant (see the documentation for the module).
RSEC_VIRTUAL_EXEC_AUTH_BADI
Use
You can use this enhancement to check the execution authorization by implementing your own method instead of using authorization object S_RS_COMP (method get_execution_auth).If an implementation is active, the method of this implementation is checked instead of authorization object S_RS_COMP.If either of the two mechanisms permits execution, the query can be executed.See the technical documentation on implementation.The return value of the method is a boolean value with two possible values:True (=X): Execution authorization exists: A standard check is not performed.False (=empty/initial): No execution authorization by BAdI. -> There is also a standard check for S_RS_COMP.Execution authorization for one of the two mechanisms is therefore sufficient to execute the query (OR logic).
This also guarantees that a user with a SAP_ALL profile can always execute the query, even if the BAdI is not active or returns "no authorization".
- SAP Managed Tags:
- BW (SAP Business Warehouse)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
12 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
General Splitter
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
GraphQL
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
2 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
14 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Vulnerabilities
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- SAP Cloud ALM and Identity Authentication Service (IAS) in Technology Blogs by SAP
- RAP Node Extensibility for Unmanaged BO in Technology Q&A
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- Real time access management with SAP BTP Kyma serverless workloads in Technology Blogs by SAP
| User | Count |
|---|---|
| 8 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |