Have you ever asked yourself one of the following questions:
- How can I secure my business data provided or consumed via Web Services running on the SAP NetWeaver platform?
- How can I integrate these services securely in a heterogeneous environment with the latest Microsoft .NET technology?
- Are there any best practices I should follow?
If yes, then this session at TechEd 07 is made for you! Here is the agenda of my 2 hours lecture:
- Web Services Interoperability - What's the catch?
- WS-Security Interoperability: A short primer
- Secure Web Services with SAP NetWeaver
- Secure Web Services with Microsoft .NET
- Live Demo: Building a secure interop scenario
- Summary
As you can see from the agenda, the session is split into two main parts:
- Part one will start with a short overview on Web Services Security (WS-Security) and interoperability in general and discuss the support for the WS-BPEL - SAP Developer Network (SDN) in both platforms, SAP NetWeaver and Microsoft .NET. It'll give you hands-on advise on how to use SAP NetWeaver Developer Studio and Microsoft Visual Studio 2005 (incl. the extensions for the Windows Communication Foundation, WCF) to design and deploy secure Web Services, along with code samples that are required to build an interoperable scenario.
- In part two of my session, I'll demonstrate the steps to build an interoperability scenario based on SAP NetWeaver and Microsoft .NET. The general setup looks like this:
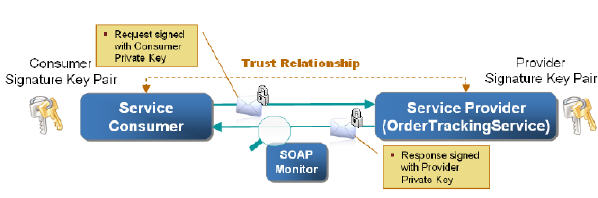
The Web Service provider in the scenario is hosted on SAP NetWeaver AS Java 7.0 and implements an interface that allows consumers to track the status of their orders which are uniquely identified by their id in the backend system. From a security perspective, the following threats have to be addressed:
- Unauthorized users could use the service to track the status of other user's orders
- A false service provider could send bogus responses
- The message content in transit could be changed by a third party, e.g. the order id in the request or the current processing status in the response
Therefore, both parties possess a cryptographic key pair which is used to digitally sign the messages and identify each other based on public key certificates. During the live demonstration, the requests and responses will be traced using a SOAP Monitor to visualize the secured message flow.
If you want to get familiar with security in Enterprise SOA, I recommend the following readings for a brief overview:
For information regarding WS-Security interoperability with .NET 2.0 and the Web Services Enhancement (WSE), which is the predecessor of the Windows Communication Foundation (WCF) that is the subject matter of this session, please find the following articles on SDN:
As a mixture of lecture and demonstration, this session will give you practical, hands-on advice on secure and interoperable programming, including techniques for troubleshooting and debugging in an SOA environment. Hope to see you at TechEd!
